Outlook vulnerability allows hackers to steal password hashes
3 min. read
Updated on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team Read more

Microsoft Outlook is one of the most popular email platforms in the world. I personally rely on my Outlook email address for work-related as well as personal tasks.
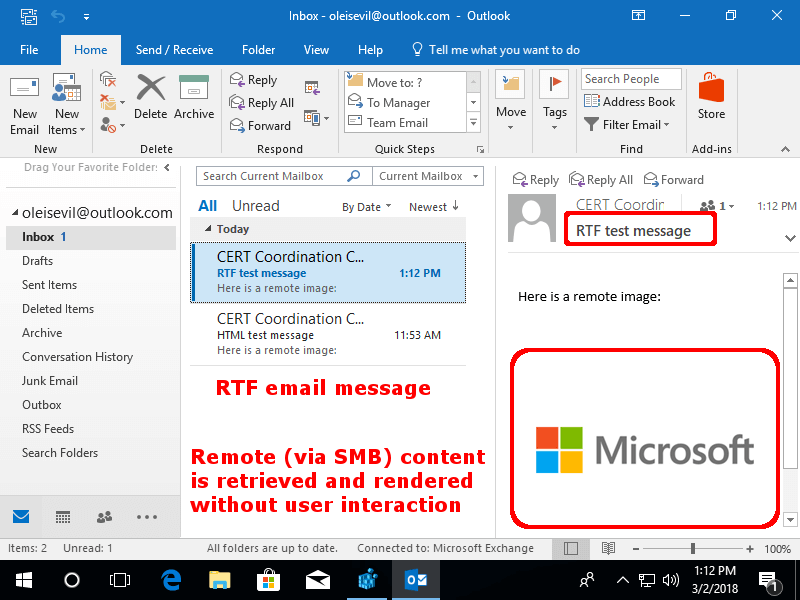
Unfortunately, Outlook may not be as secure as we users would like to think. According to a report published by the Carnegie Mellon Software Engineering Institute, Outlook comes with a security bug that could trigger password hash leaks when users preview a Rich Text Format emails that contains remotely hosted OLE objects.
Watch your Outlook password
This security vulnerability exists because the Redmond giant doesn’t use strict content verification and restrictions when loading items from a remote SMB server. On the other hand, the same vulnerability cannot be exploited when accessing web-hosted content as Microsoft applies much stricter restrictions when dealing with this type of content.
Outlook doesn’t load web-hosted images in emails in order to protect users’ IP addresses. However, when users access RTF email messages that contain OLE objects loaded from a remote SMB server, Outlook does load the respective images.
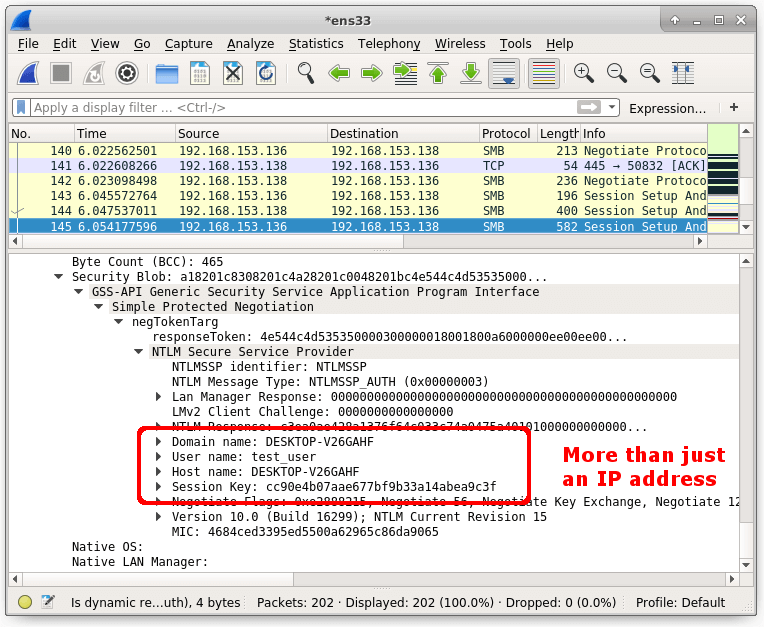
This leads to a series of leaks that include IP address, domain name, and more as the reports explains:
Outlook blocks remote web content due to the privacy risk of web bugs. But with a rich text email, the OLE object is loaded with no user interaction. […] Here we can see than an SMB connection is being automatically negotiated. The only action that triggers this negotiation is Outlook previewing an email that is sent to it. […] I can see that the following things are being leaked: IP address, domain name, user name, host name, SMB session key. A remote OLE object in a rich text email messages functions like a web bug on steroids!
Microsoft partially fixes the problem
Microsot recently rolled out a hotfix on Patch Tuesday to fix this security issue. Unfortunately, this solution is not 100% safe as it fails to block all remote SMB attacks.
Once this fix is installed, previewed email messages will no longer automatically connect to remote SMB servers. This fix helps to prevent the attacks outlined above. It is important to realize that even with this patch, a user is still a single click away from falling victim to the types of attacks described above. For example, if an email message has a UNC-style link that begins with “\\”, clicking the link initiates an SMB connection to the specified server.
Additional security measures are required in order to block remote SMB attacks. For example, admins can block specific TCP ports for all SMB sessions and Outlook users should use complex passwords.
RELATED STORIES TO CHECK OUT: