T-RAT 2.0 Telegram-controlled RAT, the latest virus threat
4 min. read
Updated on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team. Read more
Key notes
- T-RAT 2.0 is a new version of the dangerous T-RAT Remote Access Trojan.
- The malware can be controlled remotely through a Telegram channel.
- Reportedly, the T-RAT malware will retrieve passwords, record webcam, and keystrokes.
- Protect yourself from this virus and other malware by using a strong antivirus.

T-RAT 2.0, a new Remote Access Trojan (RAT), is being advertised on Russian hacking forums, as security experts recently discovered.
Reportedly, the RAT can be purchased for merely $45, but that’s not what makes it shine. Such malware will completely ruin devices, steal your data and compromise important accounts.
As opposed to other similar services, T RAT 2.0 enables malevolent agents to control compromised systems through Telegram channels, instead of web administration panels.
What is T-RAT 2.0?
T-RAT 2.0 is simply one of the latest Remote Access Trojans on the market. How this type of malware works is granting the attacker remote access to your machine.
What hackers can do from that point strictly depends on their skills and the capabilities of the RAT as well.
Some RATs are designed just to mess with the targets (e.g. open their CD tray, turn off their monitor, disable their input devices), but other ones (T-RAT included) are downright evil.
Apparently, here’s what T-RAT 2.0 can do to your system, once it infects it:
- Retrieve cookies and passwords from your browser
- Grant the attacker full access to your file system
- Perform audio recordings (requires an audio input device such as a microphone)
- Log your keystrokes
- Disable your Taskbar
- Use your webcam to perform video recordings or take pictures
- Fetch clipboard content
- Snap screenshots of your current view
- Disable your Task Manager
- Hijack transactions for several services, including Ripple, Dogecoin, Qiwi, and Yandex.Money
- Execute CMD & PowerShell commands
- Restrict your access to various websites and services
- Forcefully terminate processes on your computer
- Use RDP and/or VNC to perform additional remote control operations
More so, it’s compatible with most Chromium-based browsers (v80 and up), and its Stealer component supports the following apps:
- FileZilla XML
