Laptop Encryption Software: Best Picks for 2025
11 min. read
Updated on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team. Read more
Key notes
- Protecting the data on your laptop is important, especially since it can be easier to steal than a desktop.
- That is why we created this list of file encryption software that you can get.
- Do you like reading about Data encryption? If so, you'll also like our Encryption page.
- For more product lists picked by our experts, check out our dedicated Software page.

One of the most vital areas for modern businesses is cybersecurity. Without the right protection and in place, organizations or businesses face the risk of hackers entering illegally into their systems and collecting valuable business data which may likely result into much damage in the future.
A very crucial area of cyber security is encryption. Encryption tools usually encode data, unlocking it with a certain key, making it difficult for third-parties to gain access.
Full disk encryption software guards the contents of computers by requiring a multi-factor authentication or password before the system can boot.
To make use of this software in a business context, you will require a solution which can manage devices that are encrypted, and offer key recovery and other enterprise-friendly features.
With this encryption software, you can protect data such as customer transactions and passwords, email addresses and other important information. Many organizations are also making use of encryption software’s to ensure the privacy of internal online conversations and emails.
What are the best encryption software for laptops?
WinZip (recommended)

Starting off as a mere archiving tool, WinZip has evolved way past that point, incorporating a wide variety of features and tools that make it a must-have for any PC owner, and not just an optional utility.
For example, besides the archiving tools, it is also an excellent encryption and locking tool. More so, it allows better sharing of data between PCs via networks, clouds like Dropbox, Google Drive, OneDrive, and social platforms.
The software boasts an incredibly simplistic UI, and once installed it integrates with your PC’s context menu, allowing you to archive, encrypt, and more just by right-clicking a file.
Here are some of the perks of using WinZip:
- Banking-level encryption
- Enhanced archiving capabilities
- Improved data sharing between PCs on the same network
- Integrated cloud support that works with Dropbox, Google Drive, OneDrive, and more.
- Can be tested for free without limitations for a limited time
”WinZip”
”EncryptFolder Lock
Aside from protecting assets on company computers, it is also very important to add protection to any device that stores vital data. For instance, smartphones of employees need to be protected because they store vital company data such as emails and other company documents.
Folder Lock is good for adding encryption to mobile devices.
Features/Pros:
- The app can protect photos, videos, personal files, contacts, notes, wallet cards, and audio recordings stored in your handset.
- It has some hidden security features.
- Aside from encrypting devices, you can also enable a decoy password, log unauthorized login attempts, hacker deterrents, back up all your passwords and get notifications whenever there is a potential brute-force attack.
- The app is free to download.
Cons:
- A different subscription is required for a secure backup.

Folder Lock
Password-protect all of your laptop's files and folders and keep them away from prying eyes fast and efficiently.NordLocker

Besides the versatility in terms of what it can support, it is also extremely versatile in terms of the encryption it uses to keep all of the above safe, featuring Argon2, AES256, ECC (with XChaCha20, EdDSA, and Poly1305), and other creations of modern cryptography to guarantee ultimate security of your files.
Pros:
- Comes with a 5 GB free trial
- Advanced encryption methods
- Supports a wide variety of files for protection
- Easy-to-use
- Includes cloud data syncing for protection of your online files as well
- Allows safe data transfers
- Long-term plans are extremely affordable
Cons:
- Somewhat limited platform support
Symantec Endpoint Encryption
From a single console, Symantec Endpoint Encryption software can be managed centrally providing full disk encryption for Windows OS devices.
Features/Pros:
- The console can also be used to manage its own endpoint encryption and also systems encrypted with Microsoft BitLocker and Opal-compliant self-encrypting drives.
- The solution offers employees that forget their passwords a choice of self-recovery and help-desk support.
- For ease of use, authentication can be integrated with Microsoft’s Active Directory. The full disk encryption solution also offers automated policy controls and compliance-based reporting. It can be integrated with Symantec Data Loss Prevention for additional security and consistency.
Cons:
- Management requires a better console.
- Lots of new releases.
- Interface is a bit difficult to understand.
- Symantec processes are slow.
- Symantec encryption is a bit expensive.
Supported client operating systems:
- Microsoft Windows 7, 8, 8.1, and 10
Sophos SafeGuard Encryption
Sophos SafeGuard Encryption is a powerful encryption software for laptops.
Features/Pros:
- Without an end user involvement, Sophos SafeGuard Encryption can be deployed onto endpoints and with the Intel’s AES-NI instruction set, encryption can be accelerated.
- The management for all enterprise devices is provided by a single console, including the encryption of hard disks with Microsoft’s BitLocker, Apple’s FileVault 2 and Opal self-encrypting drives.
- This consists of encryption status, auditing and editing to ensure compliance with internal and external regulations.
- The authentication system of the software supports cryptographic and biometric token, and multiple users can share encrypted computers without sharing passwords.
- If a user forgets a password, it can be recovered quickly using a challenge/response system accessed over the phone or via a web portal.
Cons:
- New users find it difficult to use.
Supported client operating systems:
- Windows XP SP3 Professional
- Windows Vista SP2 Business, Enterprise, Ultimate Edition
- Windows 7 SP1 Home Premium, Enterprise, Professional, Ultimate Edition
- Windows 8, 8.1 Pro, Enterprise Edition
- Windows 10 Pro, Enterprise Edition
Dell Data Protection Encryption Enterprise Edition

