Here's how you can recognize a phishing attack on Teams
TeamsPhisher is popular choice for hackers when it comes to phishing attacks on Microsoft Teams.
3 min. read
Updated on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team. Read more
Key notes
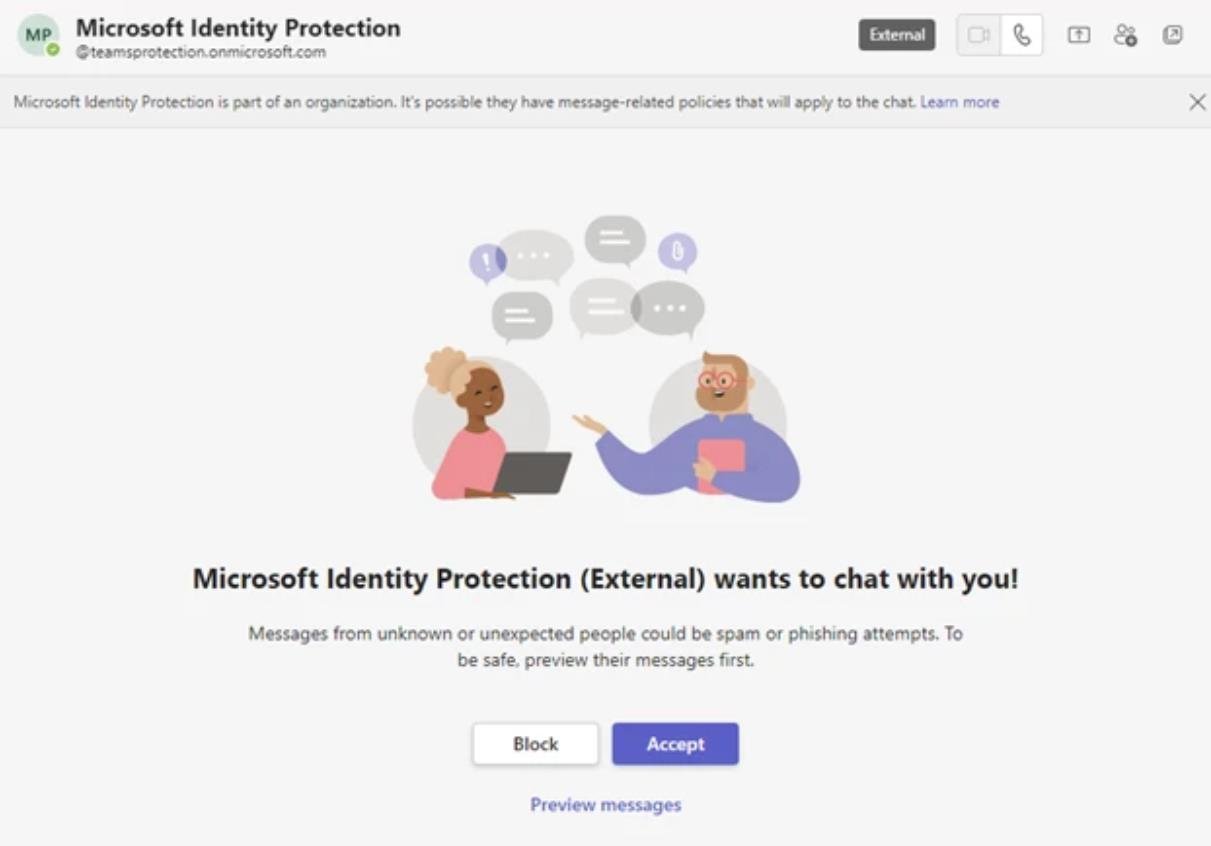
- If you get a call from a Teams member outside of your organization, be as suspicious as possible.
- You also have to be careful when reading odd-looking emails from your 'co-workers'. And don't click on weird-looking attachments.
- Microsoft Teams is a very useful tool, sure, but it's also prone to a lot of cyberattacks.

As you might know already, Microsoft Teams is not just one of the most popular apps for working environments, but it’s also one of the most targeted apps for phishing, malware, and cyberattacks, altogether.
For example, in 2022, over 80% of Microsoft Teams accounts were the target of cyberattacks. 60% of Microsoft 365 tenants were successfully hacked in 2022, so it’s safe to say Microsoft products are vulnerable and at risk.
However, there are ways to protect yourself from phishing and other malware, when using Microsoft Teams. Watching out for the TeamsPhisher tool is one of them, as this little tool is a Phyton 3 program that fully automates a cyberattack, and has become popular to use amongst hackers and threat actors.
The tool, which has a GihHub page in case you’re wondering how it works, is able to conduct phishing messages and attachments to Microsoft Teams users that allow external communications.
The TeamsPhisher tool bypasses Teams policies to enable phishing attacks
Usually, it’s not possible for any Teams users to send files or attachments outside of their organization. However, TeamsPhisher can apparently bypass this policy by making use of Teams web requests.
Hackers would need a Microsoft Business account (not personal), with a valid Teams and Sharepoint license.
According to the tool’s developers, you can easily get a Microsoft Business account:
This means you will need an AAD tenant and at least one user with a corresponding license. At the time of publication, there are some free trial licenses available in the AAD license center that fulfill the requirements for this tool.
And once you have it, there is a guide on how to effectively hack someone.
On the other side, though, things look far more formal, which creates a feeling of authority, needed for users to actually fall in the phishing trap.
This is how you can recognize a phishing attack done using the TeamsPhisher tool.
And, the tool is also used to send complex and convincing emails to Business users. These emails usually have an attachment that can be clicked. Once you do that, your account is compromised.
So, you should not answer to anyone that isn’t in your organization. Preview their messages first, and then talk to your IT managers or security managers about it.
Then, you should also be mindful about suspecting emails that seem to come from your coworkers. Look out for every odd-looking attachment, that is the first sign something is not right.
The TeamsPhisher has become quite a popular phishing tool when it comes to hacking Teams accounts, and many hackers have tried it and will still try it from now on.
But at least, you’ll know how to recognize these attacks and protect yourself accordingly.


User forum
0 messages