What is Audit Success in Windows: How to Improve Security
A deep dive into Windows auditing
4 min. read
Updated on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team Read more
Key notes
- Windows audit success events let administrators analyze network activity and react to security problems.
- The audit success monitors and records computer activity to enhance security and compliance.
Do you want to learn about Windows audit success? Here is all you should know. Windows auditing is a critical security feature that allows administrators to track and monitor user activity on a Windows-based system.
Also, this includes recording events such as logins, file access, and changes to system settings. Furthermore, tracking and monitoring these events is essential for various reasons, including compliance with regulations, troubleshooting, and identifying security threats.
So, in this article, we will discuss the importance of Windows auditing and examine what audit success is in the context of the Windows operating system.
What is Windows auditing?
Windows auditing is an essential tool for ensuring the security and integrity of a Windows-based system. It provides a detailed record of user activity for identifying and addressing security threats and compliance with regulations.
There are several advantages of using Windows auditing to track and monitor user activity on a Windows-based system, including:
- Security – Windows auditing allows administrators to identify and address security threats by providing a detailed record of user activity. This can detect and respond to unauthorized access and monitor potential security breaches.
- Compliance – Windows auditing helps organizations to comply with various regulations, such as HIPAA, PCI-DSS, and SOX, by providing a comprehensive record of user activity to demonstrate compliance.
- Troubleshooting – Windows auditing can help troubleshoot system problems by providing a detailed record of user activity. This can be useful for identifying the cause of a problem, as well as for determining the best course of action to resolve it.
- Forensics – Windows auditing can be used for forensic purposes, allowing administrators to reconstruct past events and understand how security breaches occurred. This can help identify the cause of a problem and determine the best course of action to resolve it.
Note that tools like AD Manager Plus play an important role in Windows audit success. Firstly, it allows you to view, track and report on all Active Directory changes, user activities, and security events in real time.
Also, it helps to automate the process of creating, modifying, and deleting user accounts, as well as resetting passwords, enabling or disabling accounts, and managing group membership.

ADManager Plus
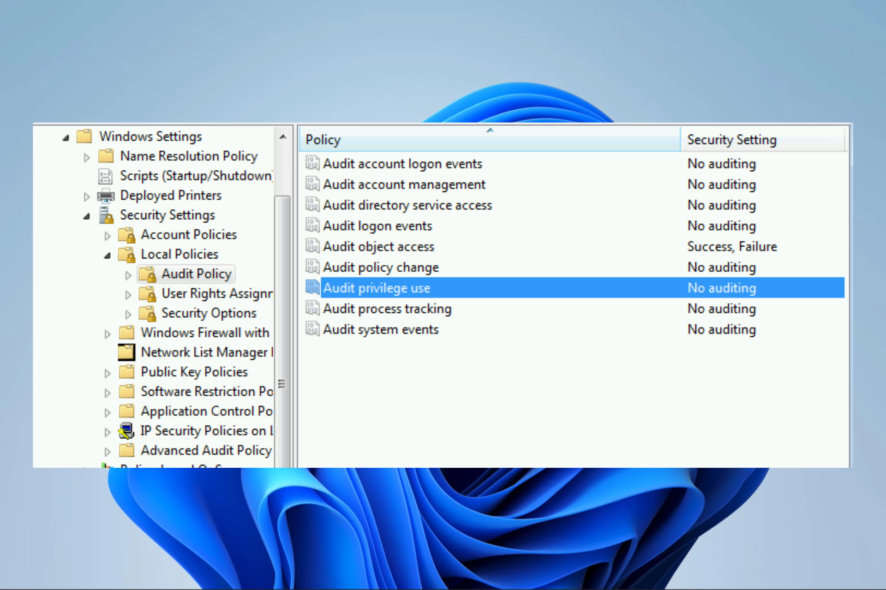
Useful in conjunction with other tools and practices to achieve comprehensive Windows audit success.What is Windows audit success?
1. How it works
Windows audit success events recording is done in the Windows event log. The event log is a system-wide log that records events that occur on a computer, such as a system startup and shutdown, security events, and application events.

Audit success events recording stays in the security event log, one of the three main event logs in Windows (the other two are the application event log and the system event log).
An administrator must first configure the audit policy settings on the computer or network to enable auditing.
These settings determine which actions require auditing and which events require logging into the event log. After configuring the audit policy settings, the operating system will begin tracking and recording the specified actions and events.
Audit success events recording in the event log show up as event ID 4648. The event log entry includes the following:
- Information about the user who performed the action
- The date and time of the action
- The resources that were affected
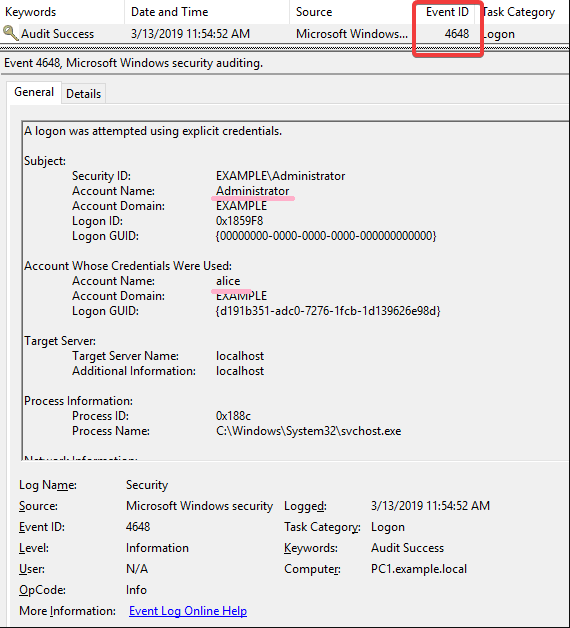
This information can identify who acted when it was performed and what resources were affected.
2. Use Windows Audit Success to Improve Security and Compliance
Auditing can improve security and compliance in several ways. For example, audit success events are useful for the following:
- Identify security breaches – Audit success events can identify suspicious activity and potential security breaches. For example, it logs an audit success event if a user logs in to a computer using an account without the authority to access the system.
- Detect suspicious activity – Audit success events detect suspicious activity on a computer or network. For example, it logs audit success events if users access a file or resource they do not typically access.
- Improve compliance – Audit success events improve compliance with regulatory standards. For example, if an organization is subject to HIPAA regulations, audit success events track access to protected health information (PHI).
- Improve incident response – Audit success events improve incident response. For example, if an incident such as a security breach occurs, audit success events determine actions taken and by whom.
Windows audit success is a powerful tool that improves security and compliance.
Audit success events can identify security breaches, detect suspicious activity, and improve compliance with regulatory standards by tracking and recording specific actions on a computer system or network.
Hope you have found this guide helpful. Lastly, let us know your thoughts in the comments below.