7 Best Practices for NTFS Permissions: Keep Your Data Secure
Great management tips with NTFS permissions
5 min. read
Updated on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team Read more
Key notes
- Who may access a file or folder and what actions they can take are determined by NTFS permissions.
- Read, write, and execute are among the basic permissions, while full control, modification, and read & execute are among the advanced permissions.
NTFS permissions are a security feature in Windows that allows administrators to control who can access files and folders on an NTFS file system. These permissions work with local and network resources.
They are also essential to securing sensitive data and ensuring compliance with various regulations. This article will discuss seven best practices for configuring NTFS permissions. Hence, it will show you how to keep your data secure and reduce the risk of unauthorized access.
What are NTFS Permissions?
NTFS permissions or access control entries (ACEs) determine who can access a file or folder and what actions they can perform.
There are two kinds of NTFS permissions: basic permissions and advanced permissions. Basic permissions include read, write, and execute, while advanced permissions have full control, modify, and read & execute.
There are a few advantages associated with NTFS permissions. These include the following:
- Granular control – NTFS permissions provide a high level of granularity, allowing administrators to control access to individual files and folders down to the user or group level. This allows for a more secure and efficient use of resources.
- Inheritance – NTFS permissions can be inherited from parent folders to child objects, simplifying the process of managing permissions and reducing the risk of errors.
- Auditing – NTFS permissions can be audited, so administrators can track and log changes to permissions. This can help to detect and prevent unauthorized access.
- Security – NTFS permissions provide an additional layer of security for your files and folders. You can help minimize the risk of unauthorized access and data breaches by controlling your data.
- Compliance – NTFS permissions can help you meet various compliance requirements, such as HIPAA and PCI-DSS.
Let us now explore some noteworthy best practices.
What is the recommended best practice around configuring NTFS permissions?
1. Use a permission management tool
These tools can automate many tasks associated with managing permissions, such as reporting and alerting.
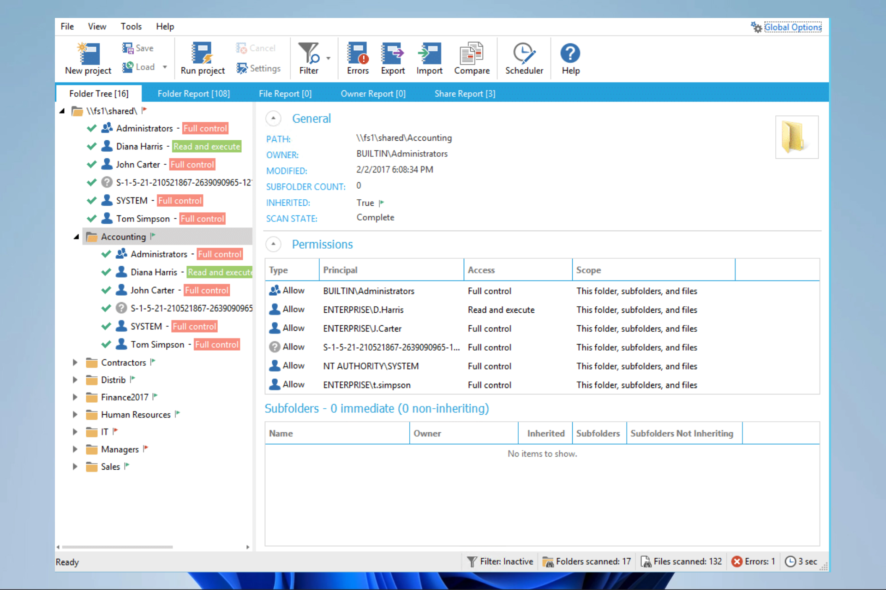
Note that a few tools may help with permissions. ADAudit Plus is one example. This tool can provide detailed visibility into changes made to NTFS permissions, including who made the change, when it was made, and what the change was.
