Event ID 4771: How to Fix Kerberos Pre-authentication Failed
Check logon audits for errors in usernames
4 min. read
Updated on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team. Read more
Key notes
- The Kerberos pre-authentication failed error indicates that the domain controller failed to authenticate the user.
- This may be due to the user intentionally entering an incorrect password, or it may indicate that an unauthorized person is attempting to access your network.
- Always ensure you have a stable internet connection for verification to take place.
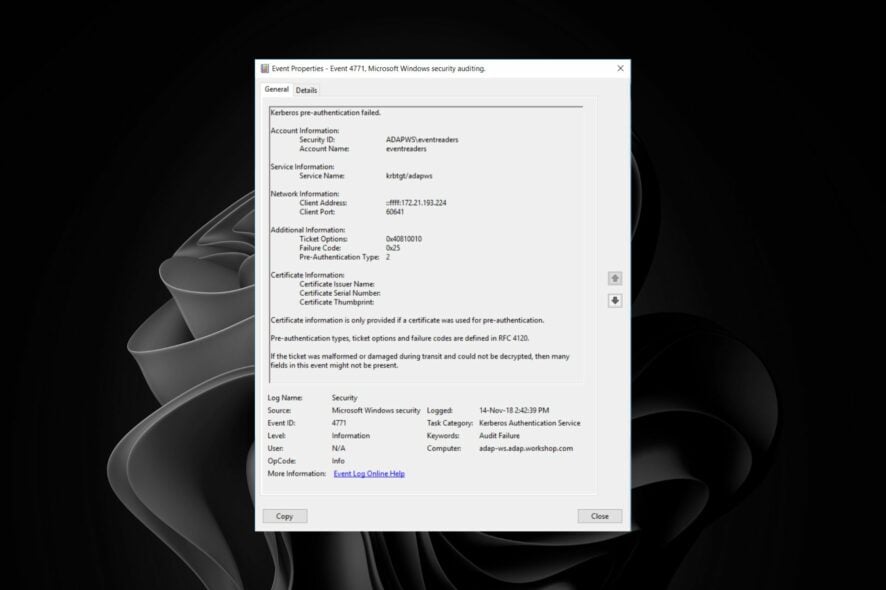
The Kerberos pre-authentication failed error indicates that the user cannot log in to Windows or any other network resource. This error occurs when there’s a problem with the Kerberos pre-authentication process.
It can occur if you use an incorrect username or password if your computer is offline or not connected to the network, or if an error occurs when connecting to a domain controller.
Why am I getting the Event ID 4771 error?
This error means that you tried to connect to a server using Kerberos pre-authentication, but the server did not respond to your request. In Windows, Kerberos pre-authentication verifies a user’s credentials before the KDC authenticates them.
If the pre-authentication fails, the user will be prompted for their password. For some users, the error code was Event ID 4771. Kerberos pre-authentication failed 0x18 on their PCs. For this code, the issue is a bad password. However, for Event ID 4771, this can happen for several reasons:
- Server clock mismatch – The likely cause is that your computer’s clock is out of sync with the server’s clock. This can happen if your computer was offline for a long time and returned online but failed to synchronize its clock.
- Incorrect password – Most users who encountered the Event ID 4771 error admitted to having recently changed their passwords. However, for unique IDs such as Event ID 4771 status 0x12, it means that the user’s credentials have been revoked.
- Cached credentials – Cached credentials are used to reduce login times and to improve security because they’re obtained automatically from the directory server. However, when you changed passwords, they may cause conflicts.
- Wrong domain – Make sure that you’re logging on to an account from the same domain as the computer you’re connecting from; otherwise, there will be no way for Active Directory to verify your credentials correctly.
How can I solve the Event ID 4771 error?
1. Enable failed logon auditing
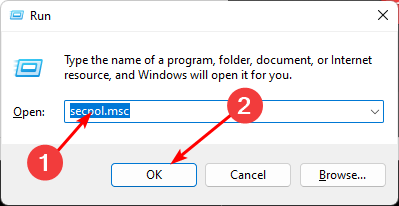
- Hit the Windows + R keys to open the Run command.
- Type secpol.msc in the dialog box and hit Enter.
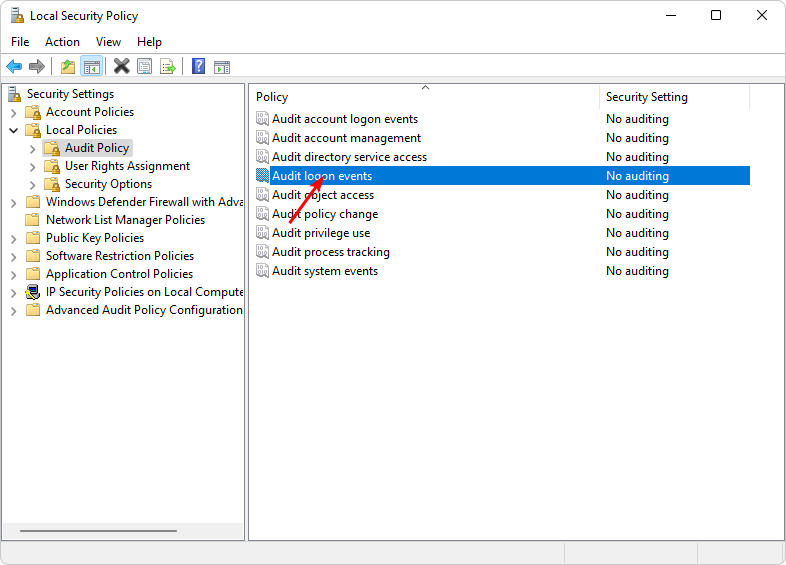
- Navigate to the following location:
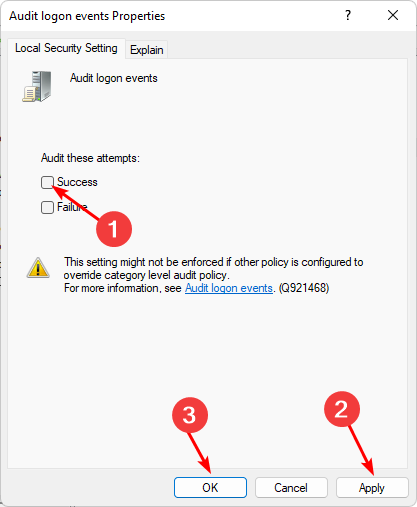
Security settings/Local Policy/Audit Policies/Audit Logon Events - Double-click on Audit logon events, select Success/Failure, then click on Apply and OK.
