Microsoft Defender brings new tools to fight device tracking
2 min. read
Updated on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team. Read more
Key notes
- Microsoft Defender Endpoint brings a new way for IT administrators to fight against device exposure.
- Read the lines below to find all about the new report designed to easily identify vulnerable devices.
- To keep your organization safe from any threats, take a look at this Microsoft Defender section too.
- Don’t hesitate to bookmark our Security & Privacy Software Hub for extra tips and tricks on this topic.

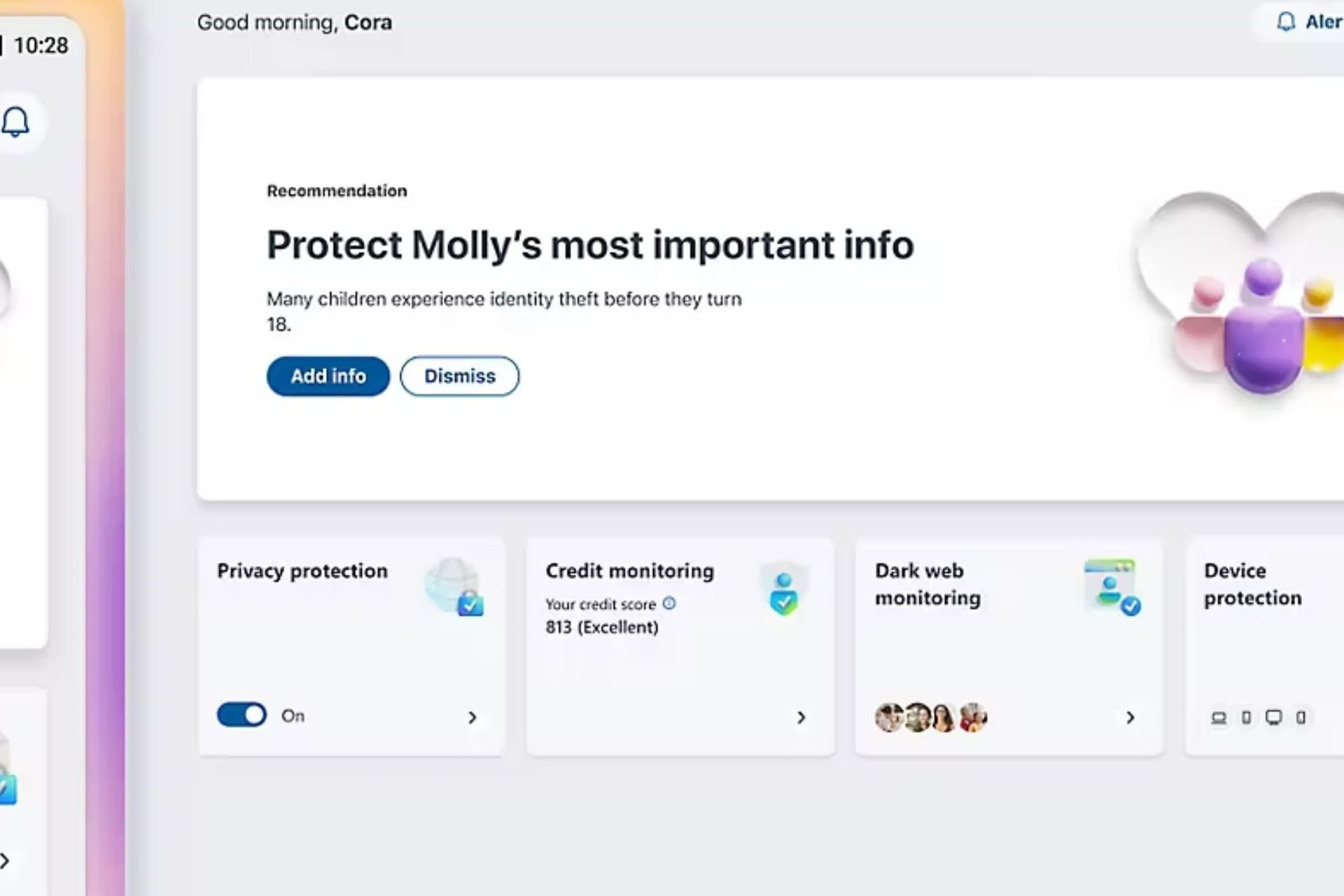
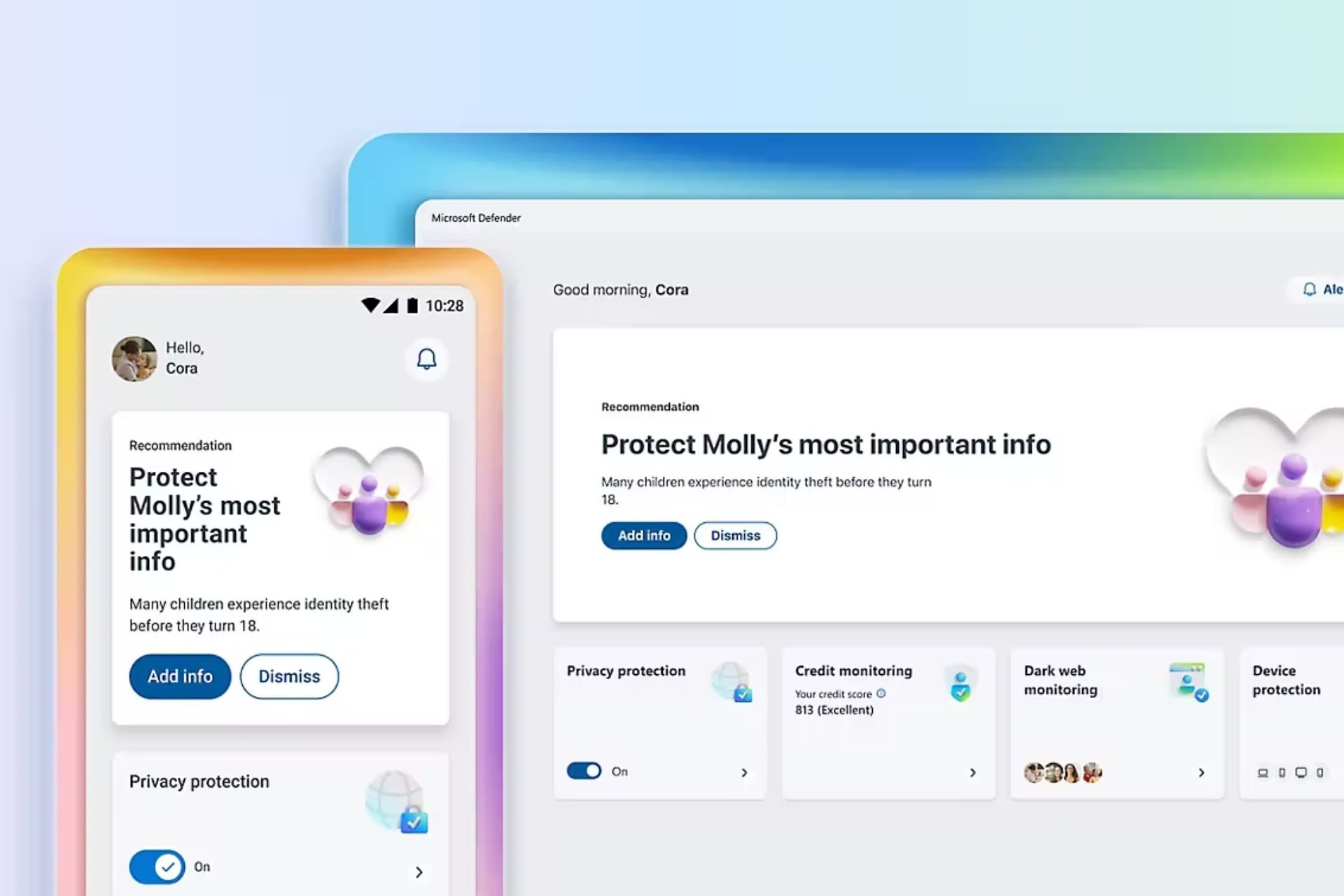
Microsoft Defender for Endpoint provides users with a new report designed to help them identify and keep track of vulnerable Windows and Mac OS devices.
As a reminder, that’s an enterprise endpoint security platform that helps enterprise networks prevent and respond to latest threats.
The changes are supposed to make it easier for IT administrators to fight against device vulnerability within the organization. That’s what Microsoft reveals:
The report shows graphs and bar charts with vulnerable device trends and current statistics. The goal is for you to understand the breath and scope of your device exposure.
How to access new Vulnerable devices report?
In order to access the report in the Microsoft Defender Security Center, you simply need to enter into Reports > Vulnerable devices.
Here you’ll find two new columns:
- Trends – you may see the past 30 days, 3 months, 6 months, or a custom date range of your choice
- Today – this column reveals current information only
You’ll also be able to filter the data by exploit availability, vulnerability severity levels, vulnerability age, operating system platform, Windows 10 version, or device group.
Moreover, to further explore an insight, select the relevant bar chart to view a filtered list of devices in the Device inventory page. You may now export the list and continue your investigations.
Do you find these graphs with statistics and details on currently vulnerable device trends as being useful within your organization? Let us know your opinion in the comments area below.
[wl_navigator]

User forum
0 messages