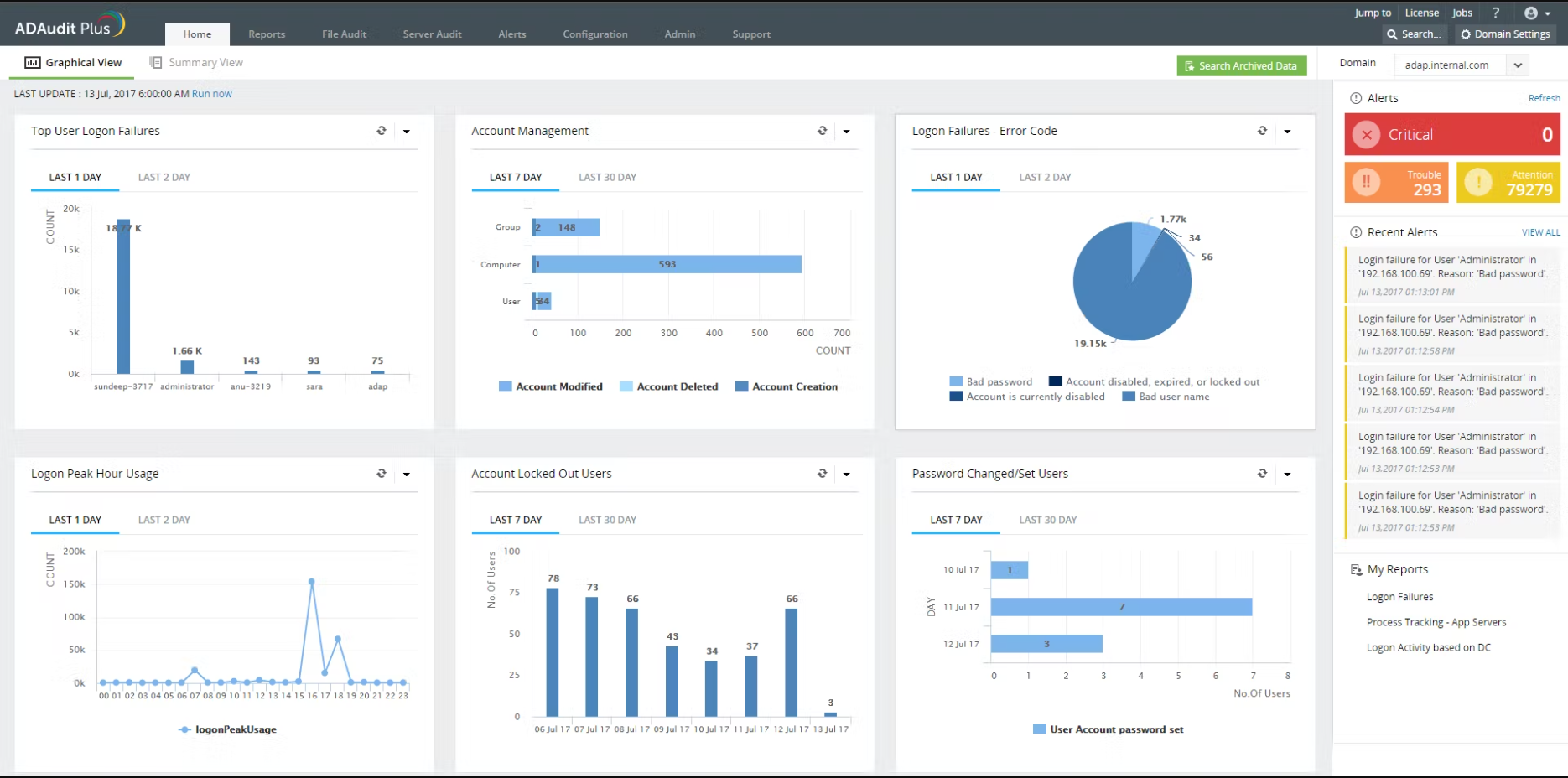
It also provides real-time alerts for critical NTFS permission changes and allows you to generate reports on NTFS permission changes.
ADAudit Plus
Great audit tool that offers comprehensive file audit, monitoring, and NTFS permission options.2. Least Privilege
Least Privilege is a best practice when configuring NTFS permissions, which means giving users and groups only the permissions they need to complete their tasks and nothing more.
This principle helps to ensure that users and groups have access to only the resources they need to perform their job functions and that they cannot access sensitive data or perform actions that could harm the system.
By applying the principle of least privilege, you can help to reduce the risk of unauthorized access and data breaches. For example, if a user only needs to read a specific file, they should be given read permission and nothing more.
3. Deny permissions
The Deny permission is a powerful NTFS permission that can override any Allow permissions. While it can be helpful in certain situations, it is important to use it sparingly and with caution, as it can also lead to confusion and errors.
The Deny permission is used to explicitly prevent a user or group from accessing a specific file or folder, regardless of any Allow permissions granted.
It’s important to note that the Deny permission takes precedence over any Allow permission, which means that if both Allow and Deny permissions have been assigned to a user or group, the Deny permission will take precedence, and the user or group will be denied access.
4. Use groups
Using groups as an NTFS permissions best practice is a method of managing permissions that can make it easier and reduce the risk of errors.
Instead of granting permissions to individual users, groups manage permissions. By assigning permissions to groups, you can simplify the process of managing permissions and make it more efficient.
When using groups, assigning users to the appropriate groups is essential based on their roles and responsibilities. This ensures that the user only has access to the resources they need to perform their job function and nothing more.
5. Remove unused permissions
Removing unused permissions is a best practice when working with NTFS (New Technology File System) permissions.
NTFS permissions control access to files and folders on an NTFS-formatted drive. These permissions can apply to individual files and folders and entire drives.
By removing unused permissions, you can ensure that only authorized users can access sensitive data and eliminate potential security vulnerabilities.
6. Test permissions
By testing permissions, you can ensure that the permissions you have set up are working as intended and that only authorized users can access sensitive data.
This is important because if a user has permissions that they should not have, they may be able to access sensitive data or perform actions that could compromise the system’s security.
Additionally, by testing permissions, you can identify and resolve any issues with permissions that may be causing problems for users or administrators.
7. Document permissions
NTFS permissions control access to files and folders on an NTFS-formatted drive and can be complex to manage and understand.
By documenting permissions, you can ensure that your permissions are understandable. Also, you can identify any potential issues or changes and address them quickly.
This is important because if permissions are not well-documented, troubleshooting and resolving issues or making future permissions changes can be challenging.
Additionally, documentation can help with compliance and auditing requirements.
By following these best practices, you can ensure that your NTFS permissions configuration is correct. Hence, your data is secure.
Remember, NTFS permissions are a critical aspect of securing your data. So, it is essential to take the time to configure and manage them properly.