How to Allow Internet Access Through an Azure Firewall
It's all about creating a subnet and routing it properly
3 min. read
Updated on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team. Read more
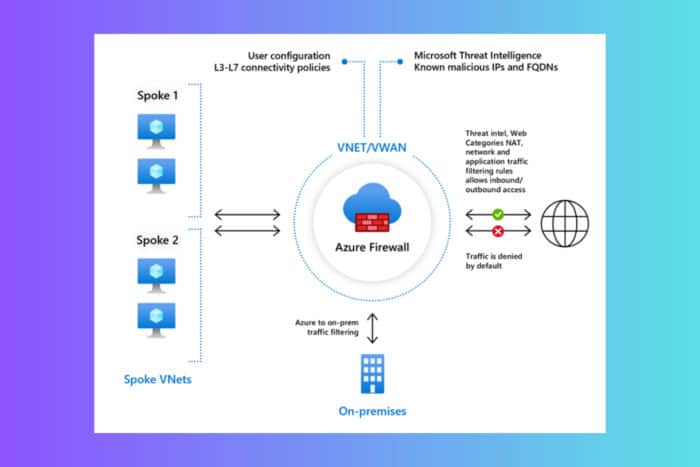
It might sound complicated to allow internet access through Azure Firewall, but our step by step guide below will get you through it without skipping a beat.
How to I allow internet traffic through Azure Firewall?
1. Create an Azure Firewall
- Open a browser, go to the Azure portal and log in with your credentials.
- Select Create a resource > Networking > Firewall.
- Fill in the required details such as Resource Group, Name, Region, and Firewall Policy.
- Click Review + create and then Create.
In case you already have an Azure Firewall, skip this step.
2. Create a Firewall Subnet and add a Route
- In Azure, navigate to your Virtual Network.
- Select Subnets > + Subnet.
- Name the subnet AzureFirewallSubnet.
- Specify a subnet address range (at least /26 in size), then click Save.
- After creating the subnet, deploy the firewall into this subnet.
- Go to the Firewall you created.
- Under Settings, select Public IP configuration and associate a public IP address.
- Go to All services > Route tables > + Add.
- Fill in the required details and create the route table.
- Once created, go to the route table and select Routes > + Add.
- Add a route with the following details:
- Route name: AllowAllOutbound
Address prefix: 0.0.0.0/0
Next hop type: Virtual appliance
Next hop address: The private IP address of your Azure Firewall.
- Route name: AllowAllOutbound
- To associate the Route Table with the Subnet, go to the Subnets section of your route table.
- Click + Associate and select the subnet you want to route through the firewall.
3. Create a Network rule in Azure Firewall
- Go to your Azure Firewall.
- Under Settings, select Rules > Network rule collection > + Add network rule collection.
- Fill in the required details:
- Name: AllowAllOutbound
Priority: 100 (or any priority that fits your rule set)
Action: Allow
- Name: AllowAllOutbound
- Add a rule with the following details:
- Name: AllowAll
Protocol: Any
Source: Any
Destination: 0.0.0.0/0
Destination Ports: *
- Name: AllowAll
4. Verify the configuration
Finally, it’s time to verify the configuration you just set up. For that, double check if the route table is correctly associated with the subnet.
Check that the network rule is active and correctly configured in the Azure Firewall. Test the outbound traffic from a VM in the subnet to ensure it routes through the firewall.
This setup will route all outbound traffic from the specified subnet through the Azure Firewall, allowing all outbound traffic as per the configured rules.
Hoping that your Azure Firewall is working well, you might also be interested in our guide on how to download and set up Azure Virtual Desktop.
have you heard about the Azure Video indexer? Click the highlighted link to learn all about it.
If you have any specific requirements or encounter any issues, feel free to ask in the comments below.

User forum
0 messages