How to Exclude Users From MFA in Azure: 4 Tested Methods
MFA in Azure provides an excellent layer of security
3 min. read
Published on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team Read more
Key notes
- To exclude a user from MFA in Azure, go to Active Directory > Users > Authentication Method and turn off MFA for a certain selected user.
- You may also create an exclusion group and set up a policy for it to be removed from MFA.
- Read below for the detailed steps provided by our WR software experts team.
Sometimes, you need to exclude one or more users from MFA in Azure because, for some reason, they can’t use multi-factor authentication.
Our WR software experts have tested a few methods to exclude users from the conditional access policies and outlined them below.
How do I disable MFA for a specific user in Azure?
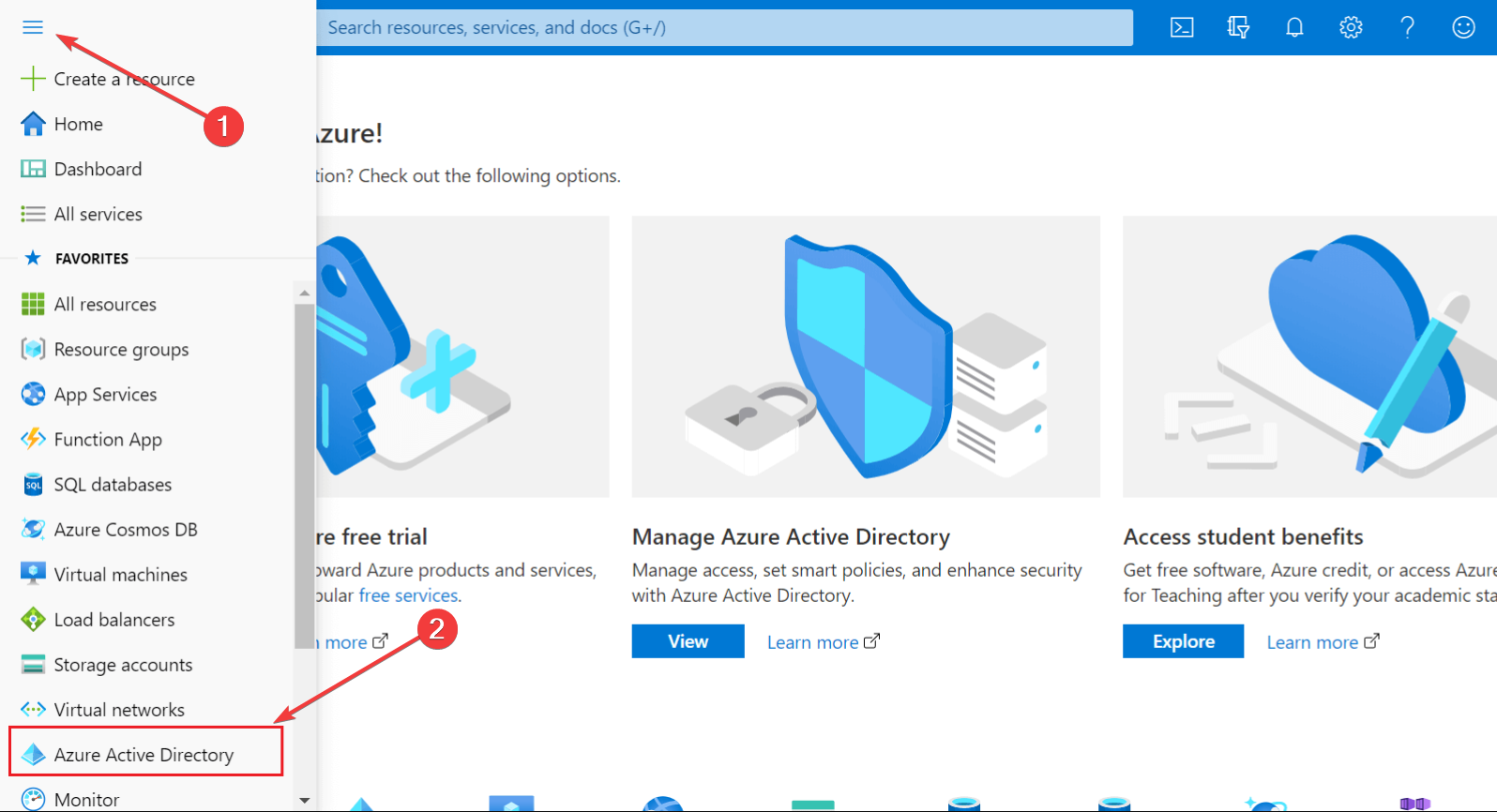
1. Disable MFA from Azure Active Directory
- Open the Azure portal and log in with administrative credentials.
