How to download KB5004945 and fix the PrintNightmare vulnerability
4 min. read
Updated on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team. Read more
Key notes
- The tech company issued an emergency patch to address the PrintNightmare security situation.
- Attackers taking advantage of the vulnerability can remotely run code with system-level privileges.
- The software is available for multiple Windows versions that were affected, including the outdated Windows 7.
- Microsoft is advising users to install these security patches and improve their online protection.

The Redmond-based tech company has released a critical emergency patch to fix a problem with the Windows Print Spooler service.
This vulnerability in question is known as PrintNightmare and it was under constant exploit from malicious entities.
When exploited, it allowed attackers to install software; view, alter, delete data; or even create new accounts with full user rights. However, user reports are indicating that the patch doesn’t really fix the entire issue.
KB5004945 is a new security update that has been released for any Windows version newer than v2004.
Users who have Windows 10 version 1909 will first get the KB5004946 patch, and then the PrintNightmare patch will also be installed.
The patch is available for multiple Windows versions
The above-mentioned security patch is now available for quite a few versions of Windows 10, Windows 8.1, Windows Server 2019, Windows Server 2021 R2, Windows Server 2008, and Windows RT 8.1.
If you are a Windows 7 user, this patch is also available for you, even though the operating system is out of support.
The only OS versions for which this patch is currently unavailable are Windows 10 version 1607, Windows Server 2016, and Windows Server 2012, but Microsoft stated that they are working on it.
This whole situation seems to be pretty serious, considering that the software is also addressed to Windows 7, this fact being an indicator of the severity of the problem.