- NordVPN
- Discord
Previous RATs also used Telegram as C&C
Although the thought of controlling a RAT through Telegram seems novel, it’s quite far from that. The crude reality is that it’s completely possible, and it’s happening right now.
In the past few years, much similar malware relied on Telegram as their command & control center. Some of them include:
- Telegram-RAT
- HeroRAT
- TeleRAT
- RATAttack
Having a Telegram C&C for a RAT is appealing for most hackers, as it can grant them access to infected systems, regardless of location.
The fact that they no longer need desktops or laptops for attacks provides them with a new level of freedom and mobility.
How do I protect myself from T-RAT 2.0?
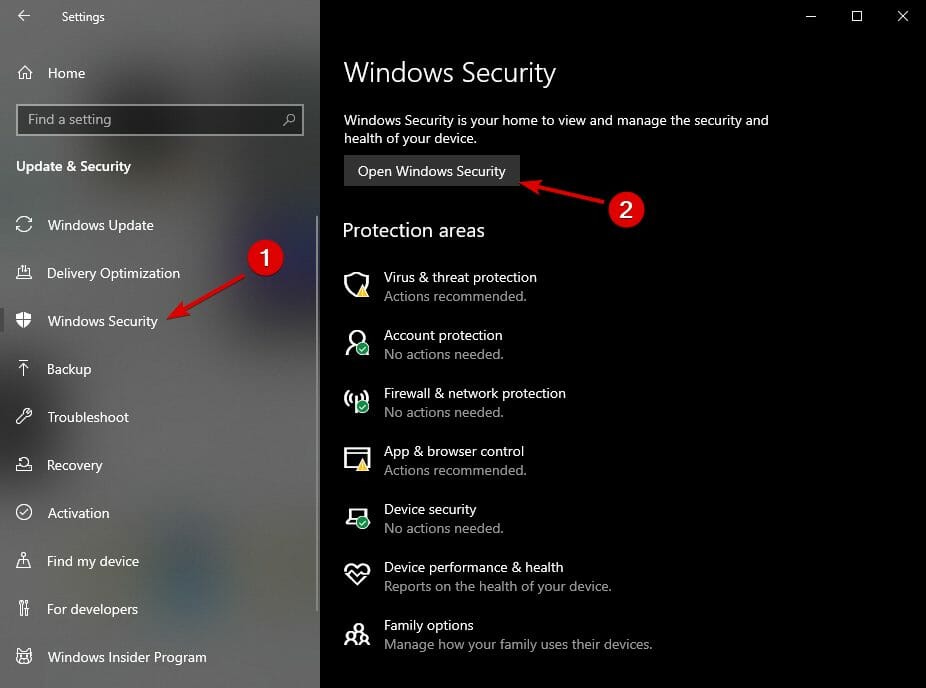
- Go to Settings.
- Choose Windows Security, then Open Windows Security.
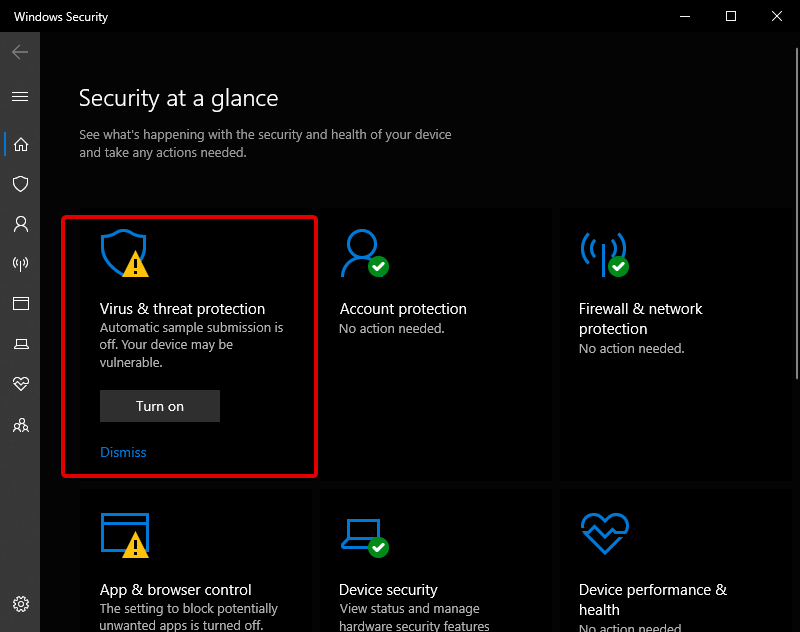
- Select Virus & threat protection, then scan options
- Now, select Full Scan and click on Scan Now.
- Let Windows Defender finish scanning your PC.
That’s how you scan your PC for malware with the in-built Windows Defender.
If you want to protect yourself from the T-RAT 2.0 malware, adware, spyware and many other harmful software that is trying to infect your PC and steal your data, you need a strong defense.
Additionally, we’d like to mention that a strong antivirus needs multilayered protection and advanced AI to actively search your PC for emerging threats, adapt to them, and monitor suspicious activity.
The software works with multiple platforms, so you can protect your phone, tabled, laptop, or PC easily.
Besides having strong protection, the program also keeps your identity and sensible data safe while you’re browsing the internet, or doing online payments of any kind.

ESET HOME Security Essential
ESET HOME Security Essential is the world-leading antivirus software that will keep any dangerous files away from you.That’s about it for this article today. The Trojan virus is a serious issue that cannot be neglected, and this latest addition is even more dangerous than before.
We suggest checking out our thorough list of the best antivirus software with unlimited validity and choosing one that suits your needs.
How do you protect your Windows PC against threats such as T-RAT 2.0? Share your opinion with us in the comments section below.




User forum
0 messages