FIX: The requested resource is in use [Error Solved]
7 expert-tested solutions to get rid of the SmartService Trojan
9 min. read
Updated on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team Read more
Key notes
- The Requested resource is in use error message can appear when your computer is infected with the SmartService Trojan.
- To remove it, make sure to uninstall any malicious software from your computer.
- Start your PC in Safe Mode and perform a full scan with a dedicated malware solution.
- To prevent the infection in the future, try to avoid freeware sites, and check any external devices for viruses.

This message The requested resource is in use looks harmless when it first pops up on your computer screen. But, if it appears on your PC every time you try to open a program, it should worry you.
The error message is usually a warning for something quite serious – a Trojan horse malware that is called SmartService.
The Trojan horse‘s name is, sadly, well earned. The malware behaves in a very smart way, from the multiple ways it can worm itself onto your PC and expose it to threats.
Like other destructive malware, its strain can leave a trail of damage that includes: installing programs that steal your personal information, spying on your online activity, and relaying the data to hackers.
This all sounds scary. But the Trojan‘s reign of terror does not end there. Without a doubt, its most destructive effect is the ability to block the antivirus software installed on your computer.
By doing this, the malware opens the door for other viruses and malware to infect your computer.
The compound effect is your computer becomes an inlet through which cybercriminals can have free passes over your banking and other personal information.
Because of this ability to infiltrate computers and, at the same time, disabling their malware defenses, SmartService is often the weapon of choice for ransomware attackers.
It also messes with your browser. Your browsing experience will be characterized by constant popups, annoying redirects, and dubious browser extensions.
From the point your PC gets infected, the virus can sit there for a long time before you even notice anything unusual.
During that whole time, the Trojan will be busy at work, stealing your personal information, spying on you, and installing vicious software on your computer.
It is thus horrifying to imagine the malware may already be done with whatever malicious act it was charged with by the time you detect it.
In this article, we’ll discuss ways of removing the Trojan if you have unfortunately been hit already. First, let’s look at the ways the malware can infect your computer.
How the SmartService malware infects your computer
Seeing how difficult it usually is to detect this Trojan infection and how destructive it is, prevention is indeed better than cure, in many ways than one.
The most effective way to avoid infection is to be vigilant in the way you use your own and interact with other computers.
SmartService can infiltrate your PC in any one of the following ways: malicious attachments to emails delivered to your inbox, or ads you click on the websites you visit.
You can also get it from infected files you install as part of the software downloaded from the Internet, content you download from social media, cookies on torrents’ platforms, and other freeware sites.
Quick Tip:
Most often this error can be caused by malware, and we all know that the only effective way to deal with malware is via reliable antivirus software.
That being said, we recommend that you try out an AI-based antivirus, as it will stop all manner of cyber-threats before they even enter your PC, so you never have errors again.

ESET HOME Security Essential
Prevent the infection with malware, trojan, and other viruses, with one of the best cyber security options.How to fix The requested resource is in use error?
1. Restart your computer in Safe Mode
In the case of SmartService, the error message itself is evidence of system contamination. Rebooting in Safe Mode is a good way of running your antivirus without being blocked. Safe Mode prevents the malware from running as this mode only runs the PC’s basic services.
1. Press the Windows key to open Windows Search.
2. Type msconfig in the search box.
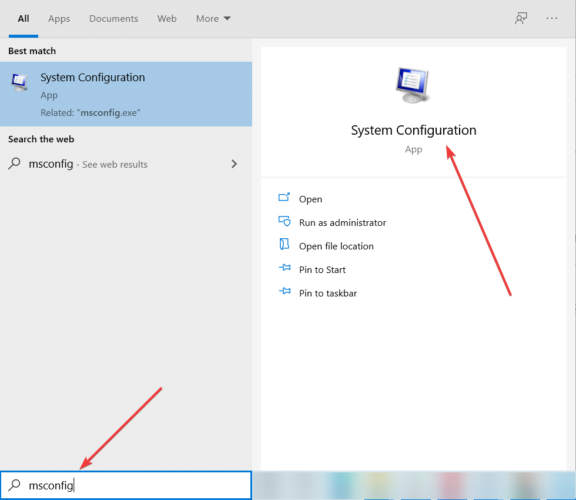
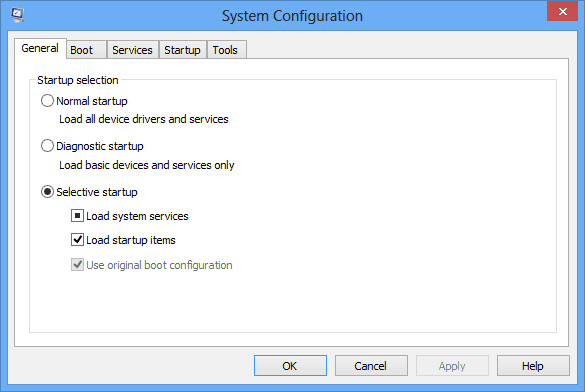
3. The System Configuration app will now open.
4. Navigate to the Boot folder. You should see the Boot options listed at the bottom.
5. Choose the Safe Boot option. It should have the Minimal sub-option already checked.
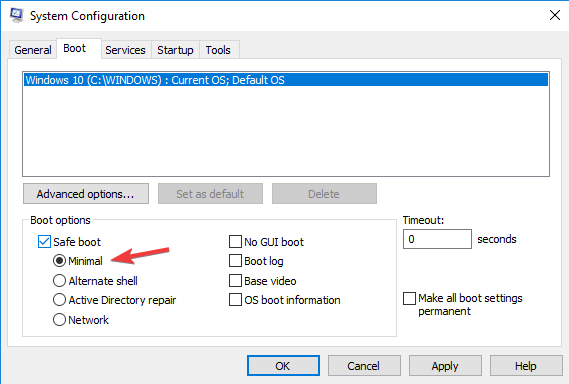
6. Click OK after you make your selection.
7. A popup screen will appear. Just choose Restart and your computer should safely reboot in Safe Mode.
If Windows 10 Safe Mode is not working and your computer starts normally, you can use our dedicated guide to fix the issue.
2. Use third-party malware removal software
We have mentioned already how the SmartService trojan can bypass some antivirus software as if they are not even there.
This means you can’t just use any antivirus software to scan or remove this rather sophisticated malware. It will simply respond with it is annoying The requested resource is in use error message.
However, there are other quality malware removal software tools you can use. We recommend you to try any of these best anti-malware software.
Bear in mind, in order to unlock the malware removal features with some of these tools, you will have to buy the license.
Just as well, you may want to be sure that the antivirus will itself not be blocked by the trojan before you spend money buying the license.
Still, you can prevent this from happening by first rebooting the PC in Safe Mode. Most malware removal tools come with instructions to guide you through installation to actual malware removal.
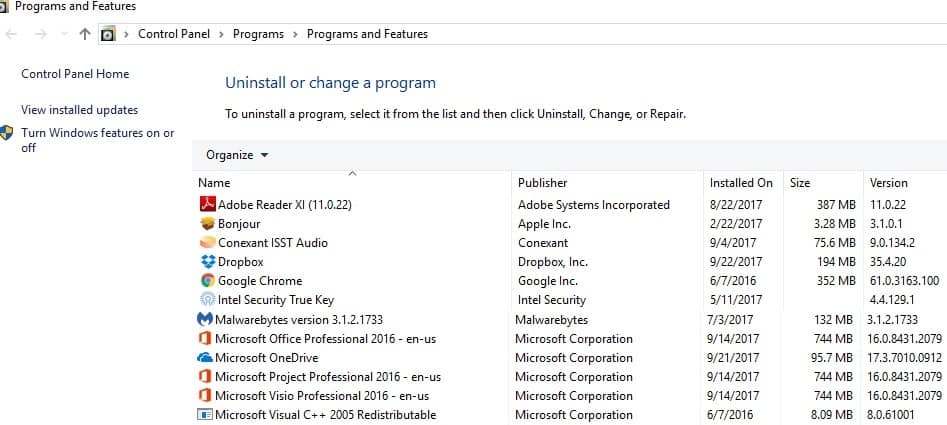
3. Uninstall malicious programs
- Open the Run dialog box by pressing the Windows and the R key simultaneously.
- Type in appwiz.cpl and hit enter.
- This will open the Programs and Features folder, from which you can identify and uninstall all programs maliciously installed by the trojan horse.
You should be able to tell which programs you have installed yourself from the ones maliciously installed by the malware.
Uninstall all suspicious-looking programs whose purpose you can’t verify. One of them might be the cause of The requested resource is in use malware. Afterward, proceed to the next step below.
However, many apps can’t be completely removed. Thus, we recommend you to use any of these best uninstaller software to get rid of residual files left behind.
4. Scan the System Configuration folder for malicious software
- To open the System Configuration folder, click the Windows startup icon and type msconfig in the search bar and press Enter.
