Windows 10 January Patch Tuesday [DIRECT DOWNLOAD LINKS]
15 min. read
Published on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team. Read more
Key notes
- The first round of Patch Tuesday updates of 2021 have finally hit live.
- The article below acts as an in-depth changelog for each cumulative update.
- Additionally, we will be providing you with direct download links for each update.
- Apply these updates to benefit from the latest features, changes, and security improvements!

2021 is here, and with it, the promise of new features and improvements come to Windows 10 as an OS.
The first steps in that direction is the current January Patch Tuesday updates, as they are the first round of major updates of the year.
Nothing much has changed in terms of update delivery, or at least Microsoft didn’t announce anything regarding the matter, so the January Patch Tuesday updates have arrived according to schedule.
Because there are many versions of Windows 10, both newer and older, still in use, each individual cumulative update is a bit different from the rest.
That is precisely why we compiled this dedicated article where will we will be providing you with a changelog for all cumulative updates that will be arriving this month.
As a bonus, we will also provide you with direct downlaod links towards each cumulative update, straight from the Windows Update Catalog!
Changes included in the January Patch Tuesday Updates

Windows 10, version 20H2
As of the writing of this article, Windows 10 v20H2 is the latest major version of Windows 10, and as such has the most experimental features on it.
Fortunately, most bugs that were first present when it was first made available have been weeded out, and this version of Windows 10 is far more stable.
That being said, you should upgrade to this version as soon as possible if your hardware allows it (the system requirements are the same as with Windows 10 v2004).
If you haven’t updated to Windows 10 v20H2, know that it is easiest to update if you already have Windows 10 v2004. Check out this in-depth guide on how to get Windows 10 v20H2 as fast as possible.
Cumulative update name:
Improvements and fixes:
