Malware attacks to affect Windows PCs through faulty drivers
3 min. read
Published on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team. Read more

Security researchers found new vulnerabilities in more than 40 drivers that have been certified by Microsoft.
The problem is in the driver code that enables communication between the OS kernel and the hardware, providing a higher permission level than a normal user or an administrator.
The driver vulnerabilities could affect millions
The list of hardware manufacturers affected include huge companies like Intel, Nvidia, Huawei, Toshiba, and Asus. Here’s how the cybersecurity team at Eclypsium, who found the vulnerabilities, describe them:
All these vulnerabilities allow the driver to act as a proxy to perform highly privileged access to the hardware resources, such as read and write access to processor and chipset I/O space, Model Specific Registers (MSR), Control Registers (CR), Debug Registers (DR), physical memory and kernel virtual memory. This is a privilege escalation as it can move an attacker from user mode (Ring 3) to OS kernel mode (Ring 0). The concept of protection rings is summarized in the image below, where each inward ring is granted progressively more privilege. It is important to note that even Administrators operate at Ring 3 (and no deeper), alongside other users. Access to the kernel can not only give an attacker the most privileged access available to the operating system, it can also grant access to the hardware and firmware interfaces with even higher privileges such as the system BIOS firmware.
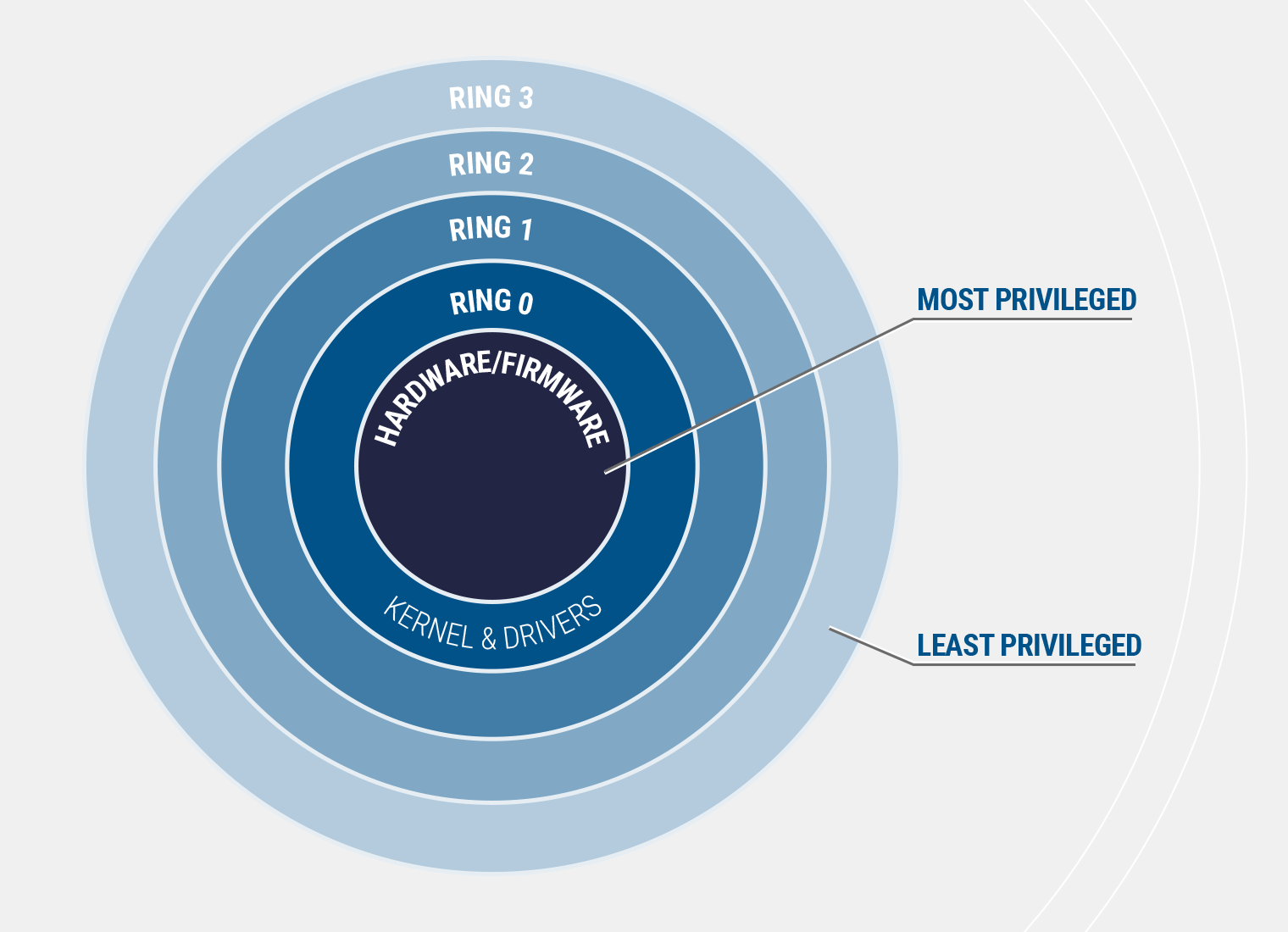
This is the case with BIOS and UEFI firmware that once affected, can’t be repaired by a OS reinstall.
All versions of Windows are affected
It’s worth mentioning that over 40 drivers were affected, and the issue applies to all versions of Windows, not just Windows 10.
Microsoft is strongly advising its customers to use Windows Defender Application Control to block unknown software and to turn on memory integrity for capable devices in Windows Security.
Here’s the full list of affected vendors:
- ASRock
- ASUSTeK Computer
- ATI Technologies (AMD)
- Biostar
- EVGA
- Getac
- GIGABYTE
- Huawei
- Insyde
- Intel
- Micro-Star International (MSI)
- NVIDIA
- Phoenix Technologies
- Realtek Semiconductor
- SuperMicro
- Toshiba
Some of them have already deployed fixes, but others are still under embargo.
To keep your system safe, be sure to regularly scan for outdated drivers and install the latest driver fixes from the aforementioned manufacturers.
To help you, we’ve prepared a guide on how to update outdated drivers, so be sure to check it out.
READ ALSO:
- How to: Update graphics driver on Windows 10
- 9 best antivirus software with encryption to secure your data
- Microsoft Defender ATP is the new cross-platform security offering from Microsoft
User forum
0 messages