- Click the Startup option and a list of all programs that start running as soon as you start your PC will appear.
- Look out for those whose manufacturer is marked as Unknown.
- There is a good chance all these are malware.
- If they were indeed important, their publisher would be happy to be identified with them.
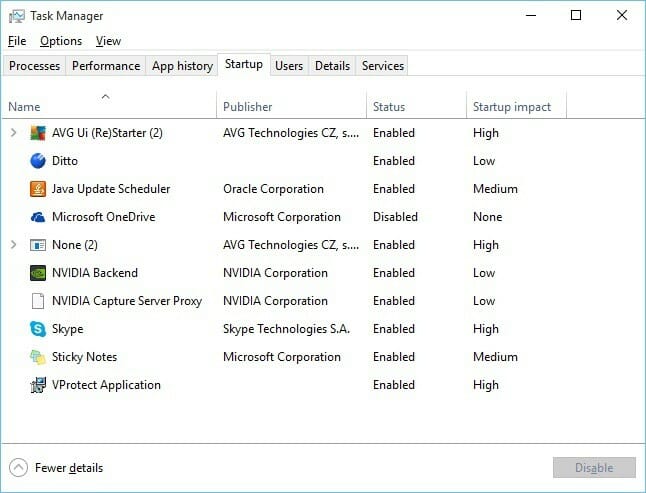
- On some PCs, you may be directed to the startup section of the Task Manager.
- Click the link.
- It will open this Task Manager window.
- You will still see all the programs set to run automatically, on startup.
- Again browse the list to pick those whose publisher is marked as unknown.
- Disable all those.
You will be able to permanently delete them using the regedit solution we will discuss later.
Most malicious malware strains are so hard to detect, and such a pain to remove because they attach themselves to your PC’s startup folder.
As soon as you start your machine, these apps are up and running. This SmartService trojan horse behaves in the same way.
You thus must make sure to scan the Startup folder and remove all suspicious-looking programs from there. This is an important step, as even the really good antiviruses may still get blocked.
5. Delete all malicious IP addresses
- Press both the Windows and R keys simultaneously to open the Run dialog box. Once it pops up, paste the command thread below and click OK.
%WinDir%System32DriversEtc
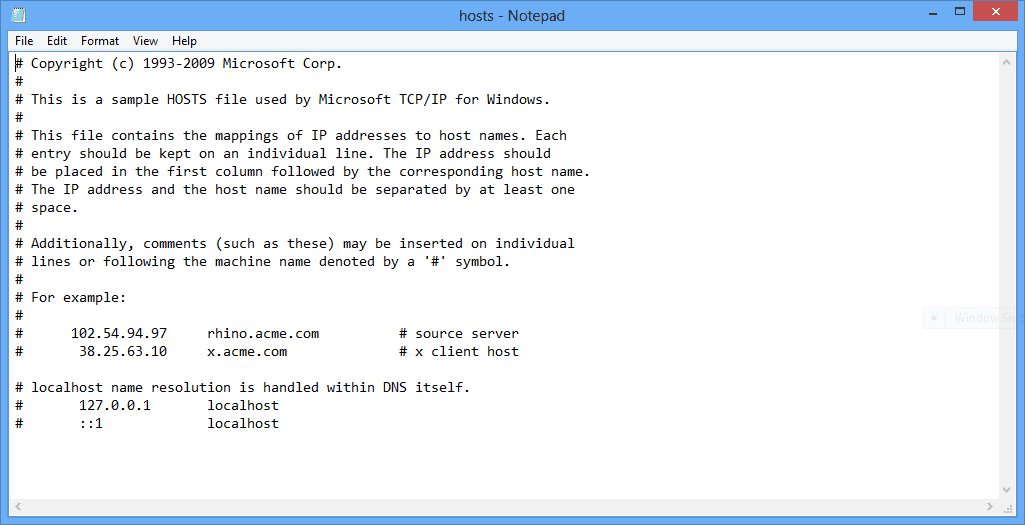
- Open the Hosts file in the Notepad.
- You should get this:
The two IP addresses you see at the bottom are for the PC’s, or localhost, and should be kept there. If you have been hacked, there will be other IPs listed below those.
Normally that’s evidence that you have been hacked. Those IPs should be removed. It is also advisable to seek the help of a cybersecurity professional at this stage. You are still not done.
Sometimes, the malware is deployed to carve a gateway for a hack or ransomware attack. Both are scary. And that’s why you should address The requested resource is in use immediately.
