Windows Updates are used to spread malware by Lazarus hackers
2 min. read
Published on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team. Read more
Key notes
- Windows Updates are used by Microsoft to strengthen the defense of our systems.
- However, you might want to know that even these updates are no longer safe to use.
- A North Korean-backed hacker group called Lazarus managed to compromise them.
- All victims have to do is open the malicious attachments and enable macro execution.

Owning an official, up-to-date copy of the Windows operating system gives us a certain degree of safety, considering that we get security updates on a regular basis.
But have you ever thought, that the updates themselves could be used against us one day? Well, it seems like that day has finally come, and experts warn us about the possible implications.
Recently, North Korean hacking group called Lazarus managed to use the Windows Update client to execute malicious code on Windows systems.
North Korean hacker group compromised Windows Updates
Now, you’re probably wondering in what circustances this latest ingenious cyberattack scheme was uncovered.
The Malwarebytes Threat Intelligence team did, while analyzing a January spearphishing campaign impersonating the American security and aerospace company Lockheed Martin.
Attackers instrumenting this campaign made sure that, after the victims open the malicious attachments and enable macro execution, an embedded macro drops a WindowsUpdateConf.lnk file in the startup folder and a DLL file (wuaueng.dll) in a hidden Windows/System32 folder.
The next strep is for the LNK file to be used used to launch the WSUS / Windows Update client (wuauclt.exe) to execute a command that loads the attackers’ malicious DLL.
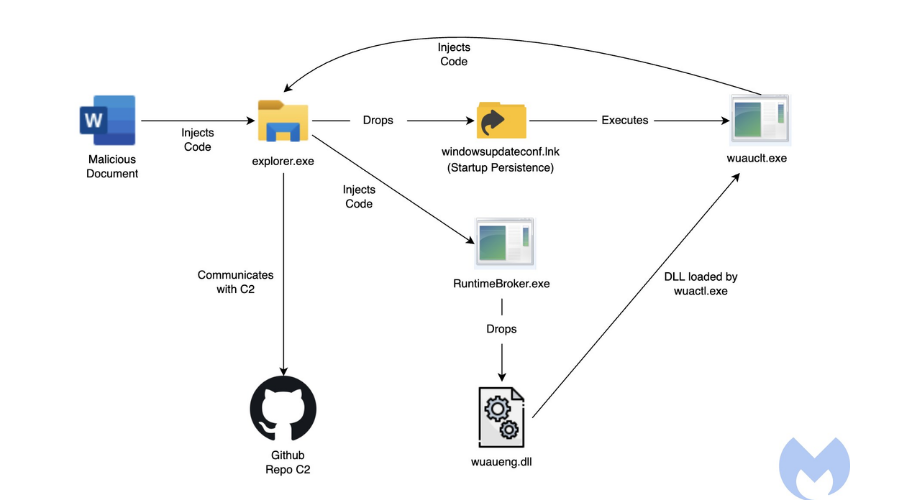
The team behind uncovering these attacks linked them to Lazarus based on existing evidence, including infrastructure overlaps, document metadata, and targeting similar to previous campaigns.
Lazarus keeps updating its toolset to evade security mechanisms and will surely continue to do so, by employing techniques such as the use of KernelCallbackTable to hijack the control flow and shellcode execution.
Couple that with the usage of the Windows Update client for malicious code execution, along with GitHub for C2 communication, and you have the recipee for a complete and utter disaster.
Now that you know that this threat is real, you can take more safety precautions and avoid falling victim to malicious third parties.
Has your machine ever been infected with dangerous malware through a Windows update? Share your experience with us in the comments section below.



User forum
0 messages