Phishing attacks on Microsoft 365 accounts are peaking right now; users advised to pay close attention to emails
Phishers are using the highly efficient Greatness kit to sabotage accounts.
3 min. read
Published on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team Read more

This shouldn’t come as a surprise, but phishing attacks on Microsoft 365 accounts are peaking right now, according to a recent report published by the cybersecurity company Trustware, where researchers there agreed that the platform is targeted by accounts using the Greatness phishing kit, which is known to be fairly easy to use, cheap, and efficient.
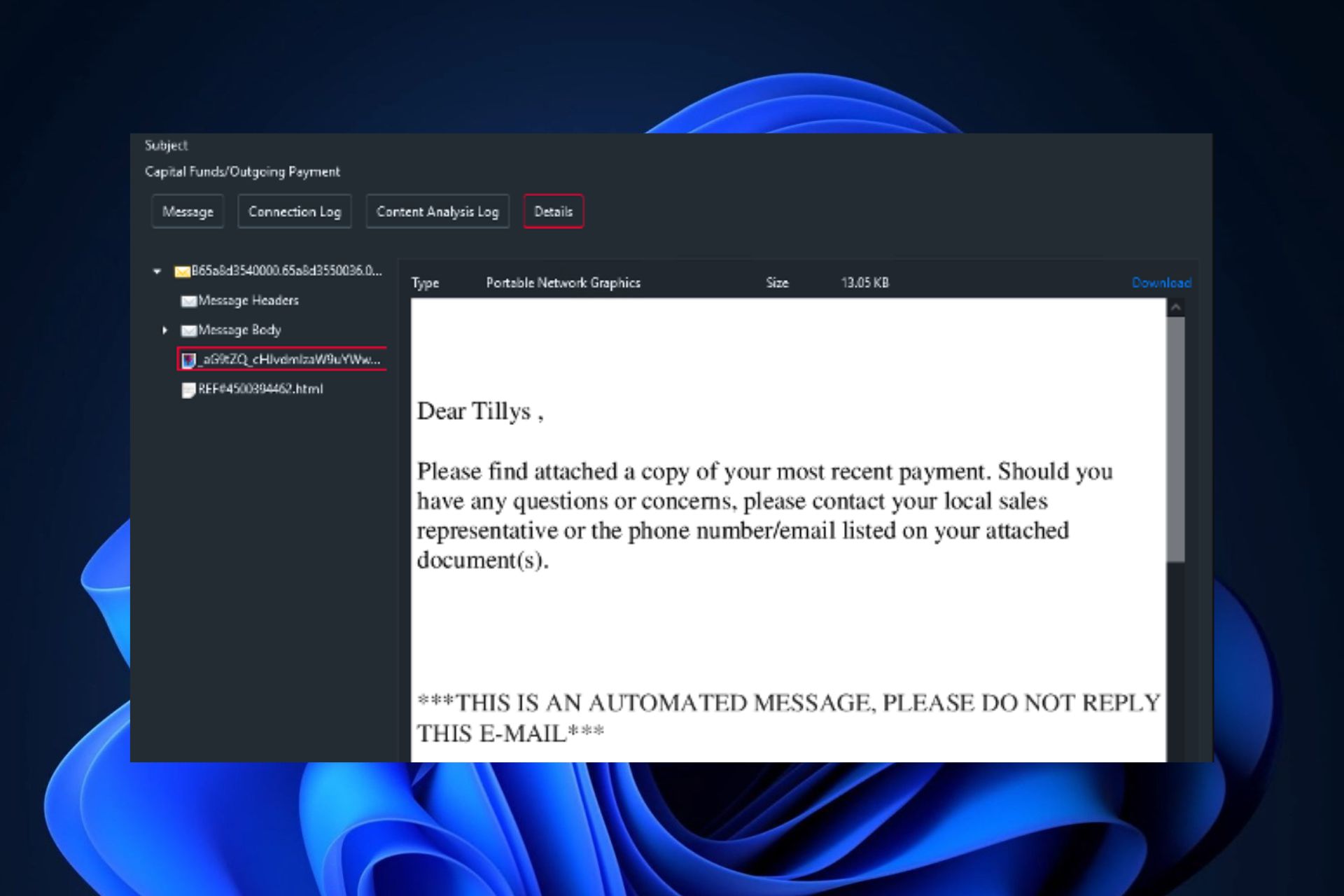
Trustwave SpiderLabs is tracking a spike in usage of the Greatness phishing kit to attack Microsoft 365 users to distribute malicious HTML attachments that steal login credentials.
Trustware
The Greatness phishing kit is a relatively new platform developed by a threat actor known as “fisherstell”. It has been around since 2022, but the cybersecurity company has noticed the spike in its usage to sabotage Microsoft 365 accounts over December 2023, and January 2023.
Microsoft 365 has always been one of the most popular platforms for cybersecurity attacks, and in 2022, over 80% of the accounts on the platform were the subject of some sort of phishing attack. So, while this is not a surprise for the users, they are advised to pay close attention to any suspicious-looking emails, as the kit’s easy-to-use method might have made thousands of victims already.