- Select Azure Active Directory from main menu.
- From the new menu, select Users.
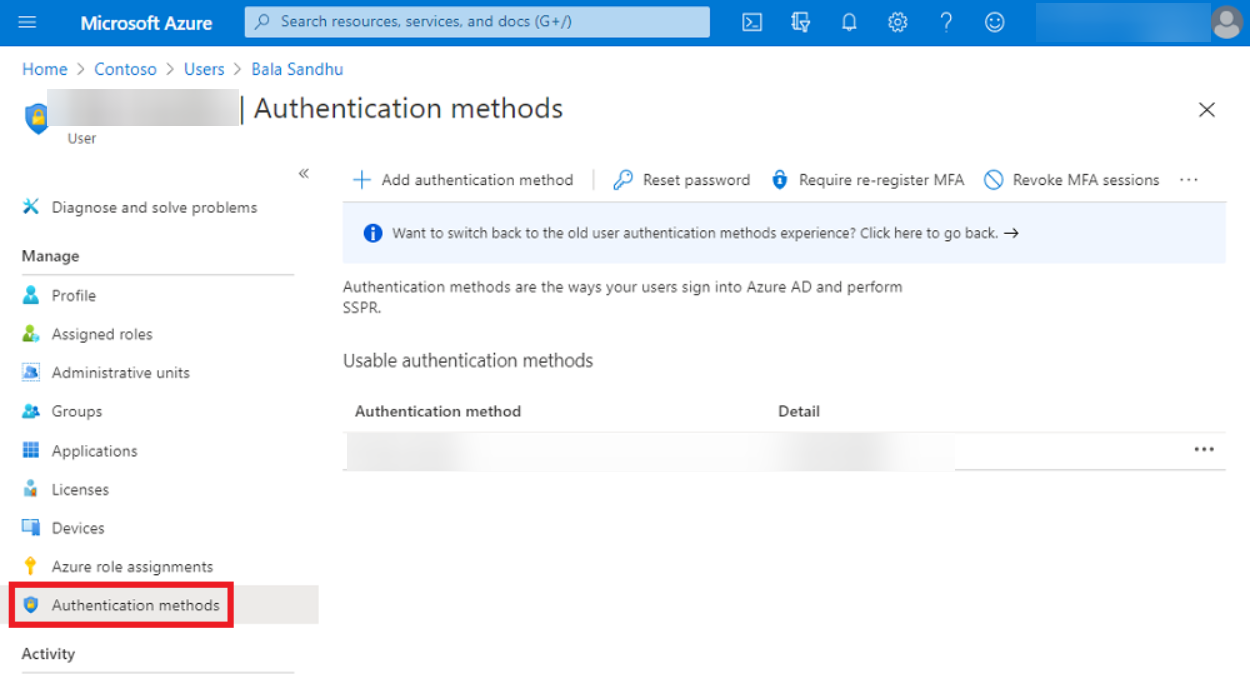
- Choose the user you need to exclude from MFA by looking or searching in the list of users, then click Authentication Method from the left pane.
- Now, slide the Multi-Factor Authentication box to Off and confirm the decision.
To confirm that you removed the multi-factor authentication for that user, try to log into Azure with the user credentials and check if there is any request for an MFA login.
