Ronggolawe malware: what it is, how it works, how to prevent it
3 min. read
Updated on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team. Read more

A few years ago, ransomware was scarce and not that big of a threat as it’s nowadays. After Petya and WannaCry crisis, we saw what potential it has and people suddenly started caring. Ronggolawe is not as widespread as Petya and WannaCry, but it’s still an immense threat for all web-based companies and web sites.
But, what’s Ronggolawe and how to protect from it? We’ll try to provide a valuable insight below so make sure to check it out.
What it is and how to protect from Ronggolawe ransomware
What is Ronggolawe and how it works
Ronggolawe or Ronggolawe.A (”A” refers to a variation of malicious software) is ransomware firstly introduced a year ago. It was introduced as an open-source code and uploaded to GitHub by an alleged cyber security company from Jakarta, Indonesia. No one can be sure what they intended to do with it, but you can guess that cyber criminals find it quite handy. Since it’s easily obtainable and requires minimal effort for adaptation to malicious purposes, it’s one of the most common ransomware tools nowadays.
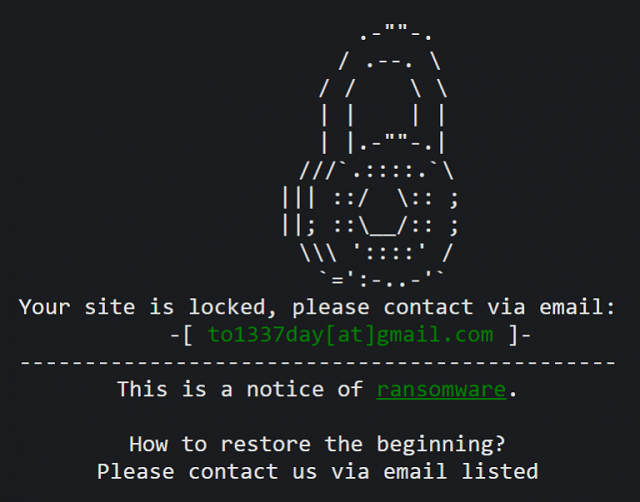
Ronggolawe’s main use is to target files stored on web servers and look for a security loophole of a kind. Once it gains the control over users’ data, it encrypts it and then, the perpetrators ask for money in order to decrypt it again. Then, they’ll offer a ”fair trade” and prompt you to contact them via the listed e-mail address. Obviously, even though you pay, there’s a risk that you’ll never see your data again.
It can come in various ways, but mostly via third-party plug-ins for supported sites, like WordPress, Magento, Blogger and similar web sites. Alternatively, it spreads via spam e-mails and links. In order to get in, Ronggolawe ransomware changes .htaccess file and reconfigures the service. Once it’s in, it produces an interface for attacker where he is able to encrypt and decrypt your files by choice. You’re immediately prompted with this pop-up web page:
That’s the moment you’ll know that the problem is real. There’s nothing you can do in the aftermath, except to pay. And still, no one can guarantee that you’ll get your data back. However, there are some ways you can protect yourself from Ronggolawe.
How to protect from Ronggolawe and ransomware in general
”Better safe than sorry” should be the mantra for all that have even the slightest chance to be affected by ransomware. Modernized hijackers have tools and knowledge to take your valuable data without too much effort. Ronggolawe is just one of the threats you can expect in everyday use, so you need a proper protection 24/7. These are some precautionary measures you should take into consideration:
- Install and keep up-to-date anti-malware software at all times. Either Windows Defender or a third-party solution.
- Keep Windows Firewall always ON.
- Enable the Cloud-based protection ON.
- Open Windows Defender.
- Choose Virus & threat protection.
- Select Virus & threat protection settings.
- Enable Cloud-based protection.
- Don’t install plug-ins from unknown sources.
- Don’t open spam e-mail. Delete it right away.
That should conclude this article. We hope you found what you were looking for. Don’t forget to tell us about your experience with Ronggolawe in the comments section below.
RELATED STORIES YOU NEED TO CHECK OUT:
- KB4012598 patches Windows XP/Windows 8 against WannaCry
- What’s the difference between WannaCry and Petya
- Prevent ransomware attacks with CyberGhost Immunizer
- Prevent future ransomware attacks with this free tool
- Wannacry and Petya push users to upgrade to Windows 10

User forum
0 messages