17000 Microsoft Exchange servers in Germany exposed online are at risk
The German national cybersecurity authority warned about it
3 min. read
Published on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team Read more

Recently, the German national cybersecurity authority alerted that more than 17,000 Microsoft Exchange servers in Germany are vulnerable to one or more critical security vulnerabilities.
As per the German Federal Office for Information Security (BSI), approximately 45000 Microsoft Exchange servers in Germany have Outlook Web Access (OWA) enabled and are accessible via the Internet.
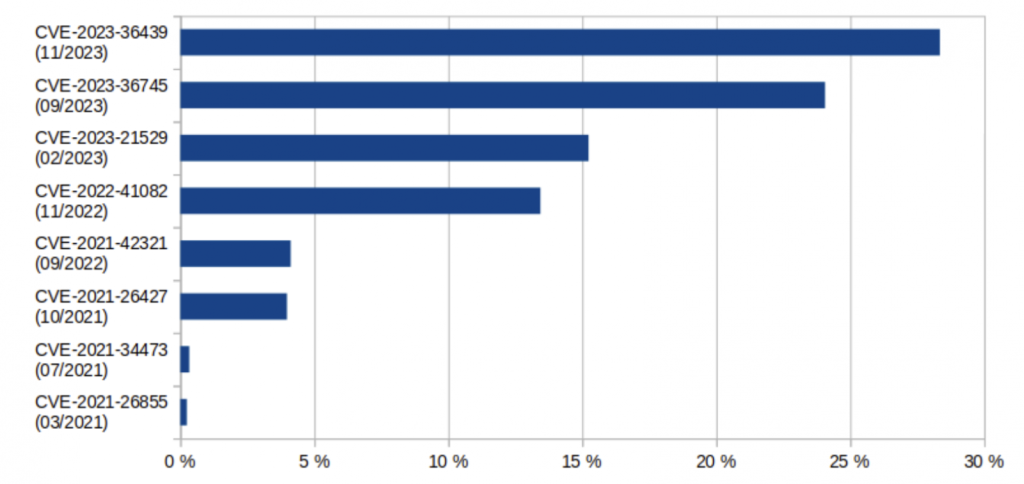
Of these, 12% of servers have outdated versions of Exchange 2010 and 2013 and have not received security updates since October 2020 and April 2023, respectively.
If we talk about the newer versions, Exchange 2016 and 2019, 28% of these have not received any security update for four months and are vulnerable to one or more critical security flaws, which could be exploited in the prevalent remote code execution attacks.
In its report, the BSI warned:
Overall, at least 37% of Exchange servers in Germany (and in many cases also the networks behind them) are severely vulnerable. This corresponds to approx. 17,000 systems. In particular, many schools and colleges, clinics, doctor’s offices, nursing services and other medical institutions, lawyers and tax consultants, local governments, and medium-sized companies are affected.
As early as 2021, the BSI warned several times against the active exploitation of critical vulnerabilities in Microsoft Exchange and temporarily called the IT threat situation ‘red.’ Nevertheless, the situation has not improved since then, as many Exchange server operators continue to act very carelessly and do not release available security updates in a timely manner.
So, BSI recommended that admins of these unpatched servers must also keep the Exchange versions up to date and install all the security updates as soon as they are available.
The admins should also inspect whether all their systems are on the latest Microsoft Exchange patch level and whether the March security update is installed correctly on their machines. Here are the details of the version available:
- Exchange Server 2019 CU14 Mar24SU (Build number 15.2.1544.9)
- Exchange Server 2019 CU13 Mar24SU (build number 15.2.1258.32)
- Exchange Server 2016 CU23 Mar24SU (build number 15.1.2507.37)
The BSI urged restricting access to web-based Exchange server series like Outlook Web Access to trusted source IP addresses or promoting using them only via a reliable VPN.
In addition to this, the BSI also mentioned that to prevent being exploited due to the CVE-2024-21410 critical privilege escalation vulnerability mentioned by Microsoft, the admins should use Extended Protection on all Exchange servers using a PowerShell script.
Microsoft has now automatically enabled the Extended Protection on Exchange Servers after the February 2024 H1 Cumulative Update (CU14). This step was taken when Shadowserver, a threat-monitoring service, alerted that 28,500 Microsoft Exchange servers were vulnerable to ongoing CVE-2024-21410 attacks.
What are your thoughts on the matter? Share your opinions with our readers in the comments section below.