Features:
- The Enterprise Edition Server regulates the Dell solution for big deployments or the Virtual Edition Server for simpler deployments.
- Existing authentication processes including Windows password, fingerprint, RSA and smartcard are used for its integration.
- A centralized console enables encryption management which consists of encryption based on end user groups and profiles, and also the provision for the management of Microsoft BitLocker encryption software and self-encrypting drives (SEDs).
- It comes with pre-set policy templates to address compliance regulations such as Sarbanes Oxley, PCI DSS, EU Data Protection Directive 95/46/EC and HIPAA.
- Supported Windows OS includes Windows XP, 7, 8, and 10.
Check Point Full Disk Encryption Software Blade
The software offers centrally managed full disk encryption software for endpoints as a security “blade,” which is a part of its entire security suite.
Features:
- Users can only access encrypted laptop or other endpoint after authentication.
- Multi-factor authentication options consist of dynamic tokens and certificate-based smartcards.
- The full disk encryption solution supports multiple pre-boot authentication languages for global deployments.
- Check Point’s Endpoint Policy Management Software Blade manages the Full Disk Encryption Software Blade enabling central policy enforcement, administration and logging from a particular console.
- Centralized management provides control of security policies and offers various deployment options.
- One-Time Login remote help options and Remote Password Change are available for users who may have lost access tokens or forgotten their passwords.
- Web-based remote help options are available.
Cons:
- It has too much overhead and configuration.
- Supports only Windows XP, 7 and 8
Microsoft’s BitLocker full disk encryption
This is the native encryption system that comes with the Enterprise, Ultimate and Pro versions of Microsoft’s Windows Vista.
It can be used for either personal use or business purposes. Microsoft BitLocker Administration and Monitoring provides the enterprise deployment centralized management.
Third-party full disk encryption systems such as Sophos SafeGuard Enterprise and Symantec Endpoint Encryption manage the Bitlocker encryption software.
Features/Pros:
- Microsoft BitLocker Administration and Monitoring (MBAM) enable security officers to quickly determine the individual computers compliance state and also allow administrators to convert the process of encrypting volumes on client computers.
- The BitLocker encryption policy options are enforced by MBAM. The compliance of client computers with those reports and policies on the encryption status of individuals’ computers and enterprise are also monitored by MBAM.
- The recovery of encrypted devices by end-users independently is enabled by MBAM through the use of the self-service portal or a help desk.
Cons:
- Difficulty in accessing encrypted drives from non MS Operating System including Windows XP.
- If a user loses the recovery key, he or she also loses data.
- For encryption, a special TPM chip is required; however, it is available on branded Desktops or notes such as Lenovo, HP and Dell.
- When a computer is functioning normally, data from local attacks or network might not be protected.
- During Encryption or Decryption, the performance of a slight Disk may degrade.
SecureDoc Enterprise Server (SES)
SecureDoc Enterprise Server (SES) keeps all security-related management under a centralized enterprise server.
Features:
- This consists of policies, password rules, key management, recovery and the management of encryption.
- Encrypted systems can also be managed by administrators from a web console.
- Supported encryption ranges from SecureDoc’s full disk encryption for laptop to native OS encryption for Windows (BitLocker) to managing hardware-based encryption with SEDs.