- Addresses a security vulnerability issue with HTTPS-based intranet servers. After installing this update, HTTPS-based intranet servers cannot, by default, use a user proxy to detect updates. Scans using these servers will fail if you have not configured a system proxy on the clients. If you must use a user proxy, you must configure the behavior using the policy “Allow user proxy to be used as a fallback if detection using system proxy fails.” To ensure the highest levels of security, also use Windows Server Update Services (WSUS) Transport Layer Security (TLS) certificate pinning on all devices. This change does not affect customers who are using HTTP WSUS servers. For more information, see Changes to scans, improved security for Windows devices.
- Addresses a security bypass vulnerability that exists in the way the Printer Remote Procedure Call (RPC) binding handles authentication for the remote Winspool interface. For more information, see KB4599464.
- Security updates to Windows App Platform and Frameworks, Windows Media, Windows Fundamentals, Windows Kernel, Windows Cryptography, Windows Virtualization, Windows Peripherals, and Windows Hybrid Storage Services.
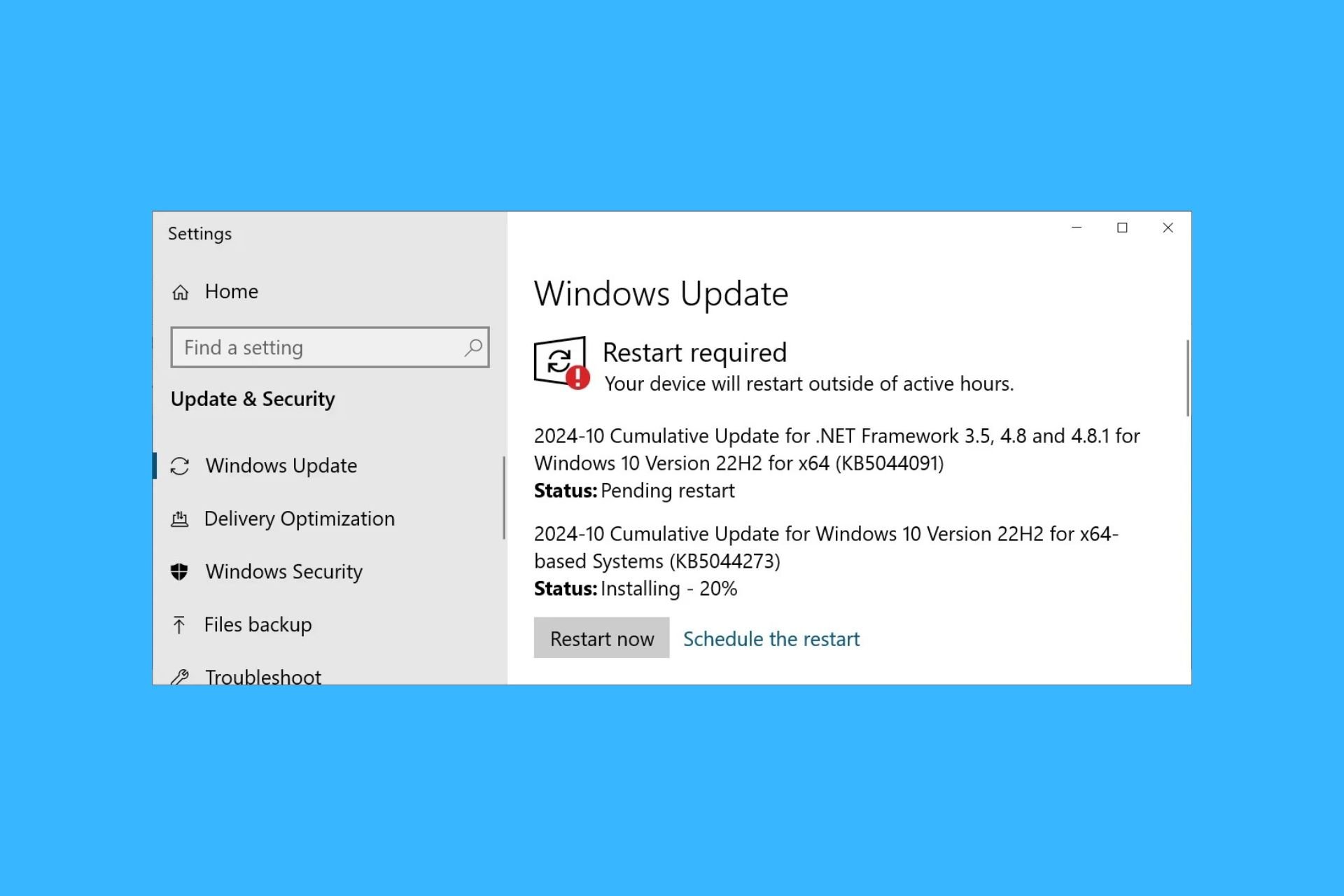
Known Issues:
- System and user certificates might be lost when updating a device from Windows 10, version 1809 or later to a later version of Windows 10. Devices will only be impacted if they have already installed any Latest cumulative update (LCU) released September 16, 2020 or later and then proceed to update to a later version of Windows 10 from media or an installation source which does not have an LCU released October 13, 2020 or later integrated. This primarily happens when managed devices are updated using outdated bundles or media through an update management tool such as Windows Server Update Services (WSUS) or Microsoft Endpoint Configuration Manager. This might also happen when using outdated physical media or ISO images that do not have the latest updates integrated.
- Note Devices using Windows Update for Business or that connect directly to Windows Update are not impacted. Any device connecting to Windows Update should always receive the latest versions of the feature update, including the latest LCU, without any extra steps.
- When using the Microsoft Japanese Input Method Editor (IME) to enter Kanji characters in an app that automatically allows the input of Furigana characters, you might not get the correct Furigana characters. You might need to enter the Furigana characters manually.
- Note The affected apps are using the ImmGetCompositionString() function.
[DIRECT DOWNLOAD LINK]
Windows 10, version 2004
Windows 10 v2004 shares the same core system as Windows 10 v20H2, so all updates, fixes and improvements applied to one is the same with the other.
Cumulative update name:
Improvements and fixes:
- Same As Windows 10 V20H2
Known Issues:
- Same As Windows 10 V20H2
[DIRECT DOWNLOAD LINK]
Windows 10, version 1909
Windows 10 v1909 shares a core structure, core operating system, and an identical set of system files with Windows 10 v1903.
Because of this, all cumulative updates that apply to one version are available to the other as well.
Cumulative update name:
Improvements and fixes:
- Addresses a security vulnerability issue with HTTPS-based intranet servers. After installing this update, HTTPS-based intranet servers cannot, by default, use a user proxy to detect updates. Scans using these servers will fail if you have not configured a system proxy on the clients. If you must use a user proxy, you must configure the behavior using the policy “Allow user proxy to be used as a fallback if detection using system proxy fails.” To ensure the highest levels of security, also use Windows Server Update Services (WSUS) Transport Layer Security (TLS) certificate pinning on all devices. This change does not affect customers who are using HTTP WSUS servers. For more information, see Changes to scans, improved security for Windows devices.
- Addresses a security bypass vulnerability that exists in the way the Printer Remote Procedure Call (RPC) binding handles authentication for the remote Winspool interface. For more information, see KB4599464.
- Addresses an issue that might damage the file system of some devices and prevent them from starting up after running chkdsk /f.
- Security updates to Windows App Platform and Frameworks, Microsoft Graphics Component, Windows Media, Windows Fundamentals, Windows Kernel, Windows Cryptography, Windows Virtualization, Windows Peripherals, and Windows Hybrid Storage Services.
Known Issues:
- System and user certificates might be lost when updating a device from Windows 10, version 1809 or later to a later version of Windows 10. Devices will only be impacted if they have already installed any Latest cumulative update (LCU) released September 16, 2020 or later and then proceed to update to a later version of Windows 10 from media or an installation source which does not have an LCU released October 13, 2020 or later integrated. This primarily happens when managed devices are updated using outdated bundles or media through an update management tool such as Windows Server Update Services (WSUS) or Microsoft Endpoint Configuration Manager. This might also happen when using outdated physical media or ISO images that do not have the latest updates integrated.
- Note Devices using Windows Update for Business or that connect directly to Windows Update are not impacted. Any device connecting to Windows Update should always receive the latest versions of the feature update, including the latest LCU, without any extra steps.
[DIRECT DOWNLOAD LINK]
Windows 10, version 1903
Windows 10 v1903 shares a core structure, core operating system, and an identical set of system files with Windows 10 v1909.
Because of this, cumulative updates that apply to one version are available to the other as well.
Cumulative update name:
Improvements and fixes:
- Same as Windows 10 v1909
Known Issues:
- Same as Windows 10 v1909
[DIRECT DOWNLOAD LINK]
Windows 10, version 1809
According to Microsoft, users that still have the Home, Pro, Pro for Workstation, and IoT Core editions of Windows 10 V1809 should know that it reached End of Service back in November 2020.
That is why it is advised that you update your OS to a newer, supported version.
Cumulative update name:
Improvements and fixes:
- Addresses a timing issue on print servers that might send print jobs to the wrong print queue.
- Addresses a security vulnerability issue with HTTPS-based intranet servers. After installing this update, HTTPS-based intranet servers cannot, by default, use a user proxy to detect updates. Scans using these servers will fail if you have not configured a system proxy on the clients. If you must use a user proxy, you must configure the behavior using the policy “Allow user proxy to be used as a fallback if detection using system proxy fails.” To ensure the highest levels of security, also use Windows Server Update Services (WSUS) Transport Layer Security (TLS) certificate pinning on all devices. This change does not affect customers who are using HTTP WSUS servers. For more information, see Changes to scans, improved security for Windows devices.
- Addresses a security bypass vulnerability that exists in the way the Printer Remote Procedure Call (RPC) binding handles authentication for the remote Winspool interface. For more information, see KB4599464.
- Addresses an issue that might damage the file system of some devices and prevent them from starting up after running chkdsk /f.