2. Create an exclusion group and policy
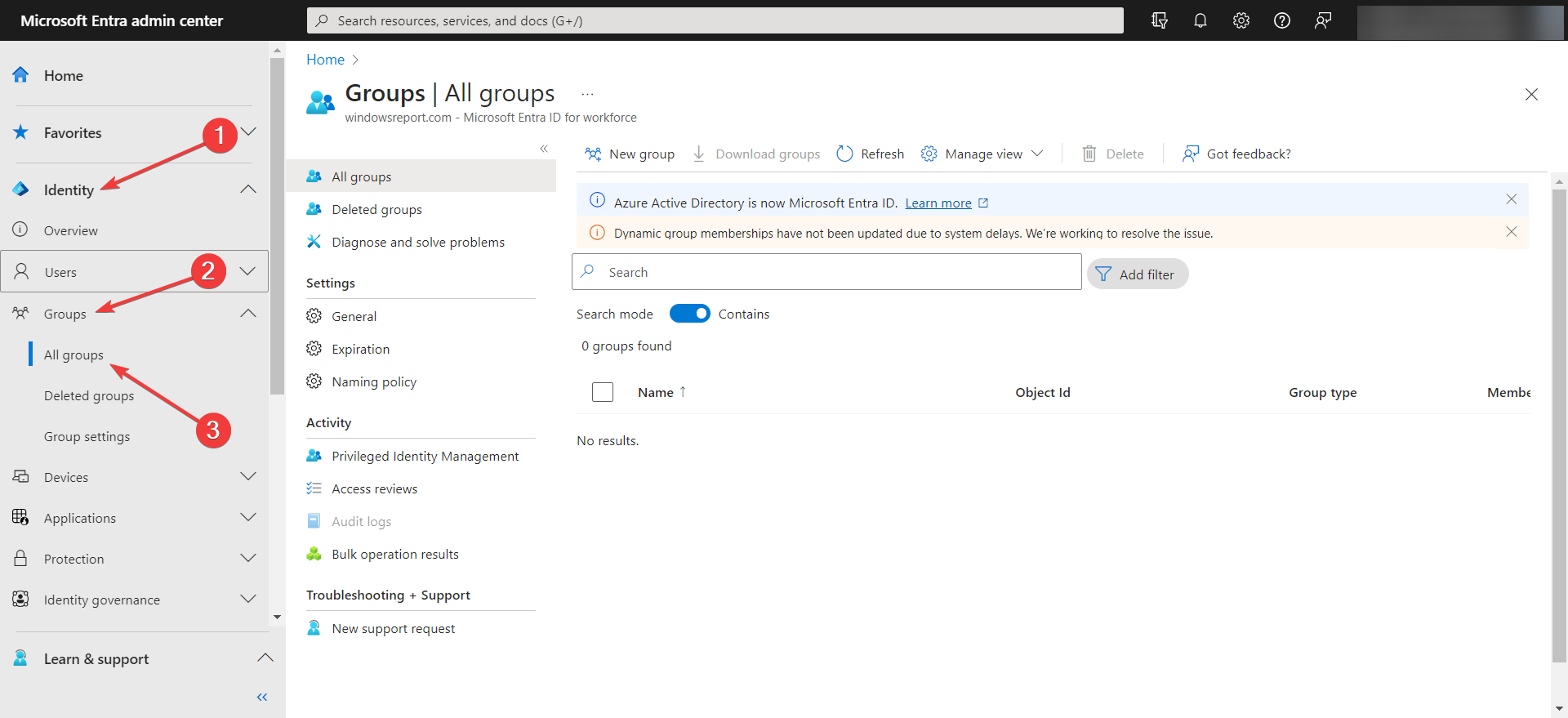
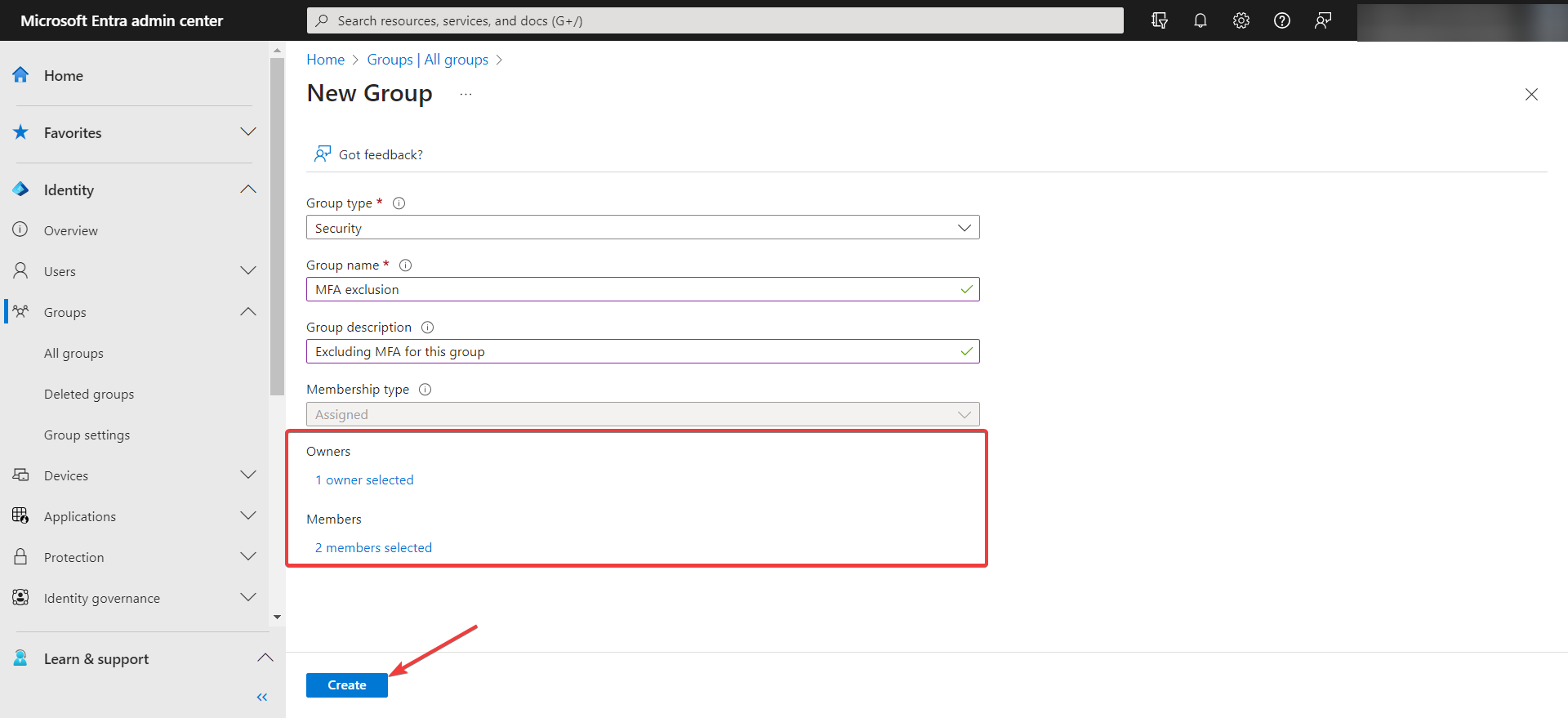
2.1 Create the exclusion group in Azure
- Sign into the Microsoft Entra admin center as an administrator.
- Browse to Identity > Groups > All groups.
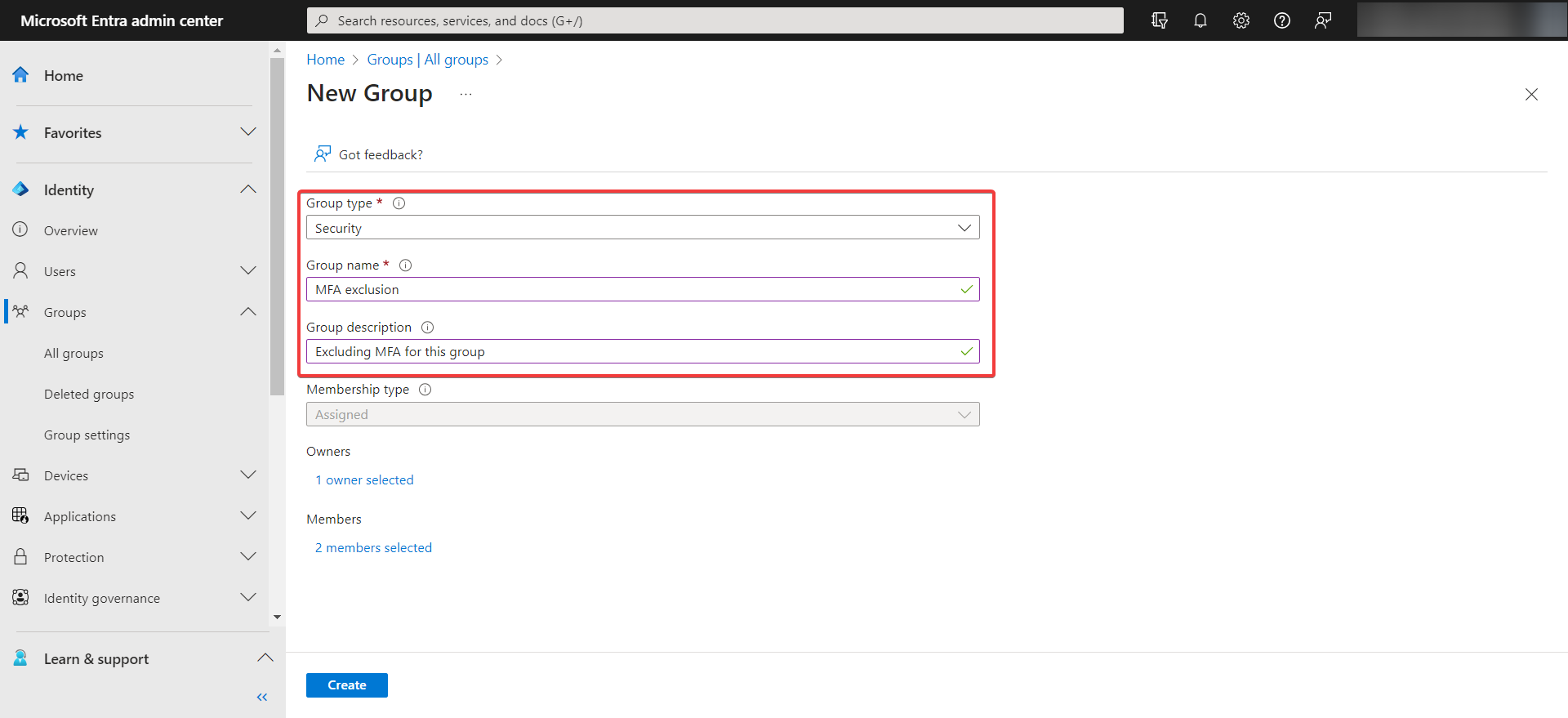
