DLL Hijacking: What is It & How to Safely Stop It?
Follow these best practices to prevent DLL hijacking
4 min. read
Updated on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team. Read more
Key notes
- DLL hijacking is a very difficult attack to detect on your PC.
- Critical Windows files like DLLs should only be downloaded from the developer’s website to avoid installing malicious files on your PC.
- Avoid clicking suspicious links in emails or direct messages to protect you from phishing.

DLLs are a critical component of the Windows OS. However, this component also poses a security risk to your PC as it is prone to hacking and exploitation by cybercriminals.
In this article, we’ll extensively discuss the term DLL hijacking, and provide you with numerous steps you can apply to help you prevent the exploit.
What is DLL hijacking?
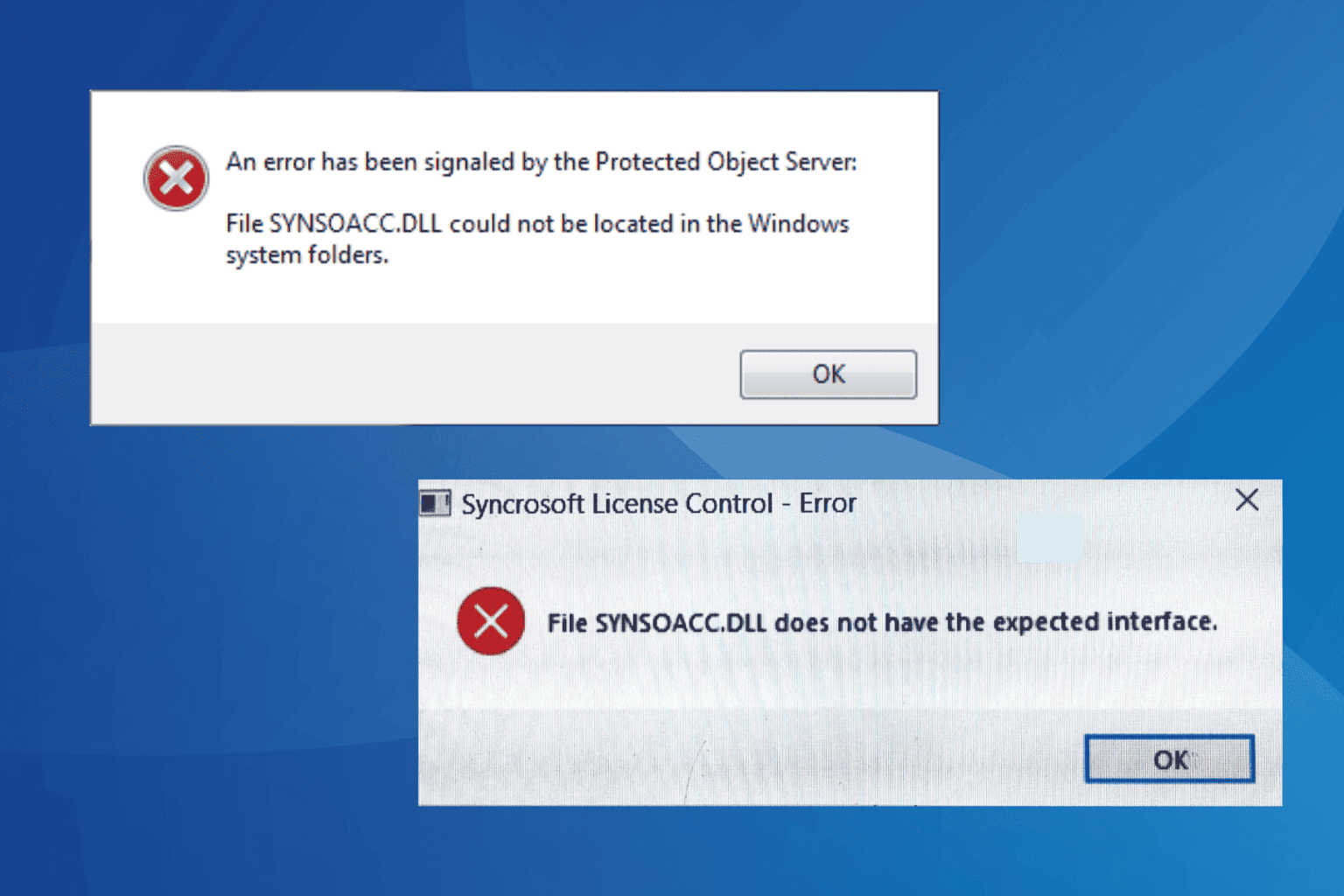
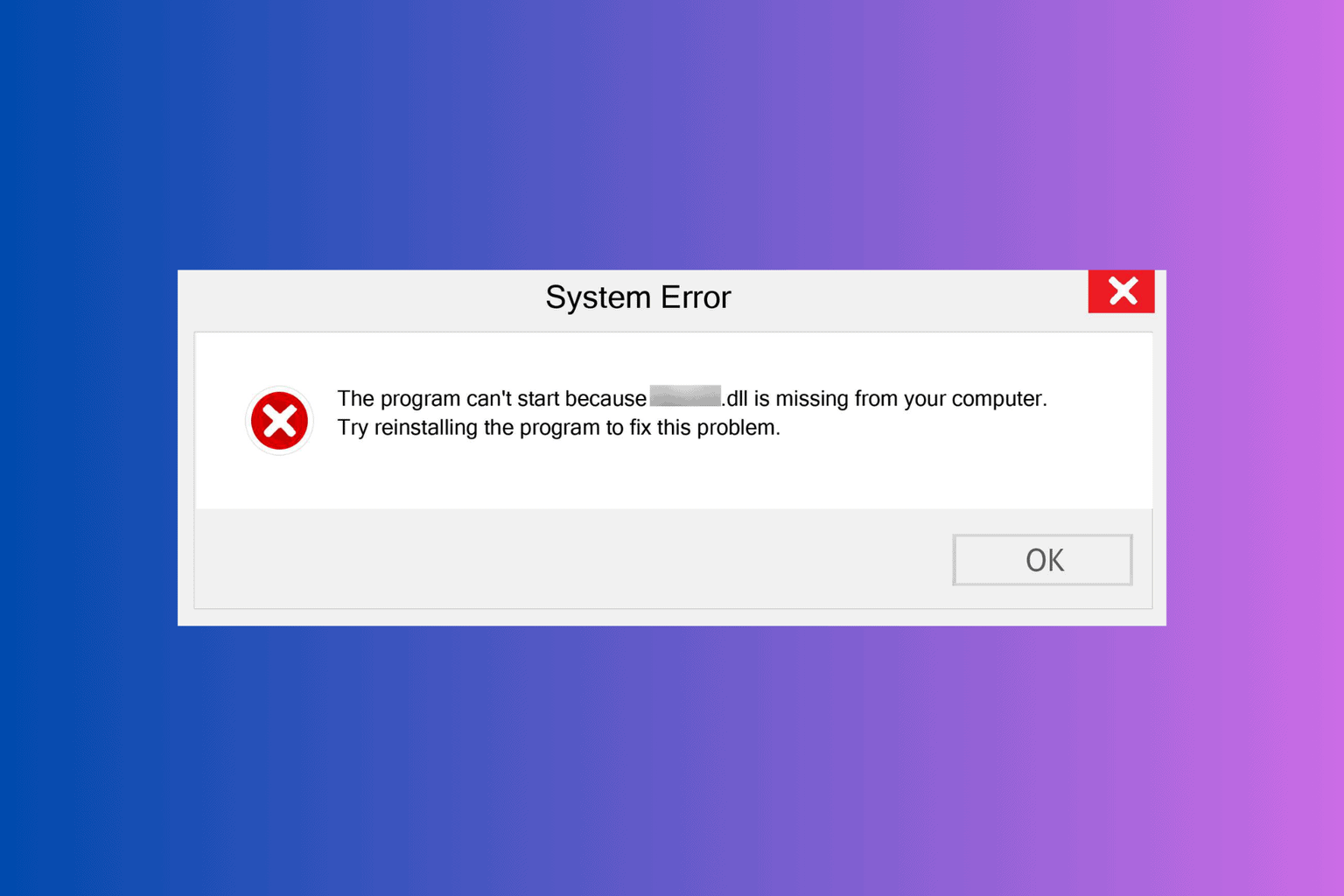
DLL hijacking simply refers to a cyberattack that allows hackers to insert and execute malicious code using the Dynamic Library File (DLL). The error is very common and is pretty difficult to detect, at least not until you begin to see the results of the attack.