Even more, knowing the Windows 7 OS has been out of support ever since January 14, 2020.
Information about this also circulated on social media, where security researchers said that Microsoft’s patch only addresses one element of the vulnerability.
What’s disconcerting is that malicious third parties can still target these vulnerabilities. Word on the internet is that there are ways for people to completely bypass Microsoft’s patch and target vulnerable systems.
This is achieved via remote code execution in addition to the previous local privilege execution.
As you can see, Microsoft is taking this threat very seriously, so we think that you should too.
Update to Windows 10 Version 20H2 & 21H1
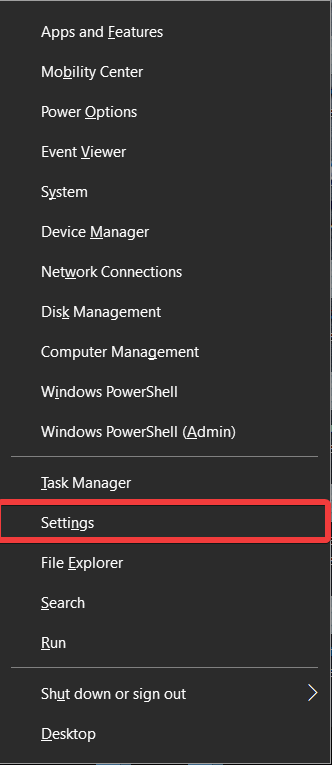
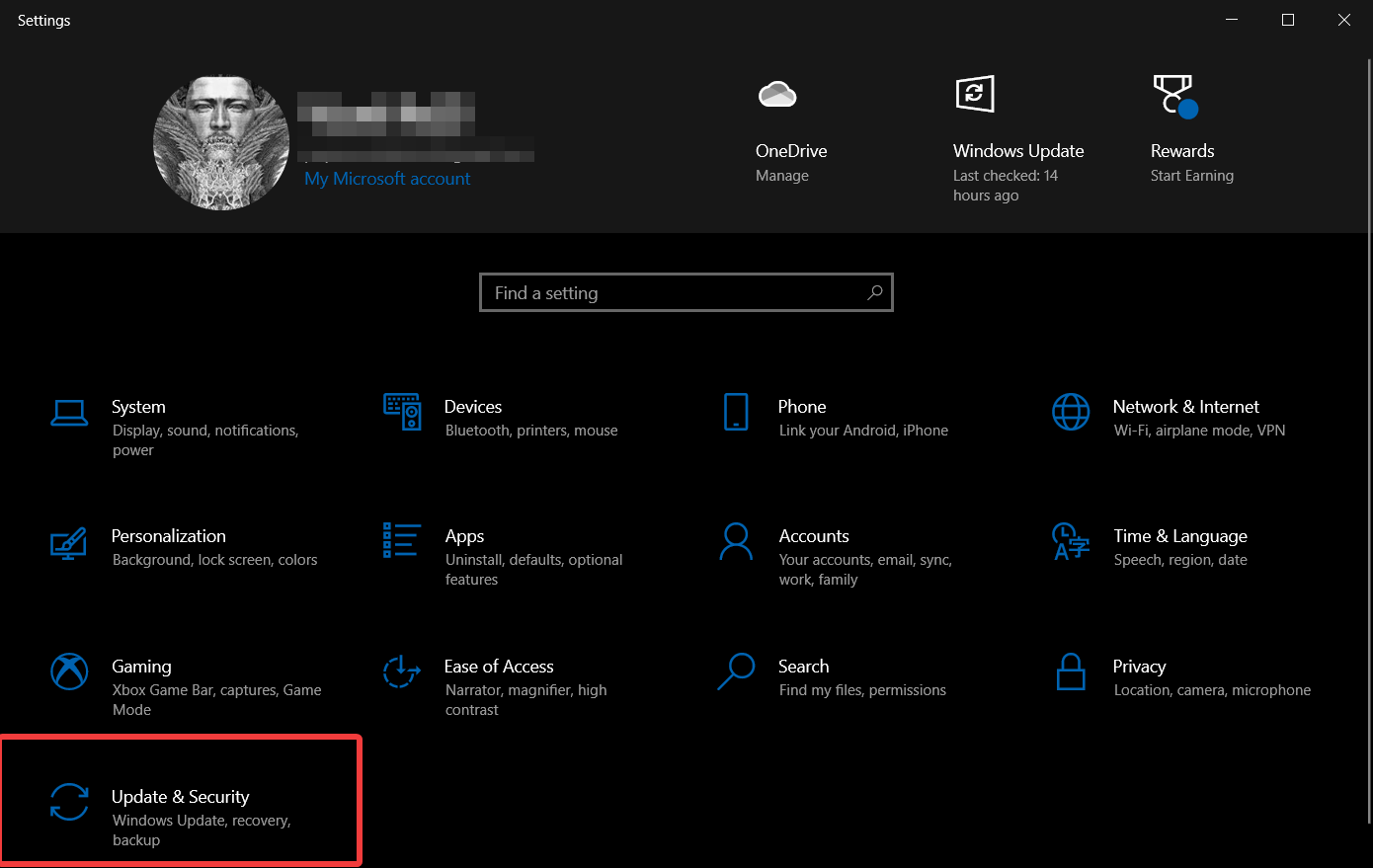
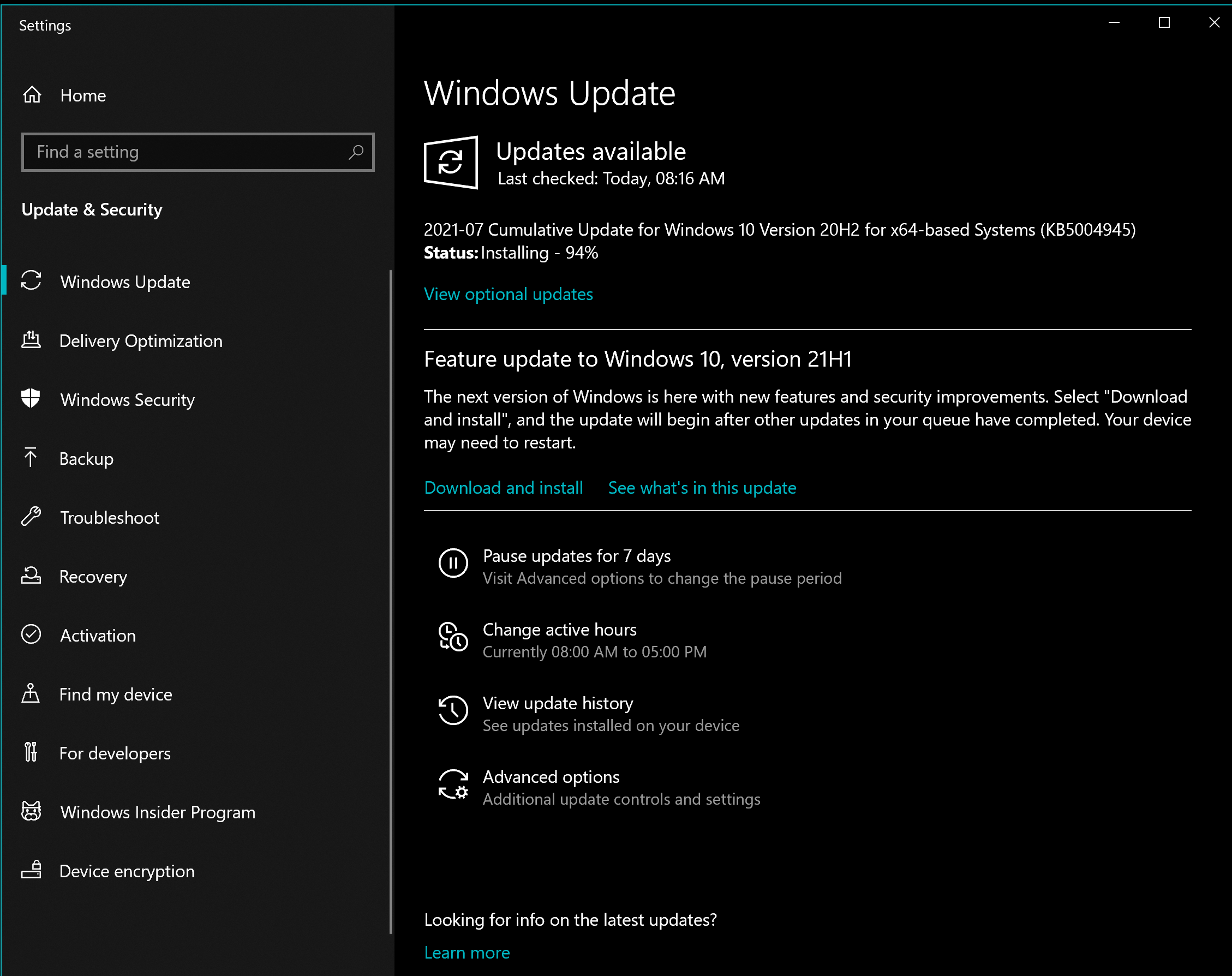
1. Open Windows Update
- Press the Win + X key combination by using your keyboard.
- Choose Settings from the pop-up menu.
- Navigate to Updates & Security.
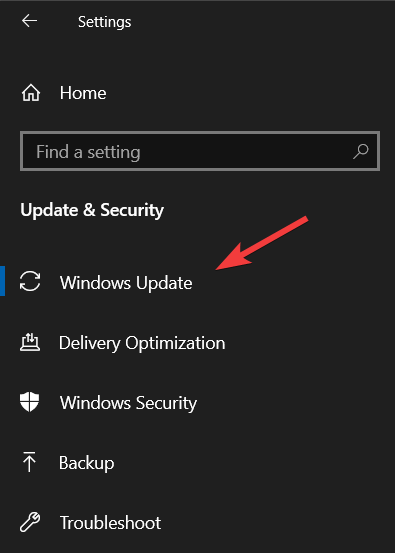
- Choose Windows Update.