- Select New group and select Security in the Group type list, then specify a name and description.
- Leave or set the Membership type to Assigned, then select the owner of the group and the users that should be part of this exclusion group. Finally, select Create.
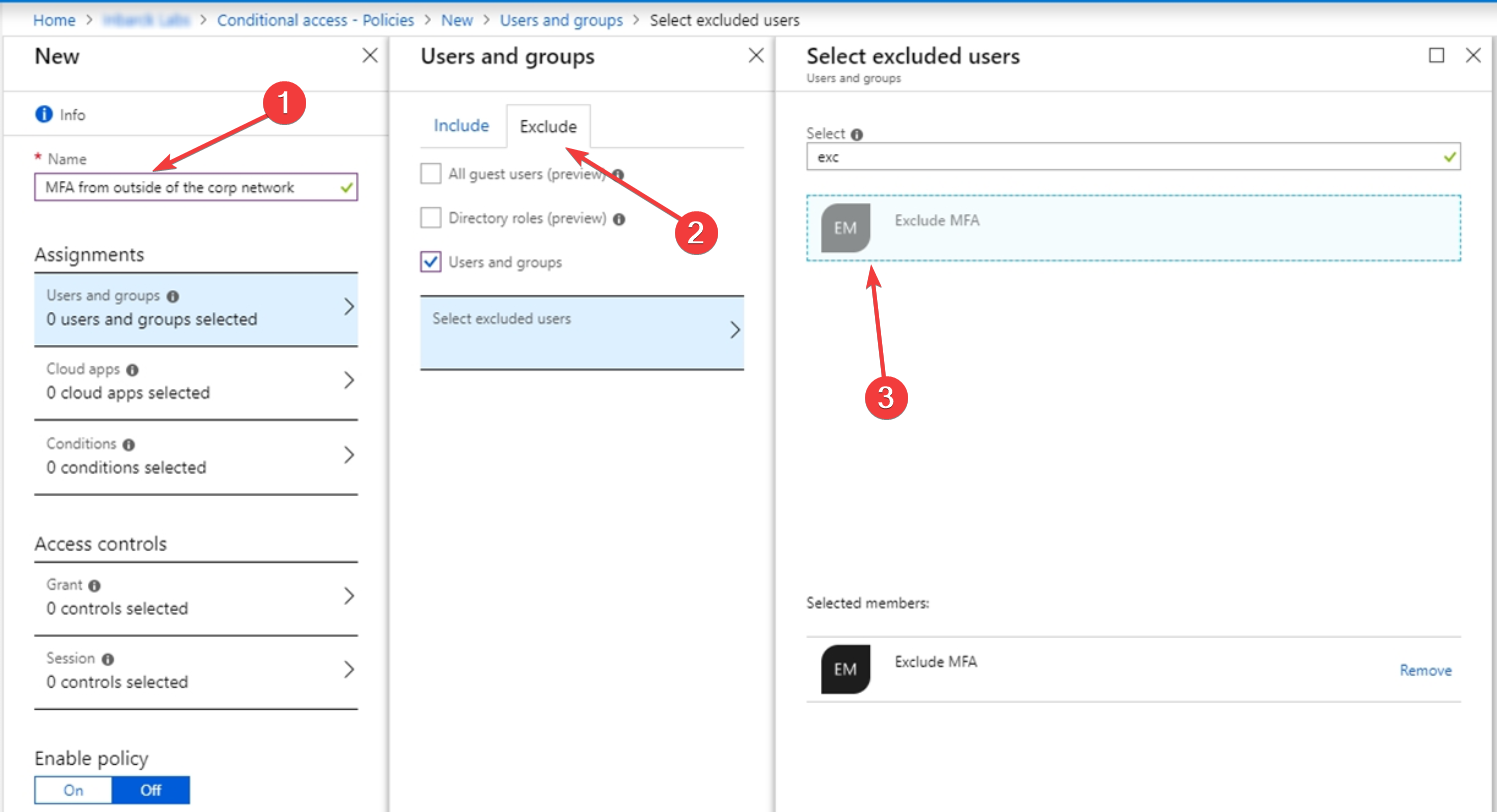