With DLL hijacking, hackers replace legitimate DLL files on your PC with malicious ones. This makes it harder for antivirus software to detect the malicious file because it camouflages as a DLL file.
Hence, loading a malicious DLL on your PC can lead to massive data breach and affect services utilizing the DLLs.
DLL hijacking may occur through social engineering or phishing attacks that trick the user into downloading malicious code disguised as a DLL file.
How can I stop DLL Hijacking?
1. Avoid downloading/installing files from unknown sources
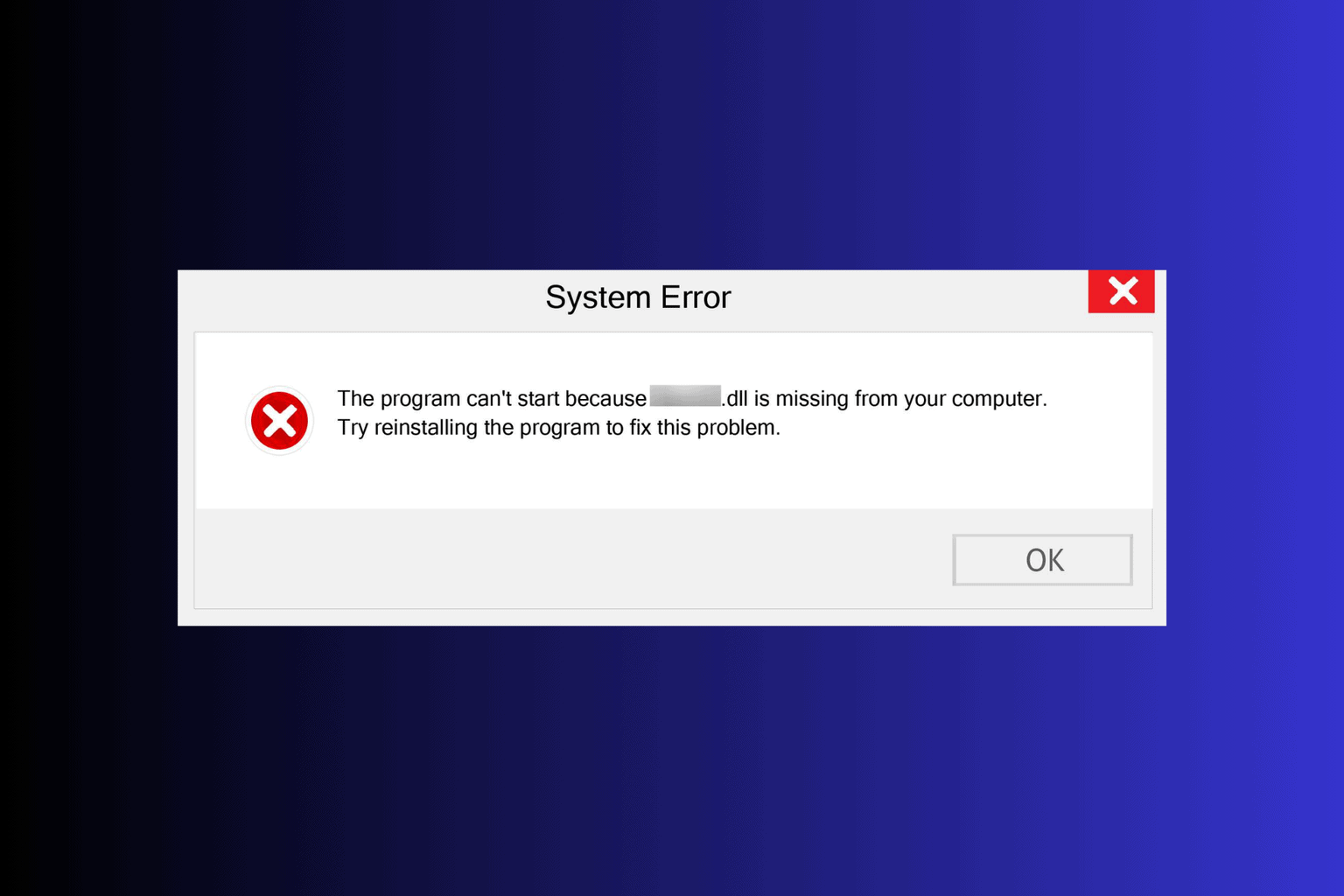
While attempting to troubleshoot errors like missing DLL files on Windows, users will have to download specific files to fix them. However, files critical to the PC’s functionality shouldn’t be downloaded from just any website.
For example, if you want to fix the msvcp120.dll error, avoid downloading the missing DLL file from third-party websites. This is because hackers can easily camouflage malicious code as a DLL file and make the file available for download.
Hence, you can use a DLL repair tool like the following one. These tools scan your PC and take care of any anomalies they detect; if there are malicious DLL files on your PC, a DLL repair tool can identify such files.
2. Use a Powerful Antivirus Software
Windows Defender is Microsoft’s primary security software but doesn’t provide as many features and functionality needed to tackle emerging threats and vulnerabilities.
There are countless free and paid antivirus software available for Windows, but you shouldn’t just install any antivirus, as this software will be responsible for managing your entire PC security. Therefore, it’s important to employ the help of software like ESET.
ESET HOME Security Essential is an award-winning cyber security software that provides protection for Windows, macOS, and Android devices. The software is very easy to use and supports over 700 languages, allowing you to utilize the software in your preferred language.