The number of victims is unknown at this time, but Greatness is widely used and well-supported, with its own Telegram community providing information on how to operate the kit, along with additional tips and tricks. The Greatness kit being used during this recent surge in attacks represents the latest HTML phishing iteration we’ve observed deployed.
Trustware
How to recognize a Microsoft 365 Greatness phishing attack?
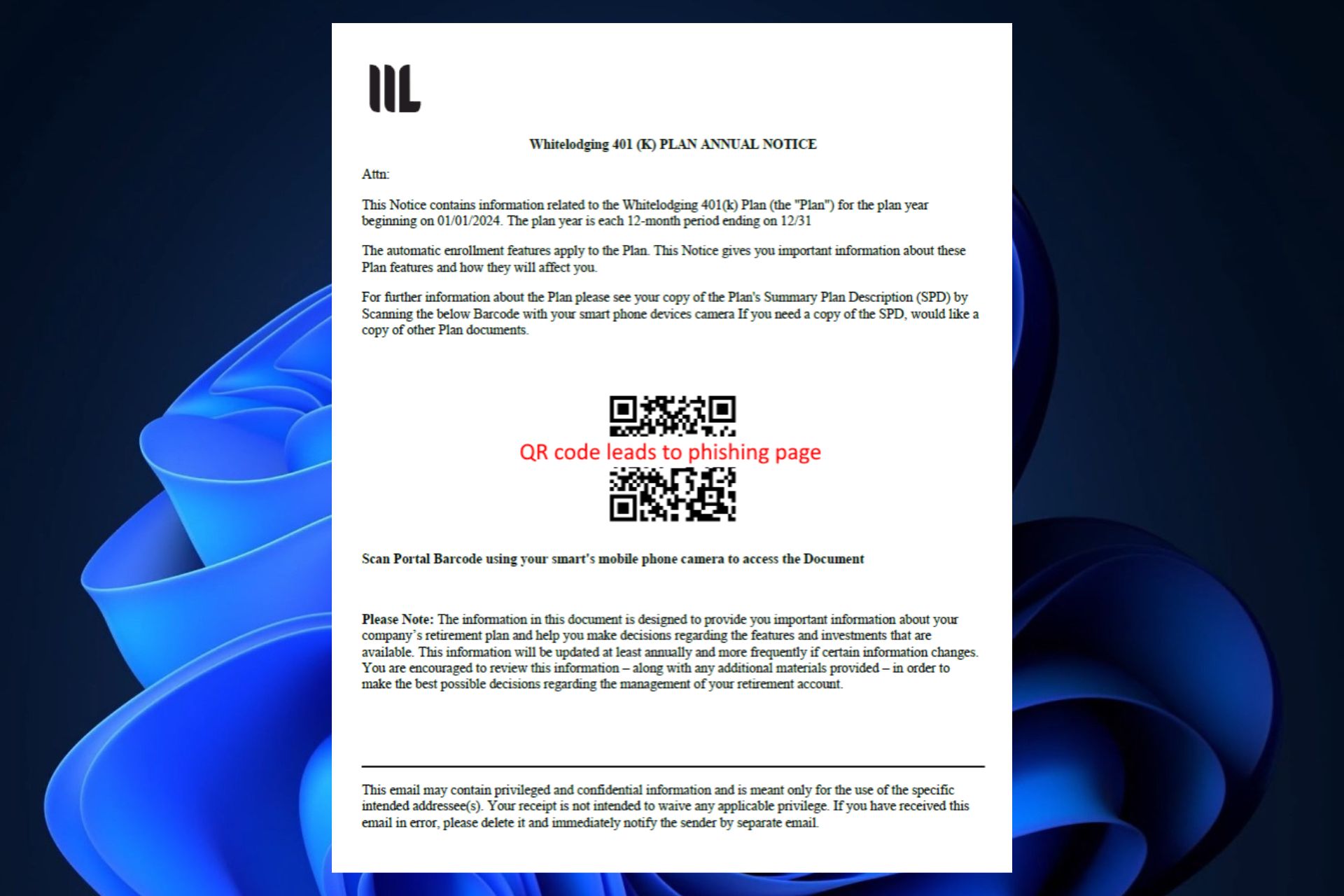
The Greatness kit allows for customizable email elements, such as names, email addresses, subjects, messages, attachments, QR codes, and engagement metrics. Plus, the kit also has systems that allow it to bypass detection measures.
Hackers are paying approximately $120 per month to use the kit, which allows for an effective emulation of various reputable services, such as imitating official Microsoft accounts.
So, users will have to pay attention to:
- Any sort of suspicious email.
- Emails that have attachments, especially HTML attachments, including, PDF, Excel, Word, archives, and executables.
- Suspicious QR codes inside emails.
- A sense of urgency in the email format. If the email asks you to do something urgently, consider it suspicious, and talk to your supervisors or management about it.
- Any sort of mentions that include access to a confidential list, or employment bonuses.
- Emails that are coming from official institutions, such as banks, partners, and so on, and the kit allows for a near-perfect emulation.
In any case, users shouldn’t open attachments in suspicious emails. Verifying and validating them with upper management is the best solution. Organizations should also consider adding an extra layer of protection by using cybersecurity tools.