2.2 Create an MFA exclusion policy for the group
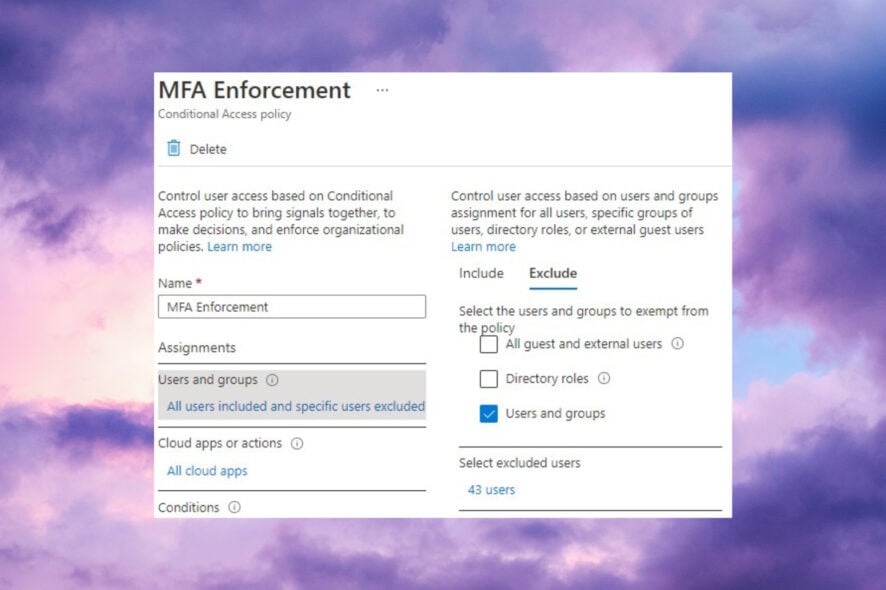
- Browse to Protection and select Conditional Access.
- Select Create new policy and fill in the name and description of the policy.
- Select Users and groups under Assignments
- On the Include tab, select All Users.
- Go to Exclude, select Users and groups, and choose the exclusion group you created in solution 2.1 above.
- Continue the process to set up the conditional access policy.
Now, the users from the group you have selected should have been excluded from multi-factor authentication when logging in.
