Microsoft requiring stronger passwords in response to LinkedIn hack and 10 million attacks each day
4 min. read
Published on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team. Read more

Security and passwords. Passwords and security. As large enterprises, educational institutes, small businesses, and everyday consumers are exposed to increasing nefarious online activity, the need for stronger passwords and better security measures are becoming a feature necessity from software and content providers.
In the wake of software provider LinkedIn’s 117 million usernames and passwords leak, the Azure Directory Team is aiding security with measures IT admins can use to better secure their user’s passwords, privacy, and sensitive information.
Reaching out to Robyn Hicock and Alex Weinert of the Azure Identity Protection division, the Azure Directory team can now offer IT admins a walkthrough of the best practices regarding password security. According to Hicock and Weinert the following:
- Password length requirements
- Password “complexity” requirements
- Regular, periodic password expiration
These may seem like no-brainers in the war against password hacking, but in fact have offered an easier way for hackers to obtain sensitive information. In separate whitepaper write ups title Robyn’s paper, Hicock explains the predictability of users when encountered with aforementioned security requirements and how hackers prey on those tendencies.
To counter those measures, the Azure Directory team uses a combined practice of dynamically banning common passwords and smart password lockout.
The details of dynamically banning common passwords include:
When it comes to big breach lists, cybercriminals and the Azure AD Identity Protection team have something in common – we both analyze the passwords that are being used most commonly. Bad guys use this data to inform their attacks – whether building a rainbow table or trying to brute force accounts by trying popular passwords against them. What *we* do with the data is prevent you from having a password anywhere near the current attack list, so those attacks won’t work.
As I mentioned in my last blog and the latest Microsoft Security Incident Report, we see more than 10M accounts attacked daily, so we have a lot of data about which passwords are in play in those attacks. We use this data to maintain a dynamically updated banned password list.
We then use that list to prevent you from selecting a commonly used password or one that is similar. This service is already live in the Microsoft Account Service and in private preview in Azure AD. Over the next few months, we will roll it out across all 10m+ Azure AD tenants.
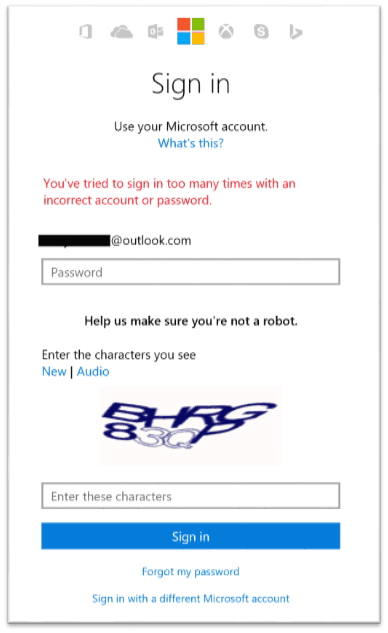
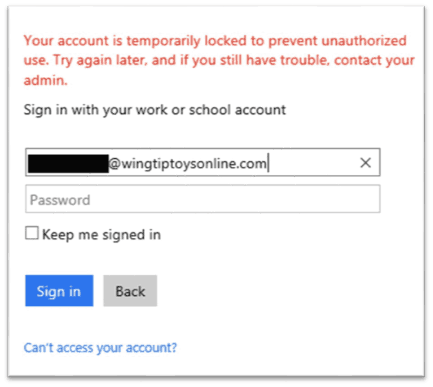
As for smart password lockout, many online consumers may have already been exposed to the practice in some form or another by companies utilizing two-factor authentication.
Of course, you already know that when our security system detects a bad guy trying to guess your password online, we will lock out the account. What you probably don’t know is that we do lots of work to make sure that they only lock themselves out!
Our systems are designed for determining the risk associated with a specific login session. Using this, we can apply lockout semantics only to the folks who aren’t you. The only way *you* get locked out is if someone is guessing your passwords on your own machine or network.
The Azure Directory method of using and smart password lockout has statistically lead to over 50% of hackers being kept away from business or user information.

Obviously, more methods can be implemented on top of or in connection with dynamically banning passwords or smart password lockout, but using the two practices should help any company get a good footing against online password hacks. Let us know in the comments how you think companies like Microsoft can enhance security, and what steps you’re taking yourself to make your information and systems more secure.




User forum
0 messages