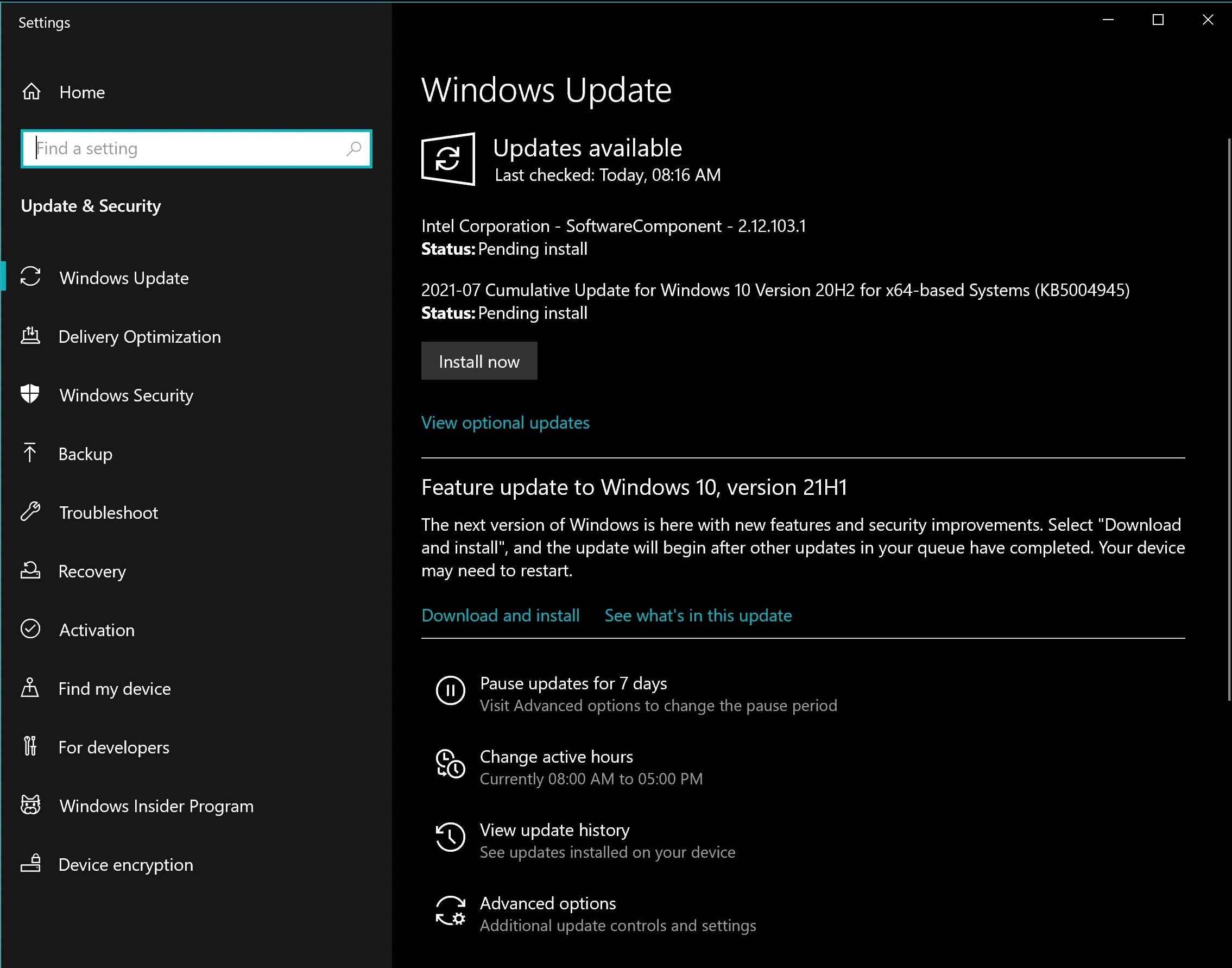
2. Perform the update
- Open the Windows Update window and click Check for Updates.