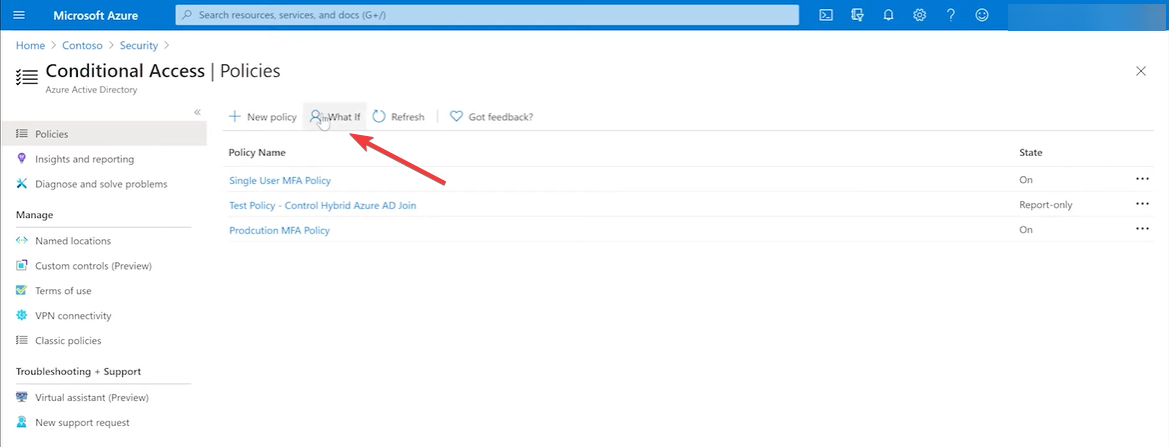
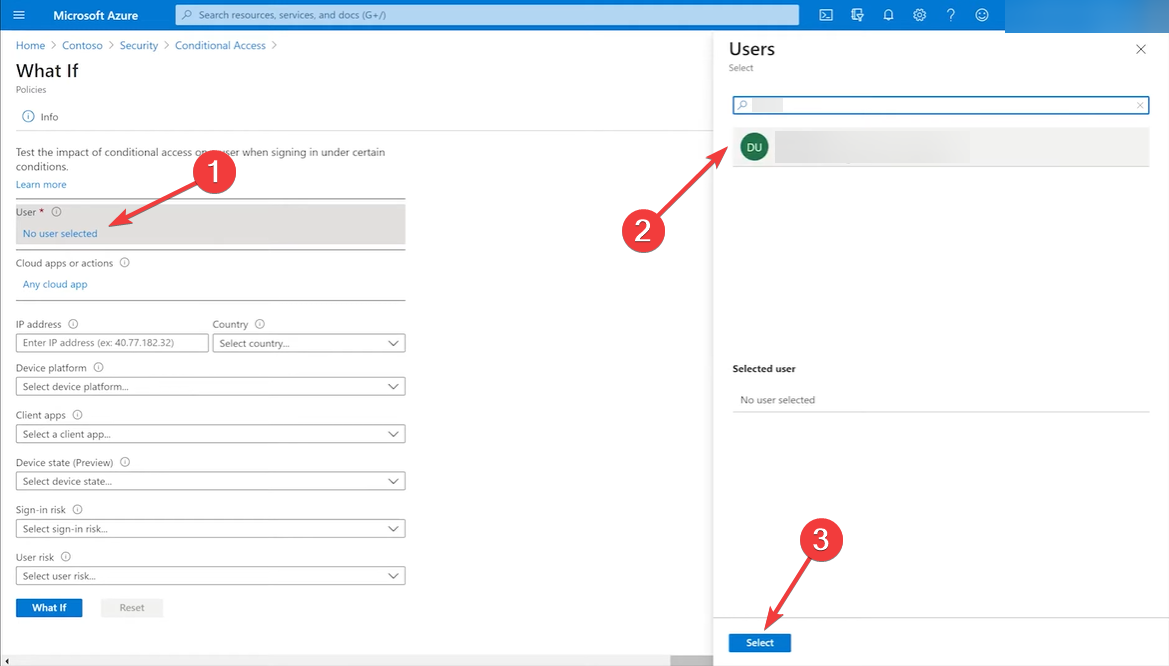
3. Use the What If conditional tool in Azure
- Log into Azure with administrative rights, click on Security, and select Conditional access.
- Next, click on What if.
- Now, click on User from the left pane, look for the user you want to check, and hit the Select button from the bottom right.
