LinkedIn security vulnerability injects malicious payloads on your PC
3 min. read
Updated on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team Read more

Experts of Proofpoint uncovered new malware campaigns on LinkedIn. Similar campaigns have been noticed for a long time. These malware campaigns are targeting individuals though fake LinkedIn accounts.
LinkedIn is used by different companies and businesses to attract employee or to create vast professional networks. Different companies provide job opportunities, so the jobseekers leave their resume out there.
Clever cybercriminals are active, and they are always ready to harvest sensitive information. Although LinkedIn provides optimized conditions for professional networks, it is more prone to cybercriminals. So, users must be careful when uploading personal information.
In case you want to be secure while surfing the internet, you will need to get a full-dedicated tool to secure your network. Install now Cyberghost VPN and secure yourself. It protects your PC from attacks while browsing, masks your IP address and blocks all unwanted access.
Modus operandi
Hackers use different vectors for distribution of malware so as to leave many downloadable eggs. The hackers can review jobs opportunities and posts by different companies.
After reviewing the LinkedIn profiles of different companies, they can get an idea about the company’s networks, partners and operating system. In this way, they can target various industries and retails.
They can steal the LinkedIn connections of different companies and then they offer jobs for different well-reputed positions in those companies. As ProofPoint researchers state:
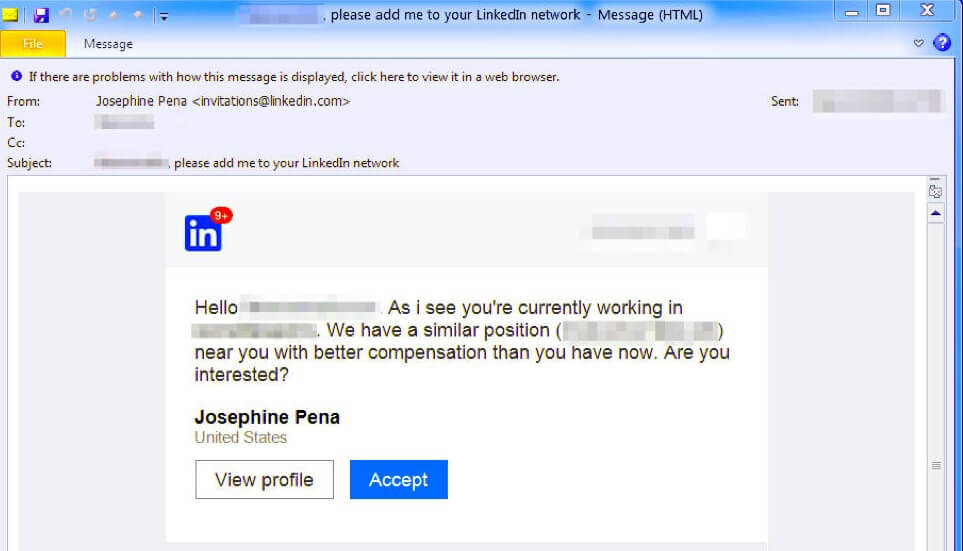
The URLs link to a landing page that spoofs a real talent and staffing management company, using stolen branding to enhance the legitimacy of the campaigns.
They may also make fake accounts like Facebook and Twitter and then send benign emails to users. Starting through simple conversation they seek the attention of users by providing information about jobs.
They send different URLs which are connected to the landing page. Landing page contains different types of files such as PDF, Microsoft Word documents or any other such documents.
These documents, created with Taurus Builder starts downloading automatically with harmful macros. If the user opens the macros More-eggs will be downloaded. ProofPoint researchers further added that:
This actor provides compelling examples of these new approaches, using LinkedIn scraping, multi-vector and multistep contacts with recipients, personalized lures, and varied attack techniques to distribute the More eggs downloader, which in turn can distribute the malware of their choice based on system profiles transmitted to the threat actor.
If more downloadable eggs are loaded then it is not possible to protect your account. The one way to protect your personal information is to use a strong and unique password.
The other way is, that if you receive any message or email from any company, then do not open it or click on the URL. LinkedIn is more sensitive to cybercriminals’ attacks, so you should be careful when creating an account on LinkedIn.
RELATED GUIDES YOU NEED TO CHECK OUT: