FIX: NETLOGON folder doesn't replicate
4 min. read
Updated on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team Read more

One of the best ways an IT Administrator can organize your company’s users, computers and more is through the use of an Active Directory. It organizes your company’s complete hierarchy from which computers belong on which network.
This ranges from meaningless things such as what your profile picture looks like to more complex matters such as which users have access to a certain file.
However, things don’t always go as planned with Active Directories, as some users have reported having issues with certain folder replications:
In my company’s AD, we have three DC’s (two in 2008R2 standard, one in 2012R2 standard core).
I’ve found that NETLOGON folder content is not replicated correctly across them
Thankfully enough, users went into further details as to how the issue manifested itself, and a solution was quickly figured out. If you too are having similar issues, continue reading the article below for a step-by-step guide on how to fix the issue.
How do I make the NETLOGON folder replicate properly?
You first have to identify which folder has the latest contents, or which folder which has scripts that run without issues.
You then take that Domain Components and declare it as Master while the other Domain Components are declared as Slaves, and then you just program a replication from Master to Slave.
1. Perform a non-authoritative synchronization
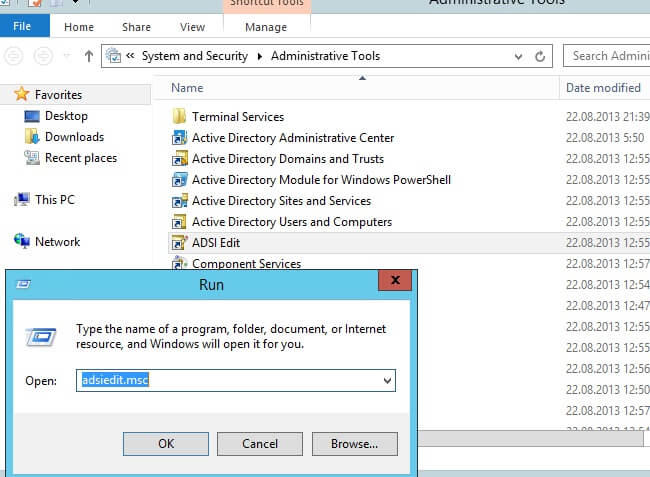
- Download and install the ADSIEDIT.msc tool
- In the ADSIEDIT.MSC tool modify the following distinguished name (DN) value and attribute on each of the domain controllers that you want to make non-authoritative:
- CN=SYSVOL Subscription
- CN=Domain System Volume
- CN=DFSR-LocalSettings
- CN=<the server name>
- OU=Domain Controllers
- DC=<domain>
- msDFSR-Enabled=FALSE
1.1 Force Active Directory replication throughout the domain.
- Run the following command from an elevated command prompt on the same servers that you set as non-authoritative:
- DFSRDIAG POLLAD
- You will see Event ID 4114 in the DFSR event log indicating SYSVOL is no longer being replicated.
- On the same DN from Step 1, set:
- msDFSR-Enabled=TRUE
1.2 Force Active Directory replication throughout the domain.
- Run the following command from an elevated command prompt on the same servers that you set as non-authoritative:
- DFSRDIAG POLLAD
You will see Event ID 4614 and 4604 in the DFSR event log indicating SYSVOL has been initialized. That domain controller has now done a “D2” of SYSVOL.
Don’t have Active Directory on Windows Server? Check out this detailed guide for more information.
2. Perform an authoritative synchronization
- In the ADSIEDIT.MSC tool, modify the following DN and two attributes on the domain controller you want to make authoritative:
- CN=SYSVOL Subscription
- CN=Domain System Volume
- CN=DFSR-LocalSettings
- CN=<the server name>
- OU=Domain Controllers
- DC=<domain>
- msDFSR-Enabled=FALSE
- msDFSR-options=1
- Modify the following DN and single attribute on all other domain controllers in that domain:
- CN=SYSVOL Subscription
- CN=Domain System Volume
- CN=DFSR-LocalSettings
- CN=<each other server name>
- OU=Domain Controllers,DC=<domain>
- msDFSR-Enabled=FALSE
2.1 Force Active Directory replication throughout the domain and validate its success on all DCs
- Start the DFSR service set as authoritative
- You will see Event ID 4114 in the DFSR event log indicating SYSVOL is no longer being replicated
- On the same DN from Step 1, set:
- msDFSR-Enabled=TRUE
2.2 Force Active Directory replication throughout the domain and validate its success on all DCs
- Run the following command from an elevated command prompt on the same server that you set as authoritative:
- DFSRDIAG POLLAD
- You will see Event ID 4602 in the DFSR event log indicating SYSVOL has been initialized.
- That domain controller has now done a “D4” of SYSVOL.
- Start the DFSR service on the other non-authoritative DCs.
- You will see Event ID 4114 in the DFSR event log indicating SYSVOL is no longer being replicated on each of them
- Modify the following DN and single attribute on all other domain controllers in that domain:
- CN=SYSVOL Subscription
- CN=Domain System Volume
- CN=DFSR-LocalSettings
- CN=<each other server name>
- OU=Domain Controllers,DC=<domain>
- msDFSR-Enabled=TRUE
- Run the following command from an elevated command prompt on all non-authoritative DCs:
- DFSRDIAG POLLAD
Conclusion
By following these steps you should be able to now make all folders withing the Active Directory’s Domain Components replicate themselves properly without any further issues.
Note: This guide is targeted towards those that have experience modifying Active Directory settings. If you are unsure how to follow these steps, better leave it to the experts.
If you have any further questions or know of a solution we may have missed out on, leave us a message in the comments section below.
User forum
0 messages