BitRAT malware bypasses Defender disguised as a Windows key verifier tool
2 min. read
Published on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team Read more
Key notes
- Be very careful when downloading stuff from the internet, even apparently official products.
- Security researchers at ASEC uncovered that certain Windows 10 activation tools hide more.
- In fact, one such tool harbors a dangerous cybercriminal, in the form of the BitRAT malware.
- Although everything seems to be installed as planned, your device is being seriously infected.

What should be the number one priority when accessing the internet? If you guessed anything that had to do with shopping or games, you aren’t quite there yet.
In fact, security should be our number one priority when dealing with this everchanging, dangerous online world we currently live in.
You might want to know that security research firm ASEC has discovered a new malware campaign that disguises itself in the form of a Windows product key verification tool.
However, don’t be fooled by the official disguise, as that tool is in reality BitRAT malware or a remote access trojan.
Windows activation software can seriously infect your PC
ASEC uncovered the fact that this particular RAT is being distributed via Webhards which are online file-sharing services in Korea.
Although pirated and unofficial software is often known to infect devices with malware, people tend not to take such warnings seriously.
Needless to say, this drives malware creators to step up their game and keep a constant flow of malicious software coming to the masses.
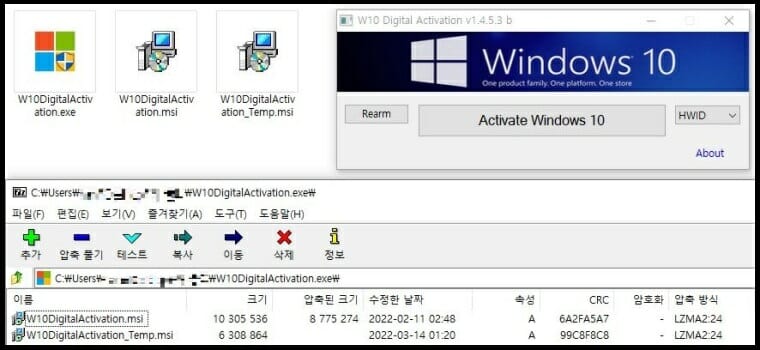
To better explain how this works, the downloaded zip file W10DigitalActivation.exe contains the dreaded file but also carries a genuine Windows activation file too.
The W10DigitalActivation_msi file is apparently real while the other W10DigitalActivation_Temp file is the malware.
The moment an unsuspecting user runs the exe file, both the actual verification tool as well as the malware file are executed simultaneously.
Of course, this action will give said user the impression that everything is working as intended and there’s really nothing shady about the whole thing.
Then, the W10DigitalActivation_Temp.exe malware file goes on to download additional malicious files from the command and control (C&C) server and delivers them inside the Windows startup program folder via PowerShell.
Finally, BitRAT is installed as the Software_Reporter_Tool.exe file inside the %temp% folder and in Windows Defender.
The exclusion path for the Startup folder and exclusion process for the BitRAT are also added, in case you were wondering.
You can find out more details about this by checking the ASEC official report. Have you downloaded such a file and had to deal with this malware?
Be sure to share your experience with us in the dedicated comments section located just below.