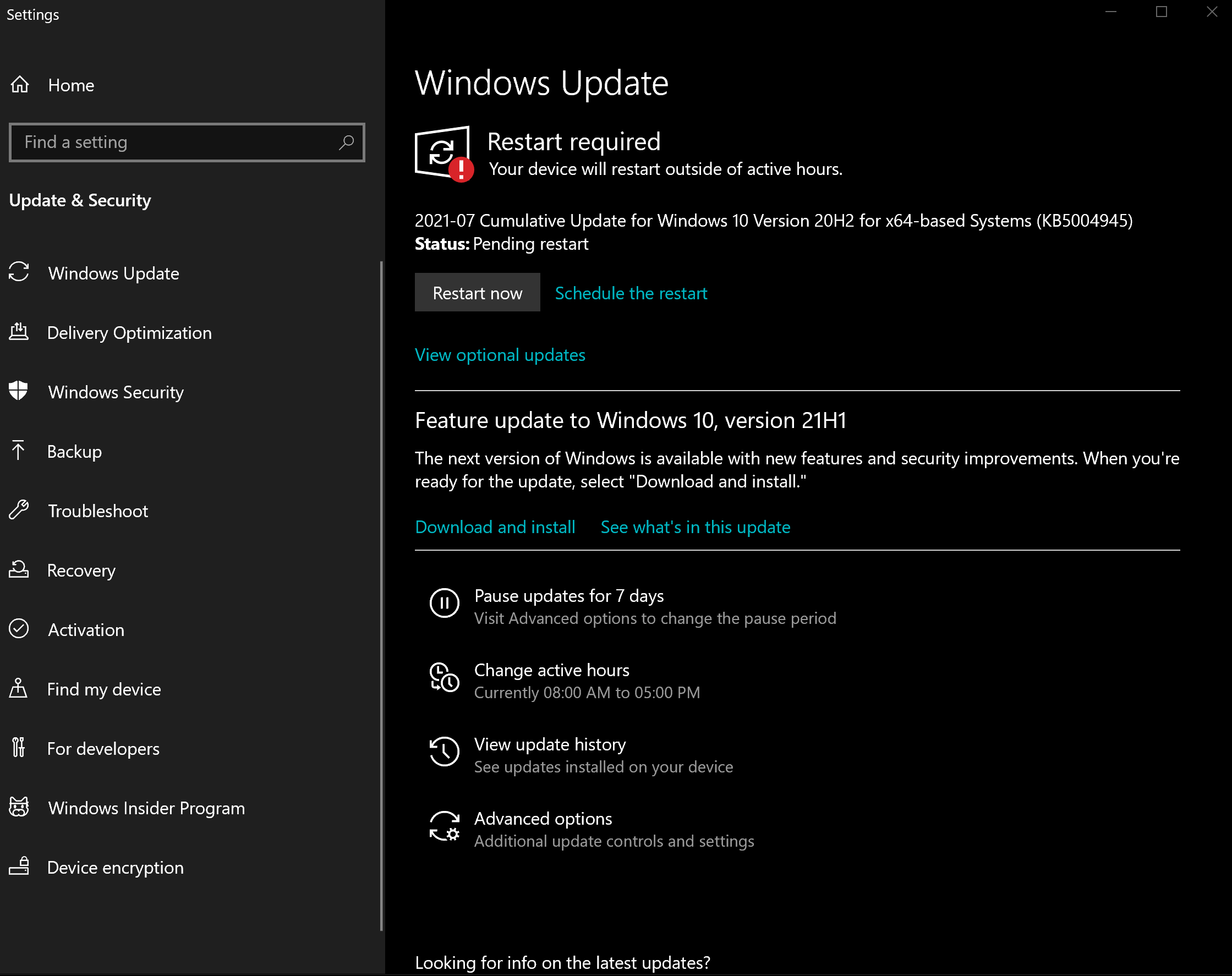
- Press the Install now button to update to version 20H2 of Windows 10, thus getting the KB5004945 patch.
- Wait for the installation process to complete.
- Click Restart now.
How can I fix the Print Spooler PrintNightmare without updating?