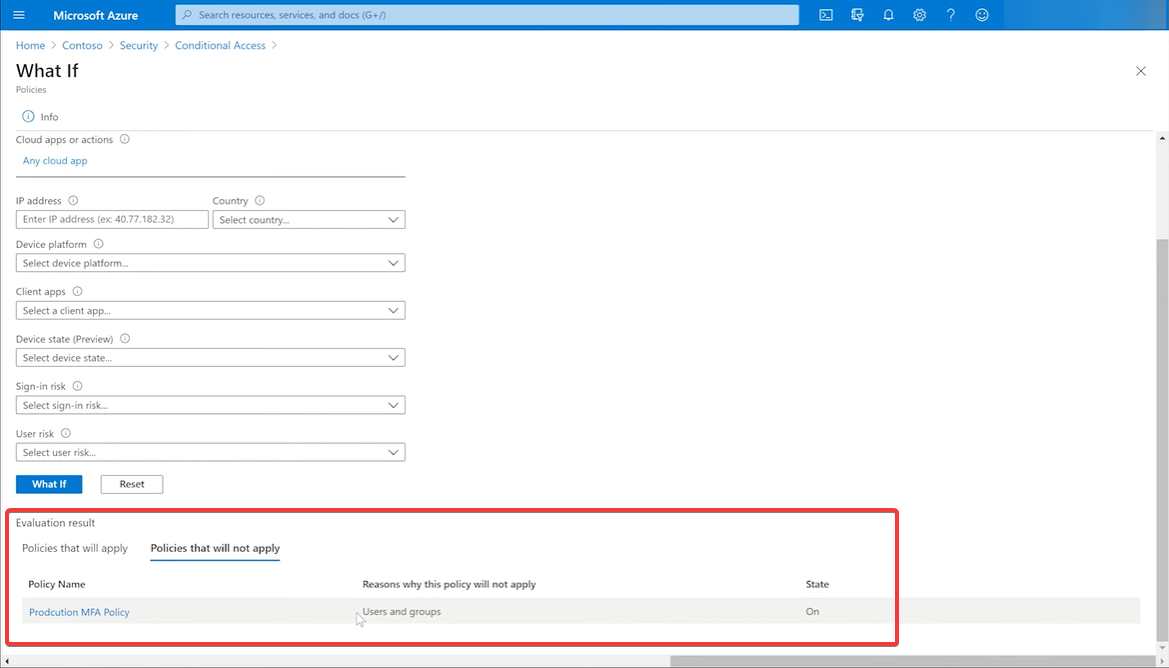
- Now, you will be able to see to what policies the user is subjected to.
The What If tool allows you to check what policies are applied to each user to see if there are any problems or conflicts. This will help you see if the multi-factor policy or other security policies are enforced.
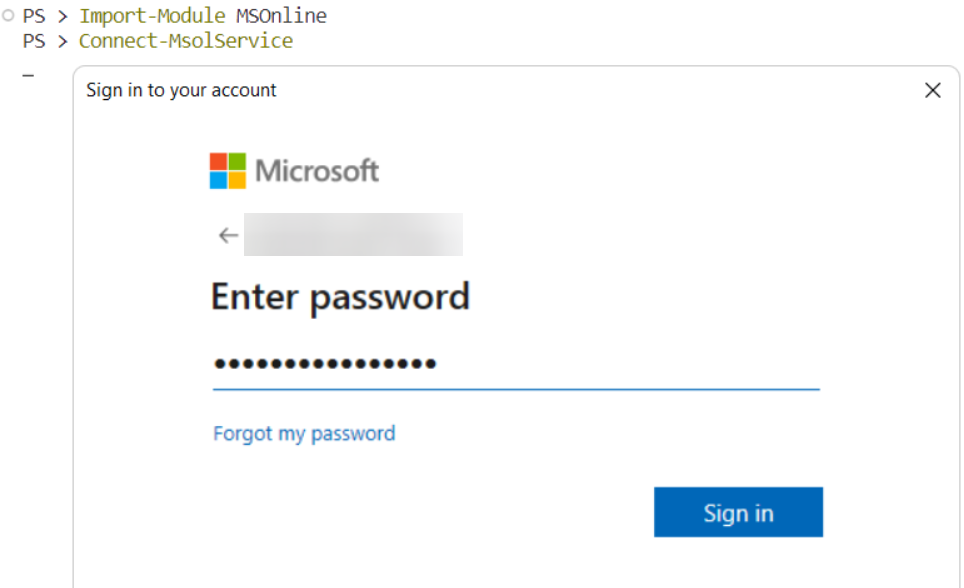
4. Disable Per User MFA in PowerShell
- Connect to Azure AD (Entra) PowerShell by running the following commands:
Import-Module MSOnline
Connect-MsolService
- Sign into your Azure AD administrative account (now called Entra).
- Type or paste the following command and replace UPN with the user’s principal name:
Set-MsolUser -UserPrincipalName "UPN" -StrongAuthenticationRequirements @()
How do I know if a user is registered for MFA?
You can check the Azure MFA policy in the Security menu, but using the What If tool from Solution 3 above is a lot easier.
Note that in order to have access to users and the security defaults, you will need an administrative account.
So, now you know how to exclude a user from Azure Multi-Factor Authentication (MFA) and restore the user access to the classic username and password method.
You might also be interested in learning how to apply MFA on Windows 11, or how to set up multi-factor authentication on RDP.
If you have any other questions or tested solutions, don’t hesitate to use the comments section below and let us know about them.