- Security updates to Windows App Platform and Frameworks, Microsoft Graphics Component, Windows Media, Windows Fundamentals, Windows Kernel, Windows Cryptography, Windows Virtualization, Windows Peripherals, and Windows Hybrid Storage Services.
Known Issues:
- After installing KB4493509, devices with some Asian language packs installed may receive the error, “0x800f0982 – PSFX_E_MATCHING_COMPONENT_NOT_FOUND.”
[DIRECT DOWNLOAD LINK]
Windows 10, version 1803
Microsoft first announced that Windows 10 v1803 will reach the end of mainstream support, and starting with July there wouldn’t be any more optional, non-security releases for this version of Windows 10.
Because of the current global pandemic, as well as user feedback, Microsoft decided to extend the support for Windows 10 v1803 up until 2021.
Cumulative update name:
Improvements and fixes:
- Extends Microsoft Defender for Endpoint support to new regions.
- Addresses a security vulnerability issue with HTTPS-based intranet servers. After installing this update, HTTPS-based intranet servers cannot, by default, use a user proxy to detect updates. Scans using these servers will fail if you have not configured a system proxy on the clients. If you must use a user proxy, you must configure the behavior using the policy “Allow user proxy to be used as a fallback if detection using system proxy fails.” To ensure the highest levels of security, also use Windows Server Update Services (WSUS) Transport Layer Security (TLS) certificate pinning on all devices. This change does not affect customers who are using HTTP WSUS servers. For more information, see Changes to scans, improved security for Windows devices.
- Addresses a security bypass vulnerability that exists in the way the Printer Remote Procedure Call (RPC) binding handles authentication for the remote Winspool interface. For more information, see KB4599464.
- Security updates to Windows App Platform and Frameworks, Microsoft Graphics Component, Windows Media, Windows Fundamentals, Windows Kernel, Windows Cryptography, Windows Virtualization, Windows Peripherals, and Windows Hybrid Storage Services.
Known Issues:
- Microsoft is not currently aware of any issues with this update.
[DIRECT DOWNLOAD LINK]
Windows 10, version 1703
Note: Windows 10, version 1703 has reached the end of service for Home, Pro, Pro for Workstation, and IoT Core editions.
In order to continue receiving quality and security updates, Microsoft recommends that you get the latest possible version of Windows 10 installed.
Cumulative update name:
Improvements and fixes:
- Addresses a security vulnerability issue with HTTPS-based intranet servers. After installing this update, HTTPS-based intranet servers cannot, by default, use a user proxy to detect updates. Scans using these servers will fail if you have not configured a system proxy on the clients. If you must use a user proxy, you must configure the behavior using the policy “Allow user proxy to be used as a fallback if detection using system proxy fails.” To ensure the highest levels of security, also use Windows Server Update Services (WSUS) Transport Layer Security (TLS) certificate pinning on all devices. This change does not affect customers who are using HTTP WSUS servers. For more information, see Changes to scans, improved security for Windows devices.
- Addresses a security bypass vulnerability that exists in the way the Printer Remote Procedure Call (RPC) binding handles authentication for the remote Winspool interface. For more information, see KB4599464.
- Security updates to Windows App Platform and Frameworks, the Microsoft Graphics Component, Windows Media, Windows Fundamentals, the Windows Kernel, Windows Cryptography, Windows Virtualization, Windows Core Networking, Windows Peripherals, Windows Hybrid Storage Services, and the Windows Remote Desktop.
Known Issues:
- Microsoft is not currently aware of any issues with this update.
[DIRECT DOWNLOAD LINK]
Windows 10, version 1607
Note: Windows 10, version 1607 has reached the end of service for all of its available editions. Update to the latest version of Windows 10 in order to keep your system protected.
Cumulative update name:
Improvements and fixes:
- Adds the ability to set a Group Policy to show only the domain and username when a user signs in.
- Addresses an issue that delays authentication traffic because of Netlogon scalability issues.