Even though it is not recommended that you follow this path, it might be useful in the case of some users, so here are the required steps to successfully stop the Print Spooler service:
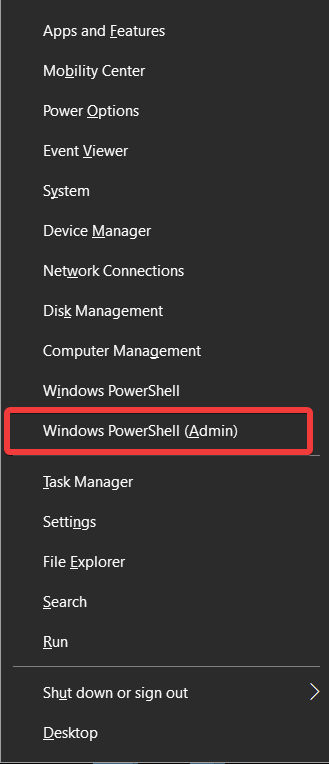
- Press Win+X keys to open the sub-menu.
- Choose Windows PowerShell (Admin).
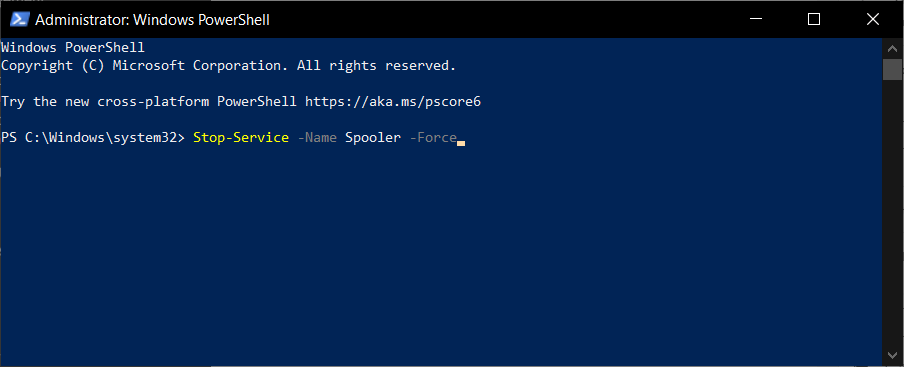
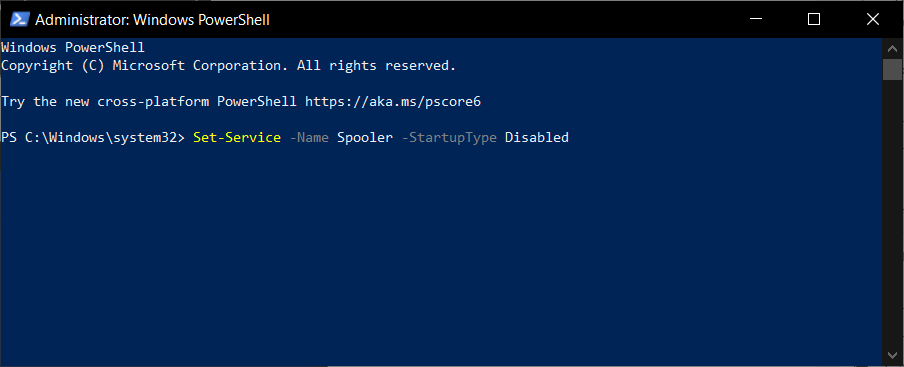
- In the command prompt, type the following command and run it by pressing Enter:
Stop-Service -Name Spooler -Force - Disable it entirely by using the following command:
Set-Service -Name Spooler -StartupType Disabled - Press Enter to run the command.
Performing these steps will ensure that Windows will firstly disable the corrupted service, and the second command will stop it from running at the startup of your system.
If for any reason, you will want to revert these changes at some point, you can run the following commands:
- To start the service again:
Start-Service -Name Spooler - To allow it to run at Windows startup:
-Name Spooler -StartupType Automatic
Microsoft now urges users to install this security update and make the best efforts to keep their private content inaccessible to external sources.
Online safety should be one of the first things on our minds, seeing how these threats can greatly impact individuals and companies alike.
What extra security measures are you taking, to protect your data? Let us know in the comments section below.


User forum
0 messages