Microsoft removes SMB1 from Windows 10 by default following Wannacry attack
2 min. read
Published on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team Read more
Microsoft recently decided to remove the SMB1 networking protocol from Windows 10 by default. This change is part of the tech giant’s multi-year security plan aimed at reducing the attack surface of the OS.
The first OS version to feature this change is build 16226. However the change only affects clean installations of Windows, and not upgrades.
Here are more details about the removal of SMB1:
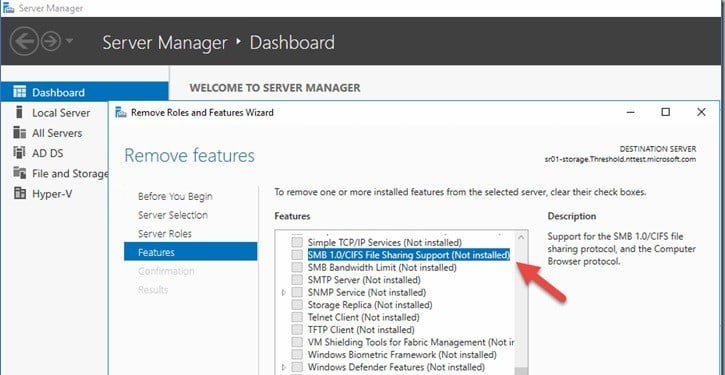
- All Home and Professional editions now have the SMB1 server component uninstalled by default. The SMB1 client remains installed. This means you can connect to devices from Windows 10 using SMB1, but nothing can connect to Windows 10 using SMB1.
- Microsoft still recommend you uninstall SMB1 even if you are not using it. The company is also considering uninstalling the SMB1 client in a later feature update of Windows 10 if it detect that you are not using it.
- All Enterprise and Education editions have SMB1 totally uninstalled by default.
- The removal of SMB1 means the removal of the legacy Computer Browser service.
Quick reminder: What is SMB1?
SMB1 is an application-layer network protocol developed by Microsoft more than 30 years ago. The protocol is mainly used for offering shared access to files, printers, serial ports and other network tools between nodes on a network.
At the time the tech giant created this protocol, the world was a much safer place. As malware appeared, SMB1 became some sort of an Achilles’s heel for computers, making them extremely vulnerable to threats. It is worth mentioning that the SMB1 server software was recently successfully exploited by the WannaCry ransomware.
Microsoft explains that if your clients use SMB1, they become sitting ducks for man-in-the-middle attacks.
[…] if your clients use SMB1, then a man-in-the-middle can tell your client to ignore all the above. All they need to do is block SMB2+ on themselves and answer to your server’s name or IP. Your client will happily derp away on SMB1 and share all its darkest secrets unless you required encryption on that share to prevent SMB1 in the first place. This is not theoretical – we’ve seen it.
If you’re still relying on SMB1, stop using it right now. For more information on how to disable SMB1, follow the instructions available on Microsoft’s support page.
RELATED STORIES YOU NEED TO CHECK OUT:
- WannaCry’s creators threaten to release more malware to Windows 10
- StoneDrill is the newest wiper malware to hit PCs