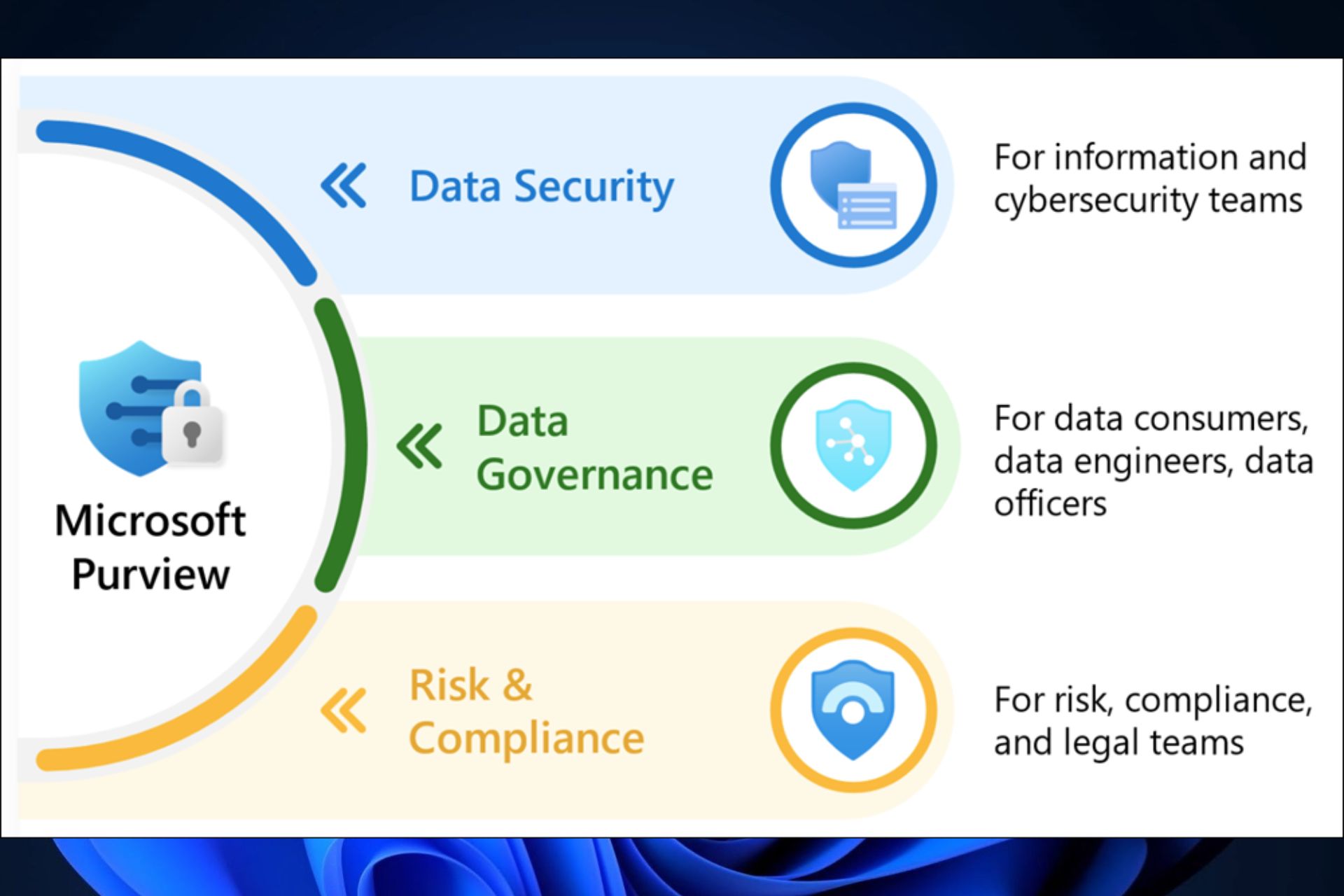
Windows Server Build 26212 introduces dMSA allowing organizations to migrate from traditional accounts to machine accounts
Build 26212 is now live!
2 min. read
Published on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team Read more
Microsoft released Build 26212 (the same version was released to the Canary channel, as well) to Windows Server 2025, and with it, the Redmond-based tech giant finally introduced the long-speculated dMSA (Delegated Managed Service Accounts) capability.
For those of you who don’t know, the dMSA account type allows a safe and secure migration from a traditional service account to a machine account, by using fully randomized keys, while disabling account passwords.
Using dMSA can stop people from stealing credentials using a hacked account (a problem known as kerberoasting), which is a common problem with old-style service accounts, and one Microsoft intends to address, according to the official changelog.
[NEW] Delegated Managed Service Accounts (dMSA)
A new account type known as delegated Managed Service Account (dMSA) is now available that allows migration from a traditional service account to a machine account with managed and fully randomized keys, while disabling original service account passwords.
Authentication for dMSA is linked to the device identity, which means that only specified machine identities mapped in AD can access the account. Using dMSA helps to prevent harvesting credentials using a compromised account (kerberoasting), which is a common issue with traditional service accounts.
Microsoft
dMSA in Windows was initially noticed at the end of last year, and then, a few months later, Microsoft officially confirmed it. Now, it’s available to preview for Windows Servers insiders.
Alongside the new dMSA, Windows Server Build 26212 also introduced more SMB (Server Message Block) protocol changes, including:
- SMB over QUIC client and server disable: Administrators can now disable the SMB over QUIC client and SMB over QUIC server options with Group Policy and PowerShell.
- SMB over QUIC client and server connection auditing: Successful SMB over QUIC client and SMB over QUIC server connection events are now written to the event log to include the QUIC transport.
- SMB signing and encryption auditing: Administrators can now enable auditing of the SMB server and client for support of SMB signing and encryption. This shows if a third-party client or server doesn’t support SMB encryption or signing. You can configure these settings with PowerShell and Group Policy.
You can read the full changelog here, and you can download the latest Windows Server Build 26212 here.