Thousands affected in the latest WordPress brute force attack, poses a challenge for cyber experts
It started of as a Web3 Crypto Malware
3 min. read
Published on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team Read more
Cyber attacks are getting advanced in nature, and it’s becoming increasingly difficult to tackle them. In the latest developments, a new WordPress brute force attack is employing the end user’s browser to target thousands of websites.
First reported by Sucuri Security, the new brute force attack is an advanced iteration of the already prevalent Web3 Crypto Wallet Drainers, an active threat for over a month that uses drainers to steal crypto assets from compromised wallets.
According to Sucuri Security, the new 3Kb long script, dynamic-linx[.]com/chx.js, has been injected on over 700 websites and counting. Once a website is compromised, attackers can automatically use the visitors’s web browser to attack more, and the chain continues!
The challenge for cyber security experts here is filtering requests from real, legitimate users who were exposed to such websites.
How does the attack work?
It’s a complex multi-step process, and we have tried to break it down for you in simple terms:
- Threat actors identify WordPress websites that can be compromised, extract details of admins with access to them, and then inject the dynamic-linx[.]com/chx.js script.
- When you open a compromised webpage, the script gets into motion, your browser asks hxxps://dynamic-linx[.]com/getTask.php for a task. The task is basically conducting a brute-force attack on another website using the provided set of credentials.
- If the brute-force attack from the end user’s browser succeeds, it automatically creates and sends a small text file with the correct credentials to the threat actors.
- Once a task is completed, another is automatically shared with the browser, which continues until the infected webpage remains open.
For the unversed, a Brute Force Attack works by bombarding the authentication servers with a wide array of login credentials (starting with simpler ones and then moving to complex sets) with the hope that one would work.
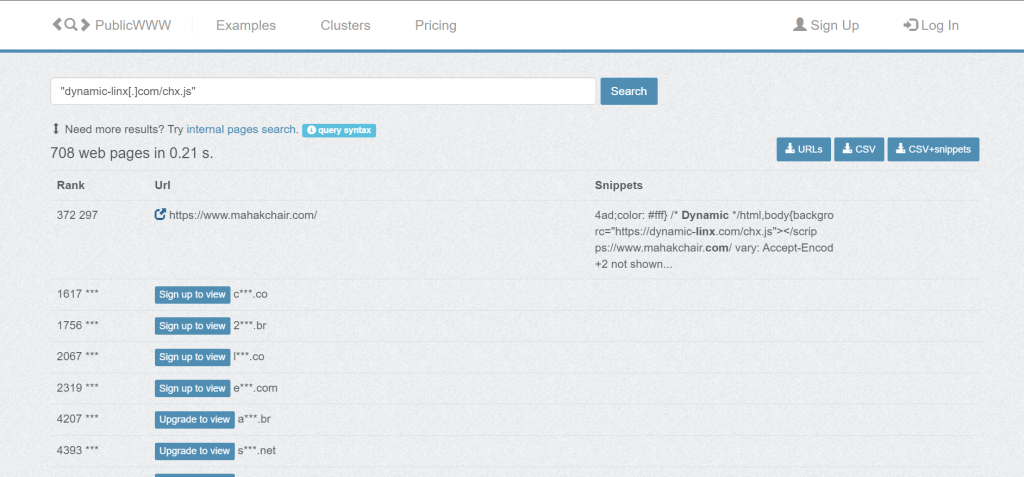
According to Sucuri Security, the only plausible reason why threat actors moved from Web3 Crypto Wallet Drainers to WordPress brute force attacks is that the former couldn’t be scaled and was easy to detect. As a result, infected websites were soon blocked.
So, threat actors could be trying to infect as many websites with different unnoticeable scripts before launching an attack that’s more profitable.
Measures to prevent the attack
At present, with minimal information about the scale and intricacy of the WordPress brute force attack, having a secure password and deploying IP-based restrictions on access to critical parts of the website could help.
Brute force attacks are getting complex in nature, and protecting your website or data is becoming all the more difficult. So, it’s time you gear up and choose an advanced website security software!
For users, a combination of an antivirus and firewall will provide the necessary web-based protection. Besides, practicing good cyber hygiene will keep you safe from similar attacks.
If you know more about the attack that could help our readers, share it in the comments section.