Plus, this antivirus solution guarantees speedy and comprehensive protection from viruses and threats.
3. Keep your PC updated
As simple as it sounds, updating your PC regularly can protect you from viruses and malware. This is because most Windows updates usually contain fixes for critical bugs on your Windows OS.
Further, bugs lead to vulnerabilities in software which hackers can further exploit. If hackers exploit a bug, users who haven’t updated their OS would likely fall victim to the attack.
4. Avoid clicking on suspicious links in Emails
Phishing is one of the most effective techniques used by hackers to gain access to a system. It refers to the process where a user is tricked into performing a specific action, e.g. downloading a file, with the sole aim of compromising the unsuspecting victim.
If you receive an email that looks a little suspicious, it’s most likely a hacker attempting to gain access to your PC. Avoid clicking on such links to protect your PC from malware.
5. Apply fully qualified paths
One of the major factors that facilitates a DLL hijack is that a malicious DLL file is placed in a location that is searched by Windows before the legitimate file. A fully qualified path defines an exact path from a particular drive to a target file or directory.
Employing fully qualified paths while loading DLL files ensures that Windows only loads the DLL file from a specific location. Hence, preventing the malicious file’s accessibility from an alternative location.
DLL hijacking is a very dangerous cyberattack that can severely affect the functionality of your PC. Preventing the attack isn’t a straightforward process but you can take certain precautions to improve the security of your PC.
We hope this article has enlightened you about DLL hijacking, and provided you with the steps needed to protect yourself from the attack.

User forum
0 messages