The OOBE shortcuts are no longer a secret, but there is more to it
Here we will explore Hotkeys mentioned in the Enderman video
3 min. read
Updated on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team Read more
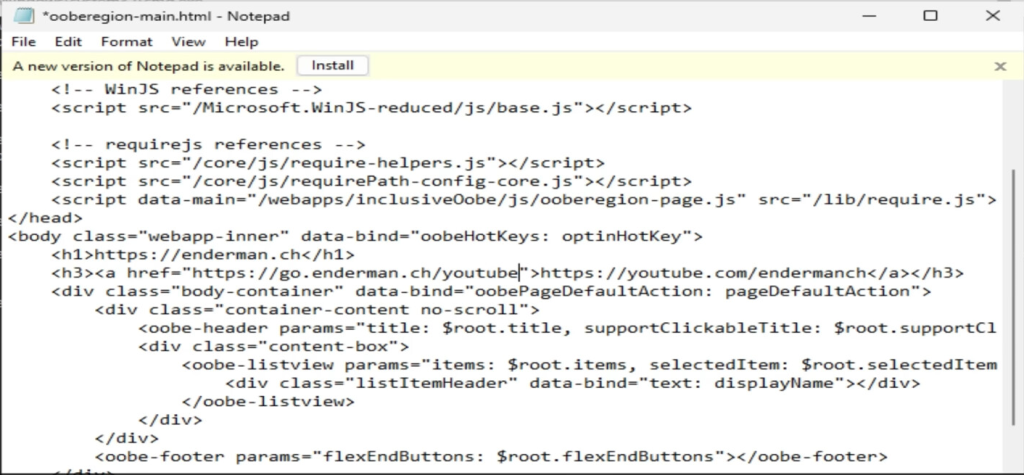
Enderman, the software engineer and security researcher, recently published his findings on the Windows 11 OOBE (Out of Box Experience) source code in a YouTube video. The OOBE in the video is for the first Windows 11 24H2 build, 26040.
He mentioned that Windows 11 build 26040 brought us the old installer back, which was first featured with Windows 10 build 9780.
On the setup page, while selecting the setup option, there is a Previous Version of Setup option, which is confusing as Microsoft has labeled the old installer as the previous version, which is misleading. The reason is that both installers co-existed for some time and are suitable for different purposes.
Enderman couldn’t get the version to work, so he installed Windows 11 build 26052 (24H2) and discovered a few hidden functionalities inside the OOBE.
Most Windows users know that we can bring up Command Prompt by pressing Shift + F10 keys to bypass the need for an internet connection or a Microsoft account while in the OOBE. Let’s find out what new things he discovered:
- Audit mode
- Press the hotkey – Ctrl + Shift + F3 during OOBE to reboot your computer into Audit mode.
- Can access the Audit mode inside the Sysprep tool.
- This mode exists parallel to the OOBE mode so that you can invoke it via OOBE.
- It is also called default boot.
- Allows you to configure the system before deployment, meaning you can change the Windows system image.
- And, by generalizing the image and distributing of a custom install.wim, pre-configuring for a large number of devices becomes scalable and quick.
- OOBE is a web application
- It is run using WWAHost.exe, which is a Windows Web Application Host.
- When checked in the Task Manager, under Processes, open the OOBE process; it is called CloudExperience Host and is located in C:\Windows\SystemApps
- In further checking the folder, he found the app uses the plain old HTML/CSS/JS stack and to be specific WinJS framework is the choice.
- You can redesign and change the text on OOBE or control anything, which opens up many modding capabilities.
- Provisioning menu
- Press the Windows key five times in the OOBE, you will get provisioning menu.
- Allows you to change advanced installation options, such as installing an app or configuring or resetting a device with Autopilot.
- Developer console
- Press Ctrl + Shift + J to open a developer console in a production environment inside Windows 11 OOBE.
- The console supports executing JavaScript code & a set of in-built commands.
- Allows multiline input and to execute it you can press Ctrl + Enter.
- To traverse through history, press Ctrl + Up and Ctrl + Down.
- Allows you to edit an app, debug the console, and then make changes to OEM EULA.
- Windows Autopilot diagnostics
- Press Ctrl + Shift + D to access the Diagnostics Page during OOBE.
- Allows you to view troubleshooting details about the Autopilot provisioning process.
This all seems too exciting and fun to play with; however, ability to customize OOBE on Windows 11 setup can open doors for cyber criminals as it would be easy for them to infect the Windows image before deployment.
Also, we at WR, always advise that no one should make changes to the original ISO image of an operating system, as this could harm their device and may make it susceptible to harmful things.
What do you think about it? Share your thoughts in the matter in the comments section below and let’s start a conversation.