BitLocker Not Saving Key to AD: How to Force it
If your key isn't being saved, make a couple of changes to registry
2 min. read
Updated on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team Read more
Key notes
- To save your key, first, you need to make a couple of changes to the registry.
- Using the command line, you can force your key to be saved properly.
BitLocker is a built-in full disk encryption software available on Windows, but sometimes Bitlocker is not saving key to AD.
This can be an issue and make your recovery process almost impossible, resulting in file loss.
To avoid such situations, follow the instructions listed below to ensure that BitLocker saves your recovery keys to AD.
Why is BitLocker recovery key not showing up in AD?
Usually, the key isn’t showing up in AD due to the following:
- System policies – If certain system policies aren’t enabled, your key won’t be saved to AD.
What can I do if the BitLocker recovery key is not saved to AD?
1. Make sure the Group Policy setting to save the key to AD is enabled
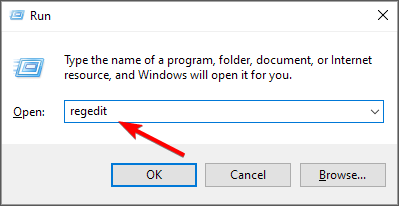
- Press Windows key + R and enter regedit.
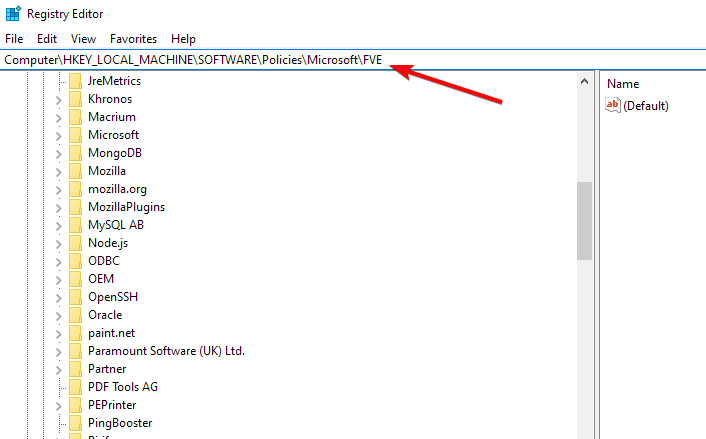
- Navigate to this registry key:
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\FVE - To allow backup of recovery information, make sure that the values listed below are available:
- OSActiveDirectoryBackup should be set to 1
- FDVActiveDirectoryBackup should be set to 1
- RDVActiveDirectoryBackup should be set to 1.
Also, make sure that the client is a member of the OU and that the BitLocker group policies apply to the respective OU.
After doing that, check if BitLocker is still not saving key to AD.
2. Get the ID for the numerical password protector
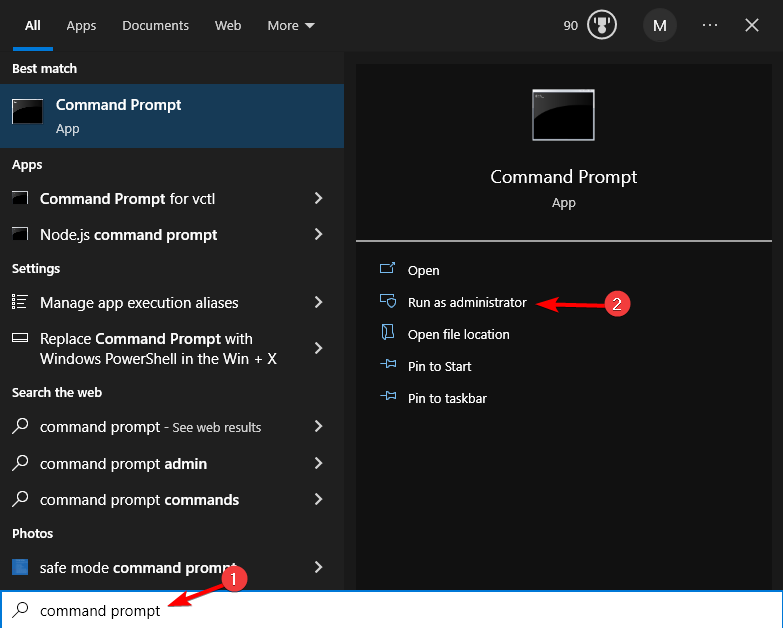
- Search for Command Prompt and select Run as administrator.
- Enter the following command, but be sure to use the correct drive letter:
manage-bde -protectors -get c: - You should now see your ID and password for the numerical password protector.
- Now run the following command but be sure to replace the values in brackets with your ID:
manage-bde -protectors -adbackup c: -id {...}
As you can see, you can easily fix the issue with BitLocker as long as you follow our simple instructions.
If you’re having further problems, we suggest reading our guide on how to find BitLocker recovery key.
We hope this helps. Also, if you found other solutions to enable BitLocker key saving to AD or fix BitLocker key backup issues, use the comments below to let us know.