- It provides pre-boot authentication using readers, smartcards, tokens or LDAP/Active Directory integration.
Cons:
- It boots slowly.
- Password should never be forgotten.
Supported client operating systems:
- Windows XP
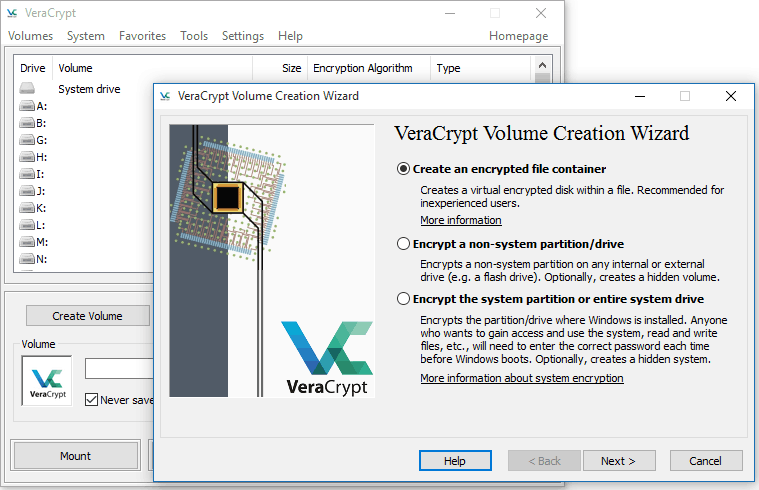
VeraCrypt
VeraCrypt is one of the most famous security tools, offering you enterprise-grade encryption for vital data.
Features:
- It is easy to use.
- Automatically adds encrypted passwords to partitions and data. However, it requires details such as location, volume size and unique hashing algorithms.
- It is immune to brute-force attacks, which prevents hackers from decrypting your passwords and other important data.
- Support for various encryption cyphers.
Cons:
- Technical skills are required in case something goes wrong
McAfee Complete Data Protection Advanced
McAfee Complete Data Protection Advanced provides a full disk encryption solution using McAfee-implemented encryption, Apple’s FileVault native encryption systems or through Microsoft’s BitLocker with pre-boot two factor authentication.
Features/Pros:
- It makes use of the instruction set of Intel’s AES-NI for faster encryption operations.
- McAfee’s ePolicy Orchestrator (ePO) management suite and other products of McAfee endpoint manage encryption.
- ePO regulates policy and patch management, recover lost passwords and demonstrate regulatory compliance.
- It synchronizes security policies with Novell NDS, Microsoft Active Directory, PKI, and other systems.
Cons:
- It is not compatible with some operating systems.
- It lacks backup protection.
- The documentations are not too good and need improvement.
- It does not offer any options to view how employees transfer, make use, or access information that are sensitive through a common schedule.
Supported client operating systems:
- Microsoft Windows 7, 8 and 10 (32/64-bit versions)
- Microsoft Vista (32/64-bit versions)
- Microsoft Windows XP (32-bit version only)
- Microsoft Windows Server 2008
⇒ Download McAfee Complete Data Protection Advanced
AxCrypt
The software is specifically designed for individuals and small groups within businesses.
Features/Pros:
- This software offers strong security, with files encrypted by either 128-bit or 256-bit AES, which can block any intruders.
- It has cloud storage capabilities. It offers automatic protection to files saved on services such as Dropbox and Google Drive.
- It is fully multilingual, and works with languages such as French, Dutch, German, Korean, Italian, Spanish, Russian, Swedish, and Portuguese.
- It has passport management.
- Your encrypted files can be accessed through a smartphone app.
- The Premium package is $27 per year.
- It has a free version with fewer options.
Cons:
- The open candy system is used by the install program for bundled third party software.
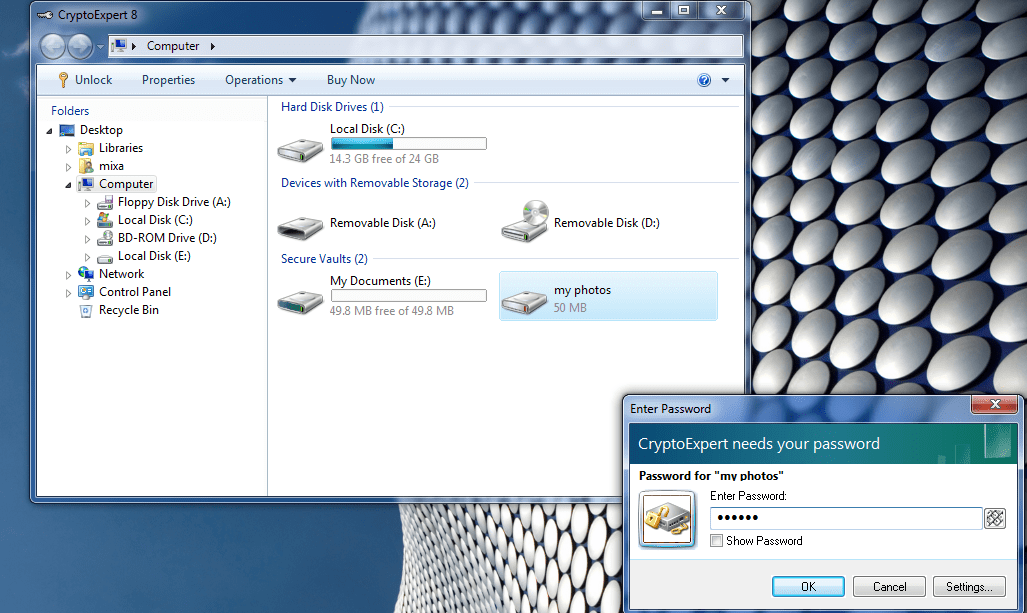
CryptoExpert
CryptoExpert provides secure data vaults for all your data to protect it from potential breaches.
Features/Pros:
- It provides a better encryption than most of the software’s listed in this article.
- Backup support for files such as certificates, Excel and PowerPoint, Word, multimedia files and email databases.
- It can protect vaults of unlimited size.
- It uses Cast, Blowfish, 3DES and AES-256 encryption algorithms.
Cons:
- It lacks secure deletion.
- Testing displays odd error messages during testing.
Supported client operating systems:
- 32-bit and 64-bit versions of Windows 7, 8, and 10.
This concludes our list of the best laptop encryption tools that you can get for your laptop.
Do you know of any other entries that deserve a spot on our list? If so, let us know by leaving us your feedback in the comments section below.
[wl_navigator]










User forum
0 messages