This will generate a security event whenever a user attempts to log into a domain-joined computer and fails. Failed logon auditing will allow you to see when users have attempted to log onto the network unsuccessfully and to identify any duplicates.
Then, you can rename the accounts with duplicate names on one or more servers, or create new accounts for them with unique names.
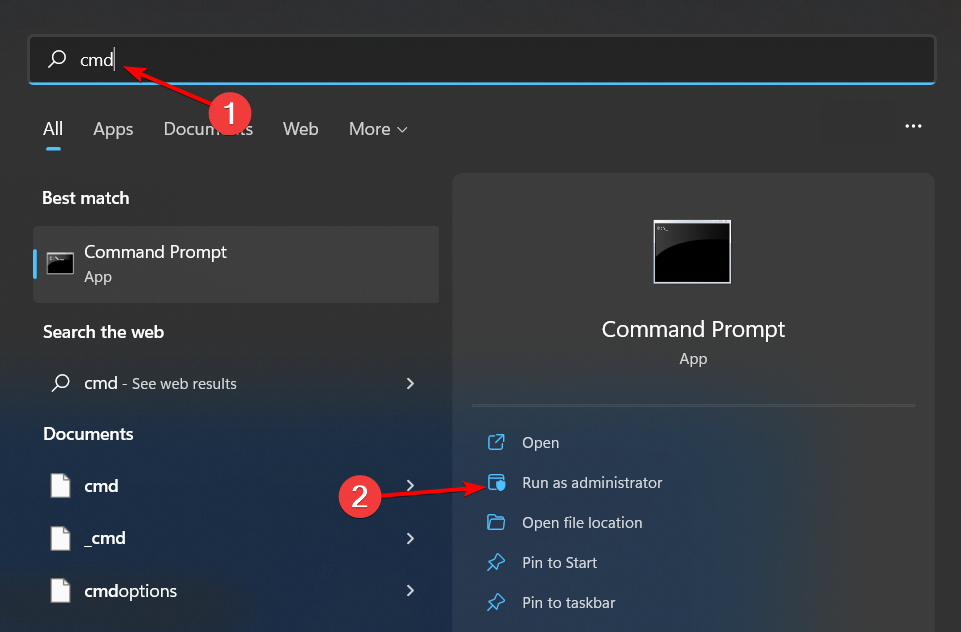
2. Delete cached passwords
- Hit the Windows key, type cmd in the search bar and click Open.
- Type the following commands and hit Enter after each one:
psexec -i -s -d cmd.exerundll32 keymgr.dll KRShowKeyMgr - A list of stored usernames and passwords will appear. Delete them from your server and restart your PC.
This happens because the Kerberos subsystem caches the old password in memory. When you change the password, it doesn’t get cleared from memory until it expires.
The Kerberos client then tries to use the old cached password, which doesn’t work because it has been changed on the domain controller.
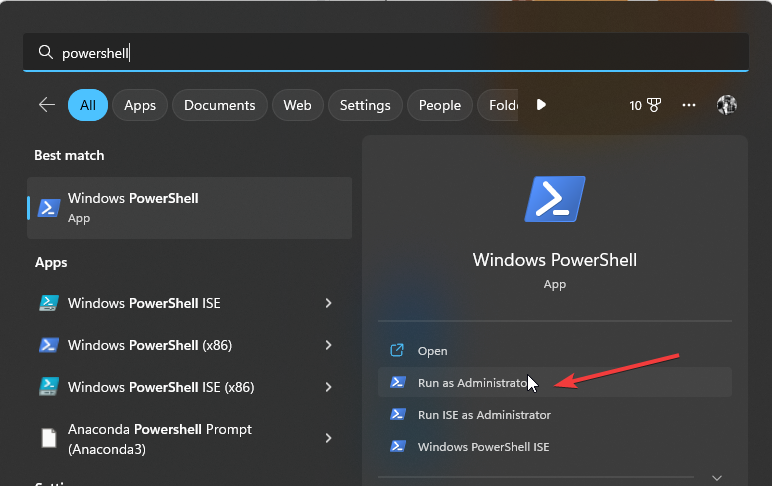
3. Enable audit logon
- Hit the Windows key, type Powershell in the search bar and click Run as administrator.
- Type the following command and hit Enter:
auditpol /set /subcategory:”logon” /failure:enable
When you enable logon auditing, it helps you determine if someone is trying to gain unauthorized access to your systems by guessing passwords or attempting other brute-force attacks.
Hopefully, you have bypassed the Event ID 4771 Kerberos pre-authentication failed error with one of these methods.
You may also come across an Event ID 4768, where your Kerberos authentication ticket is requested. If so, don’t hesitate to check out our expert article.
In the comment section below, let us know what solution fixed this error for you.

User forum
0 messages