Abandoned URLs can set Microsoft Entra ID on fire
The dangerous vulnerability was discovered by SecureWorks, earlier this year.
3 min. read
Published on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team Read more
Key notes
- An attacker would simply hijack an abandoned URL and use it to gain elevated privileges.
- The vulnerability was discovered by SecureWorks, a cybersecurity firm.
- Microsoft addressed it right away, however, it speaks volumes about its level of cybersecurity.
Earlier this year, Microsoft Entra ID (which by then was known as Azure Active Directory) could have been easily hacked and compromised by hackers using abandoned reply URLs. A team of researchers from SecureWorks discovered this vulnerability and alerted Microsoft.
The Redmond-based tech giant quickly addressed the vulnerability and within 24 hours of the initial announcement, it removed the abandoned reply URL in Microsoft Entra ID.
Now, almost 6 months after this discovery, the team behind it, uncovered in a blog post, the process that lies behind infecting abandoned reply URLs and using them to set Microsoft Entra ID on fire, essentially compromising it.
Using the abandoned URL, an attacker could easily gain elevated privileges of the organization using Microsoft Entra ID. Needless to say, the vulnerability posed a great risk, and Microsoft was apparently unaware of it.
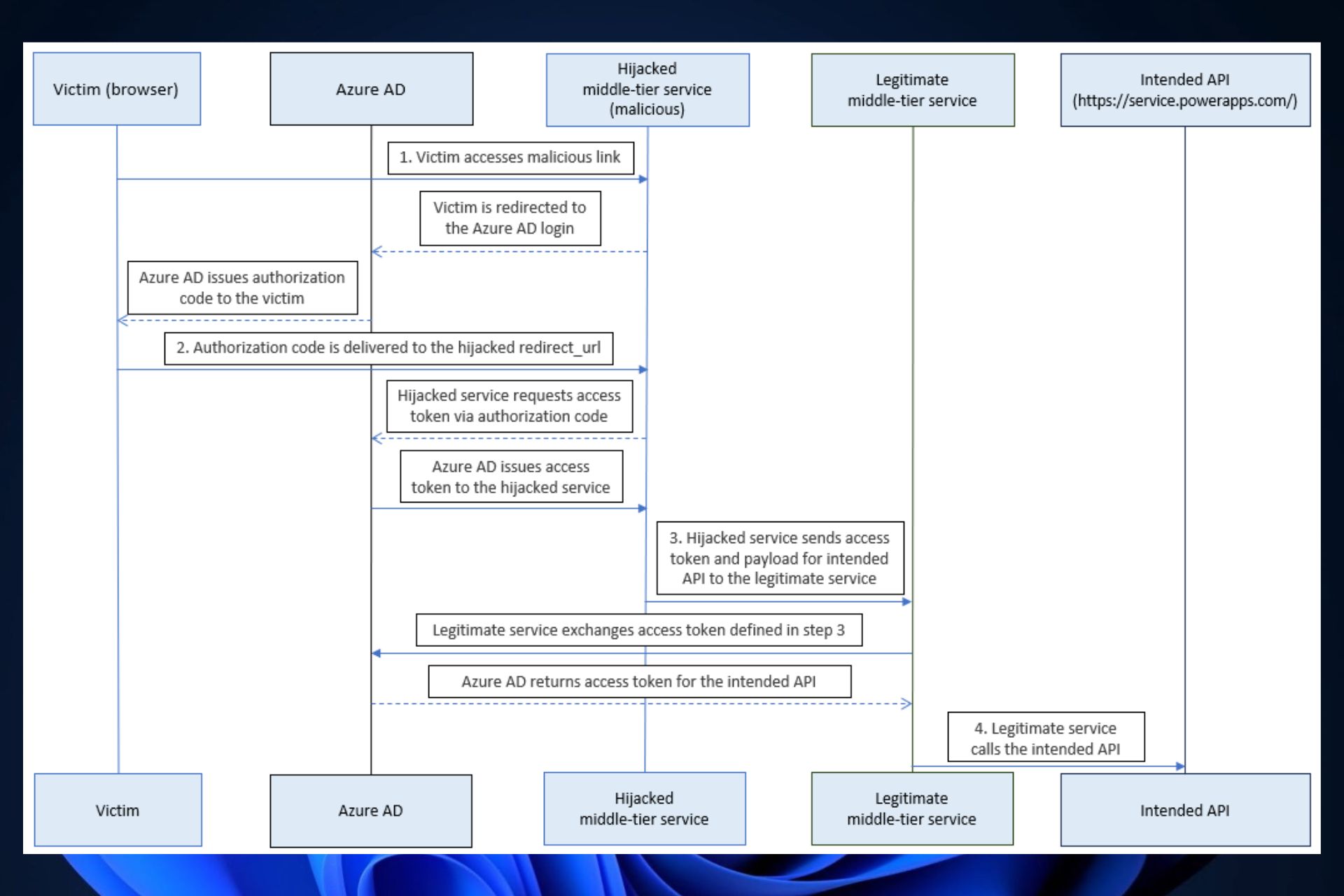
An attacker could leverage this abandoned URL to redirect authorization codes to themselves, exchanging the ill-gotten authorization codes for access tokens. The threat actor could then call Power Platform API via a middle-tier service and obtain elevated privileges.
SecureWorks
This is how an attacker would take advantage of the Microsoft Entra ID vulnerability
- The abandoned reply URL would be discovered by the attacker and hijacked with a malicious link.
- This malicious link would then be accessed by a victim. Entra ID would then redirect the victim’s system to the reply URL, which would also include the authorization code in the URL.
- The malicious server exchanges the authorization code for the access token.
- The malicious server calls the middle-tier service using the access token and intended API, and the Microsoft Entra ID would end up being compromised.
However, the team behind the research also discovered that an attacker could simply exchange the authorization codes for access tokens without relaying tokens to the middle-tier service.
Given just how easily would have been for an attacker to effectively compromise Entra ID servers, Microsoft quickly addressed this issue, and it released an update to it on the following day.
But it’s quite interesting to see how the Redmond-based tech giant never saw this vulnerability to begin with. However, Microsoft does have a history of somewhat neglecting vulnerabilities.
Earlier this summer, the company was heavily criticized by Tenable, another prestigious cybersecurity firm, for failing to address another dangerous vulnerability that would allow malignant entities to access the bank information of Microsoft users.
It’s clear that Microsoft needs to somehow expand its cybersecurity department. What do you think about it?