- Addresses an issue in which a principal in a trusted MIT realm fails to obtain a Kerberos service ticket from Active Directory domain controllers (DC). This occurs on devices that installed Windows Updates that contain CVE-2020-17049 protections and configured PerfromTicketSignature to 1 or higher. These updates were released between November 10, 2020 and December 8, 2020. Ticket acquisition also fails with the error, “KRB_GENERIC_ERROR”, if callers submit a PAC-less Ticket Granting Ticket (TGT) as an evidence ticket without providing the USER_NO_AUTH_DATA_REQUIRED flag.
- Addresses a security bypass vulnerability that exists in the way the Printer Remote Procedure Call (RPC) binding handles authentication for the remote Winspool interface. For more information, see KB4599464.
- Addresses a security vulnerability issue with HTTPS-based intranet servers. After installing this update, HTTPS-based intranet servers cannot, by default, use a user proxy to detect updates. Scans using these servers will fail if you have not configured a system proxy on the clients. If you must use a user proxy, you must configure the behavior using the policy “Allow user proxy to be used as a fallback if detection using system proxy fails.” To ensure the highest levels of security, also use Windows Server Update Services (WSUS) Transport Layer Security (TLS) certificate pinning on all devices. This change does not affect customers who are using HTTP WSUS servers. For more information, see Changes to scans, improved security for Windows devices.
- Addresses an issue in the Remote Desktop Protocol (RDP) redirector (rdpdr.sys) that causes a stop error.
- Security updates to the Windows App Platform and Frameworks, Microsoft Graphics Component, Windows Media, Windows Fundamentals, Windows Cryptography, Windows Virtualization, Windows Peripherals, and Windows Hybrid Storage Services.
Known Issues:
- After installing KB4467684, the cluster service may fail to start with the error “2245 (NERR_PasswordTooShort)” if the group policy “Minimum Password Length” is configured with greater than 14 characters.
[DIRECT DOWNLOAD LINK]
Windows 10, version 1507
Note: Windows 10, version 1507 is the oldest version of Windows 10 still active, and it has reached the end of service for some time now.
If your hardware allows it, update to a much newer version of Windows 10.
Cumulative update name:
Improvements and fixes:
- Addresses a security vulnerability issue with HTTPS-based intranet servers. After installing this update, HTTPS-based intranet servers cannot, by default, use a user proxy to detect updates. Scans using these servers will fail if you have not configured a system proxy on the clients. If you must use a user proxy, you must configure the behavior using the policy “Allow user proxy to be used as a fallback if detection using system proxy fails.” To ensure the highest levels of security, also use Windows Server Update Services (WSUS) Transport Layer Security (TLS) certificate pinning on all devices. This change does not affect customers who are using HTTP WSUS servers. For more information, see Changes to scans, improved security for Windows devices.
- Addresses a security bypass vulnerability that exists in the way the Printer Remote Procedure Call (RPC) binding handles authentication for the remote Winspool interface. For more information, see KB4599464.
- Security updates to Windows App Platform and Frameworks, Microsoft Graphics Component, Windows Media, Windows Management, Windows Fundamentals, Windows Cryptography, Windows Virtualization, Windows Peripherals, and Windows Hybrid Storage Services.
Known Issues:
- Microsoft is not currently aware of any issues with this update.
[DIRECT DOWNLOAD LINK]
That wraps up our complete changelog covering the changes from this month’s round of updates.
Keep in mind that these aren’t the only updates that are coming, since smaller tweaks and fixes are most likely to come in the following days, and another set of updates will arrive in about two weeks.
Remember that the main purpose of these updates is to improve your security, so we advise you to update as soon as they arrive in your region.
By doing so, you should be better prepared for unofficial events like Exploit Wednesday or Uninstall Thursday, a term that describe the days that follow the updates where hackers target those that haven’t applied the latest patches.
To learn more about Patch Tuesday and how you can better prepare for applying them, check out this detailed guide.
Have you updated your PC with the latest cumulative updates? Let us know if the experience went smoothly by leaving us your feedback in the comments section below.
[wl_navigator]





User forum
0 messages