Device Bound Session Credentials, a new Chrome feature to protect your cookies and reduce data theft
It will bind authentication sessions to the device
3 min. read
Published on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team. Read more
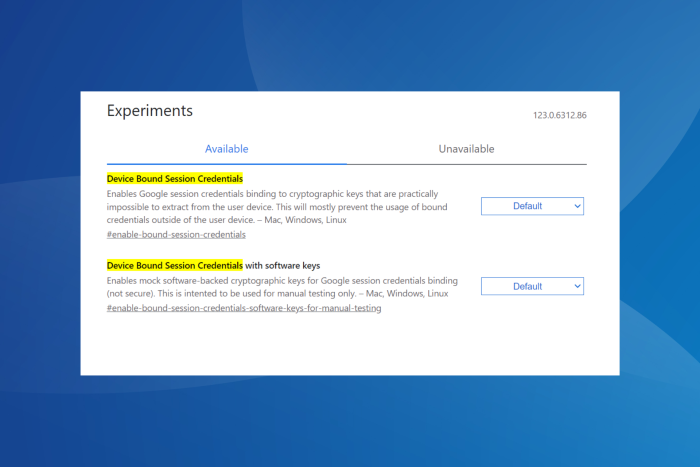
Recently, Google Chrome brought in Device Bound Session Credentials (DBSC), a feature aimed at reducing cookie theft, a common attack type that employs specialized malware. The malware, once on the PC, gains access to the cookies and sends them to remote servers.
For the unversed, cookies are small pieces of data saved by websites to store your browsing information and preferences. This way, you get a familiar experience when visiting the website the next time.
These cookies can also be used by threat attackers to gain unauthorized access to our accounts. Besides, your antivirus software is usually ineffective against such malware, given the latter has the same set of permissions as the former. This is where DBSC comes into the picture!
About Device Bound Session Credentials (DBSC) in Google Chrome
DBSC, an open-source project by Google Chrome, is available on GitHub. Google wants it to become the new web standard.
The official blog post describes Device Bound Session Credentials as a feature that will generate a new key for each browsing session and link it locally to the device. For this, DBSC will utilize the built-in TPM (Trusted Platform Module) functionality. The blog post reads,
By binding authentication sessions to the device, DBSC aims to disrupt the cookie theft industry since exfiltrating these cookies will no longer have any value. We think this will substantially reduce the success rate of cookie theft malware. Attackers would be forced to act locally on the device, which makes on-device detection and cleanup more effective, both for anti-virus software as well as for enterprise managed devices.
In a bid to preserve user privacy and reduce instances of cookie theft, DBSC prevents websites from correlating or tracking data. It also allows users to delete created keys from within the browser.
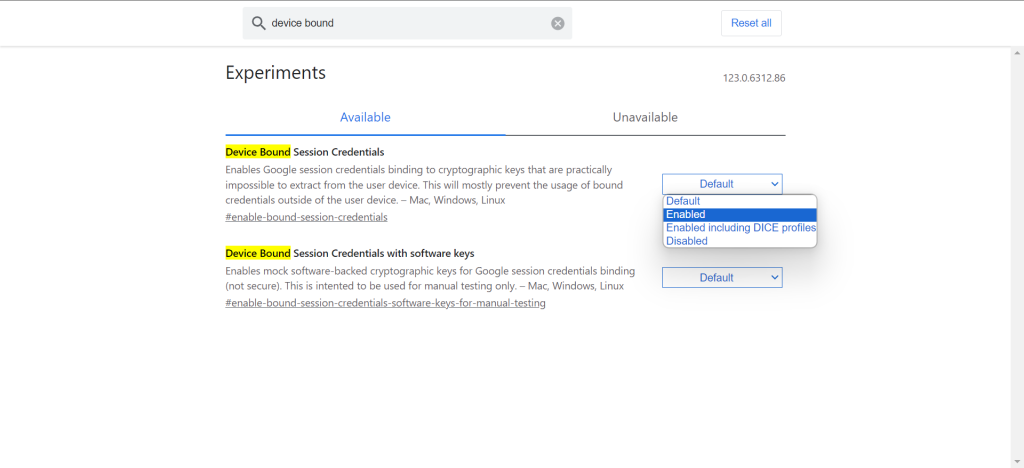
Since it’s currently in the testing stage, you will find Device Bound Session Credentials listed under flags on the following URL in Google Chrome: chrome://flags/
To enable it on Chrome, search for Device Bound Session Credentials in flags and then select Enabled from the dropdown menu.
Such features are often introduced as experimental and then based on feedback and, after subsequent refining, released for all!
Of late, Chrome has been extensively working on improving its security infrastructure, from home network protection in Chrome to upgrades like Windows Hello as an authentication method.
Such measures may help put a stop to the exponential rise in cyberattacks!
What do you think about DBSC in Chrome? Share with us in the comments section.
User forum
0 messages