6. Remove malicious Windows Registry entries
- Press the Windows and R keys together and type regedit into the search box that opens.
- This will bring up the Registry Editor.
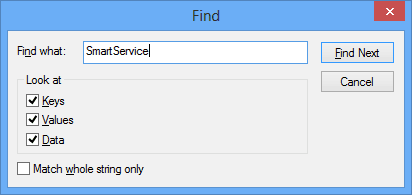
- The quickest way to find the malware once in the registry is to use the Ctrl+F keys shortcut. It will bring up this popup:
- Remember, to use this shortcut, you need to know the name of the trojan you are dealing with. In this case, start with SmartService.
- But it may be better to have a list of trojans that behave in the same way and search for all of them.
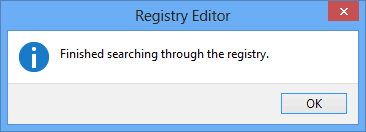
- If the Find prompt does locate the trojan, you want to delete and remove it from there. Repeat the process until the search prompt brings up this popup:
Again, be careful when making changes to the Registry. Deleting the wrong Registry files can lead to serious PC malfunction.
Now, in cases of serious malware infections like this trojan horse, there is usually some malicious changes and entries made to the Windows Registry. Your PC won’t be clean until you remove these.
But sometimes you don’t know what the trojan‘s name is. You will thus need to manually search for all suspicious-looking programs in all folders with Run in their title.
These are programs that run automatically, from the moment you start your PC. There is likely to be malicious entries in those folders.
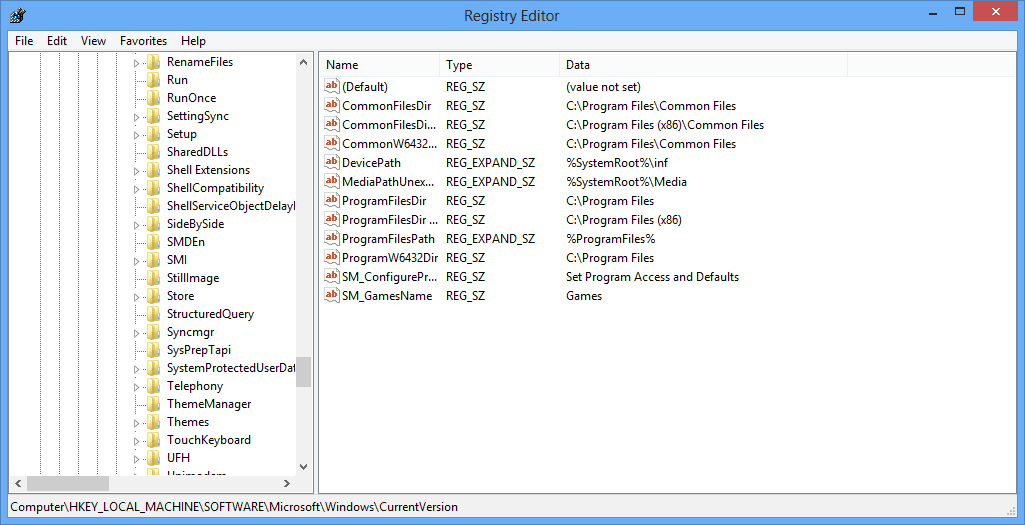
You will have to navigate to the CurrentVersion folder to find these auto-run programs. Use this sequence to get there:
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion
Once you are in the CurrentVersion folder, look for all folders with Run in the title. It can be Run, RunOnce, or others. Click once on each to reveal all the programs in the folders:
Scan the listed files and look for suspicious names, which you feel could be malware. If you are unsure about any, look them up before deleting them.
7. Prevent malware infection
Trojans like this SmartService, that leads to the error message The requested resource is in use are difficult to detect, and a pain to remove.
By disabling antiviruses, they make your task more difficult. Because of this, it would seem best to be vigilant about the way you use your PC.
You will want to desist from connecting external devices to your PC without first making sure they are clean.
This includes portable USB drives and external hard drives. There are many USB flash drive antivirus solutions that you can use. Also, avoid torrents and other freeware sites with questionable security.
Be careful when installing the software you downloaded from the Internet. Many people unknowingly grant malware programs permission to install in this way.
We hope that these solutions will help you to get rid of the error code error 0x800700aa: The requested resource is in use.
Feel free to tell us if our article helped you, and if you have any other suggestions for us, in the comment section bellow.