Attacker uses an Office 365 site to steal user credentials
2 min. read
Updated on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team Read more
Key notes
- Hackers set up an Office 365 login page to steal users' Microsoft credentials.
- Remote workers using VPNs to securely connect to company networks were a target for the email phishing attacks.
- You can always visit our Office 365 hub for relevant tips, guides, and news.
- Would you like to optimize your company's virtual private network security? Check out the VPN page for practical recommendations and tools!

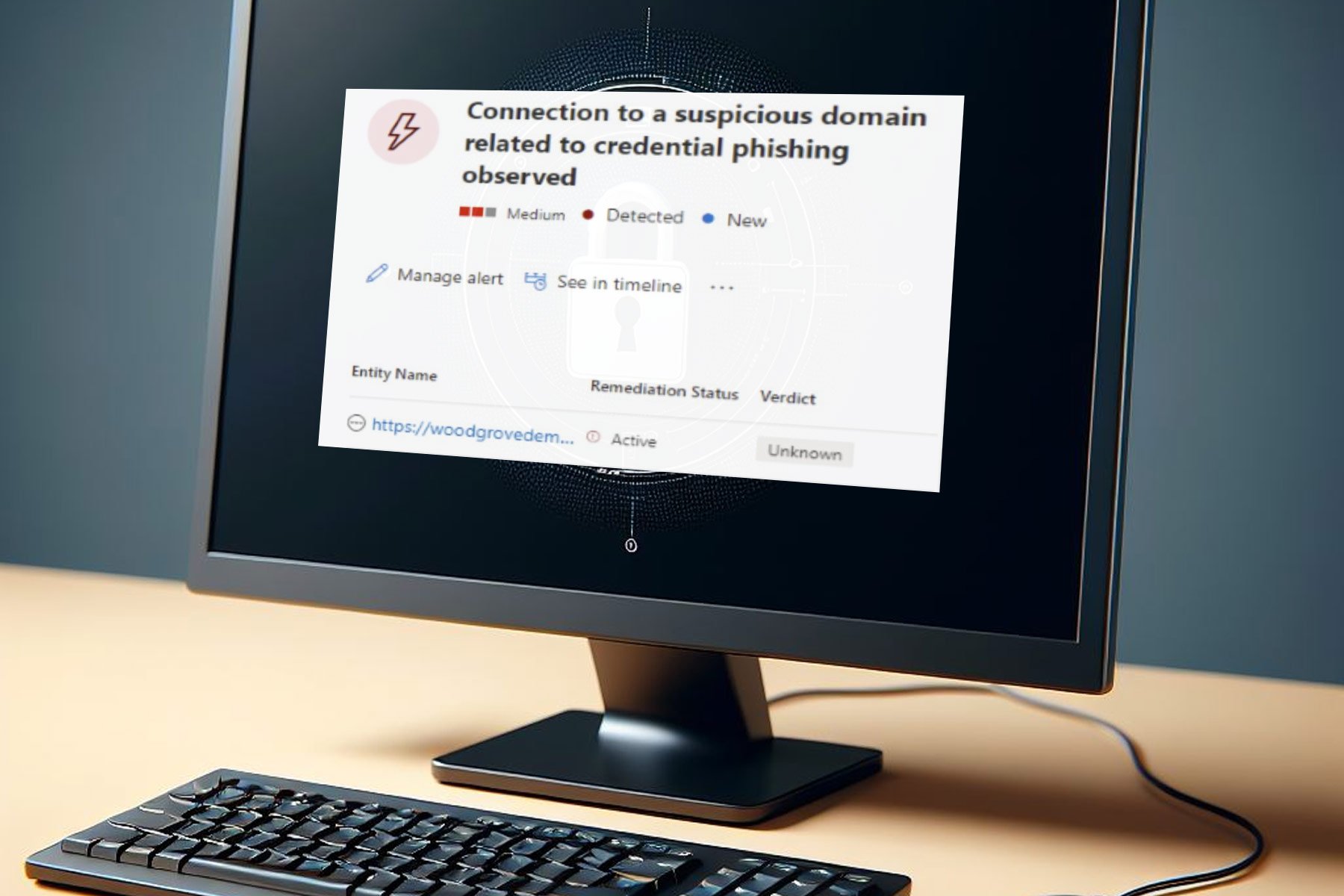
Email phishing may be one of the oldest tricks up the sleeves of any hacker, but it hasn’t run out of fashion yet. For example, a malicious player recently set up an Office 365 phishing base to fraudulently obtain usercredentials.
Pretty much any platform that requires user authentication to allow access can be a target for phishing.
Also, anyone can be a victim, from SaaS customers to OneDrive users.
Malicious actors created an Office 365 email phishing site
Hackers sent remote workers malicious email links to fraudulently capture their user credentials, according to an Abnormal Security report.
For starters, they took advantage of the fact that many organizations are currently setting up VPNs to secure internet connections for their work-at-home employees.
The target receives an email disguised as official communication from their employer’s IT department in this phishing attempt.
Next, the target clicks the link in the email, which leads to a VPN configuration that the attacker set up. In the end, the employee lands on a login page hosted on the Office 365 platform.
Since the site looks almost 100% the same as the genuine one, the remote worker, sadly, falls for it.
Therefore, the victim supplies their login details oblivious of the fact that they’re not signing into their employer’s official portal. So, just like that, the bad actor makes away with the target’s Microsoft credentials.
The attack impersonates a notification email from the IT support at the recipients’ company. The sender email address is spoofed to impersonate the domain of the targets’ respective organizations. The link provided in the email allegedly directs to a new VPN configuration for home access. Though the link appears to be related to the target’s company, the hyperlink actually directs to an Office 365 credential phishing website.
Here are tips for optimizing your email security:
- User discretion: Always check the URL of any web form that requires your user credentials.
- Email security: Use email scanning anti-malware.
- Windows updates: Always install Windows security updates.
- Microsoft’s security tools: This can elevate your threat detection capabilities.
Have you ever been a victim of email phishing? Feel free to share your experience in the comments section below.
[wl_navigator]