Microsoft Teams became a phishing highway for DarkGate malware
Don't open any files from users outside your organization in Microsoft Teams!
3 min. read
Published on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team Read more
According to a cybersecurity threat report from AT&T, the Microsoft Teams app chats are used to spread the DarkGate malware using phishing techniques.
The experts detected over 1.000 phishing messages from a single attacker in their investigation. This was possible because Microsoft enabled External Access to company chats by default and that allows anyone in the organization to add any users in chats, even if they are outsiders.
How does the Microsoft Teams DarkGate phishing attack work?
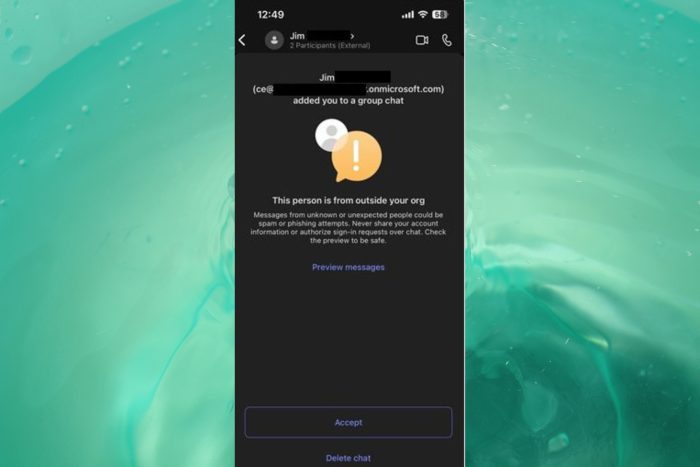
You’re one of the users in an organization when you suddenly get a message from someone you don’t know, asking you to install a file with a double extension such as filename.pdf.msi. So, you might be tempted to think that it’s a PDF document from one of your colleagues, but in fact, it’s a known tactique for the DarkGate malware attack.
Although Microsoft Teams will alert you that the person is outside your org, the attacker seems a seemingly legitimate origin, coming from the .onmicrosoft.com domain name.
An important detail to note here is the “.onmicrosoft.com” domain name. This domain, by all appearances, is authentic and most users would probably assume that it is legitimate. OSINT research on the domain also shows no reports for suspicious activity, leading the MDR SOC team to believe the username (and possibly the entire domain) was likely compromised by the attackers prior to being used to launch the phishing attack.
Cites the AT&T report
Once you click on the file and install the .msi file, the malware will connect the infected system to its command-and-control server from hgfdytrywq[.]com, which, according to PaloAlto Networks, is a confirmed component of the DarkGate malware infrastructure.
How can I avoid getting infected with DarkGate in Microsoft Teams?
The External Access feature shouldn’t be enabled by default in Microsoft Teams and if it does, the system admins should configure the clients to ban the access of outside users from their organization chats.
Furthermore, as with any other phishing threats, the users in the organization have to be advised on how to react when this kind of events occur, whether it’s about Microsoft Teams or other company channels of communication.
Don’t accept any files from untrusted users, don’t open them and, most of all, don’t install them.
Right now, Microsoft 365 users are also targeted by phishing attacks so we also recommending to always be on alert.
Have you been the victim of a Microsoft Teams phishing attack or the DarkGate malware? Tell us all about it in the comments section below.