Razer driver bug grants Windows admin privileges to anyone
3 min. read
Published on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team Read more
Key notes
- Now that the PrintNightmare vulnerability is over with, it was time for a new one.
- A researcher discovered a quick and neat way to gain admin privileges on any Windows device.
- All you need is a Razer mouse and you are pretty much good to go after plugging it in.
- The company was informed about this security issue and is working on fixing it ASAP.

We’ve been constantly talking about security and the steps we should take in order to keep ourselves safe from outside interference when it comes to our internet-connected devices.
But what do we do when the threat is closer than we think? And no, this is not a James Bond movie, it’s the sad and at the same time funny reality of software bugs.
The PrintNightmare fiasco has turned the eyes of the hacker community to the vulnerabilities exposed by installing 3rd party drivers.
We know it wasn’t long until other ways to intrude were found and, sure enough, someone already discovered that you can go through a wide-open door in Windows 10 by simply plugging in a Razer wireless dongle.
This bug gives you admin priveleges
Yes, you heard correctly. When plugging a Razer device into Windows 10 or Windows 11 machines, the operating system will automatically download and begin installing the Razer Synapse software on the computer.
This above-mentioned software allows users to configure their hardware devices, set up macros, or map buttons.
A researcher discovered a zero-day vulnerability in the plug-and-play Razer Synapse installation that allows users to gain system privileges on a Windows device very fast.
The gasoline on the fire, in this case, is that Razer claims the Synapse software is used by over 100 million users worldwide.
As you know, system privileges are the highest user rights available in Windows and allow someone to perform any desired command on the OS.
Thus, if anyone were to gain these high-level privileges in Windows, they attain complete control over the system and can install whatever they want, including malware.
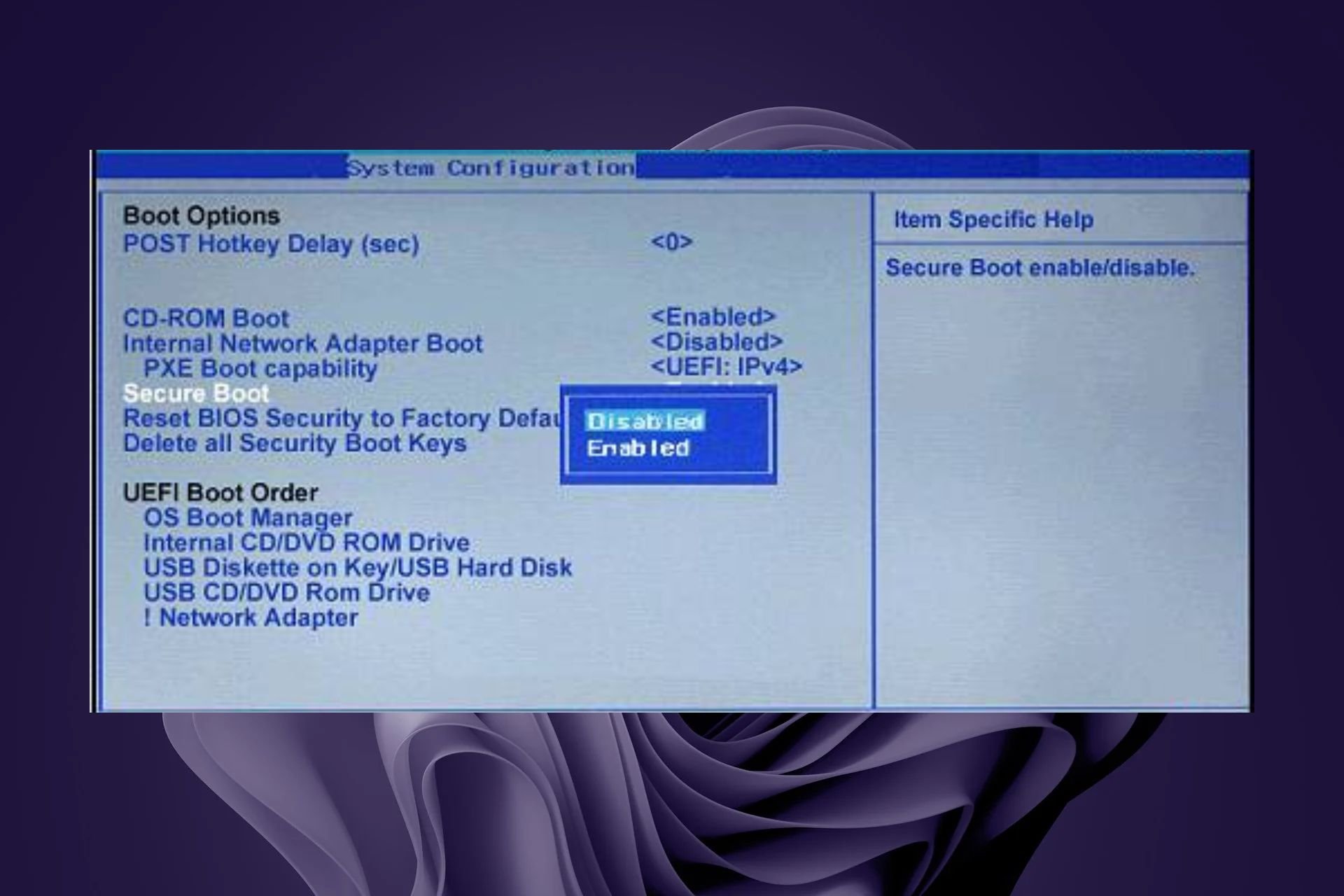
The main issue is that Windows Update downloads and executes RazerInstaller as system and that the Installer offers users the opportunity to open an Explorer window to choose where to install the drivers.
From there, there’s only one step to press shift-right-click in order to open a Powershell terminal with system privileges, and the hacker can basically do whatever he wants.
Furthermore, if the intruder goes through the installation process and defines the save directory to a user-controllable path like Desktop, the Installer saves a service binary there which can be hijacked for persistence and which is executed before user login on boot.
Another important factor to keep in mind is that the attackers do not even need a real Razer mouse, as the USB ID can be easily replicated.
Razer stated that its working on fixing this issue
After, at first, the researcher that discovered this vulnerability said he contacted Razer but didn’t receive a response, the giant hardware manufacturer got in touch with him and discussed this problem further.
Razer also told him that he would be receiving a bug bounty reward even though the vulnerability was publicly disclosed.
We’re all hoping that this problem will find its solution fast because none of us would like to become the victim of such an easy method.
However, most likely, by this time next week, both Razer and Microsoft will have provided fixing patches, designed to rid us of this vulnerability.
Were you ever the victim of malicious interference or data extraction? Let us know in the comments section below.