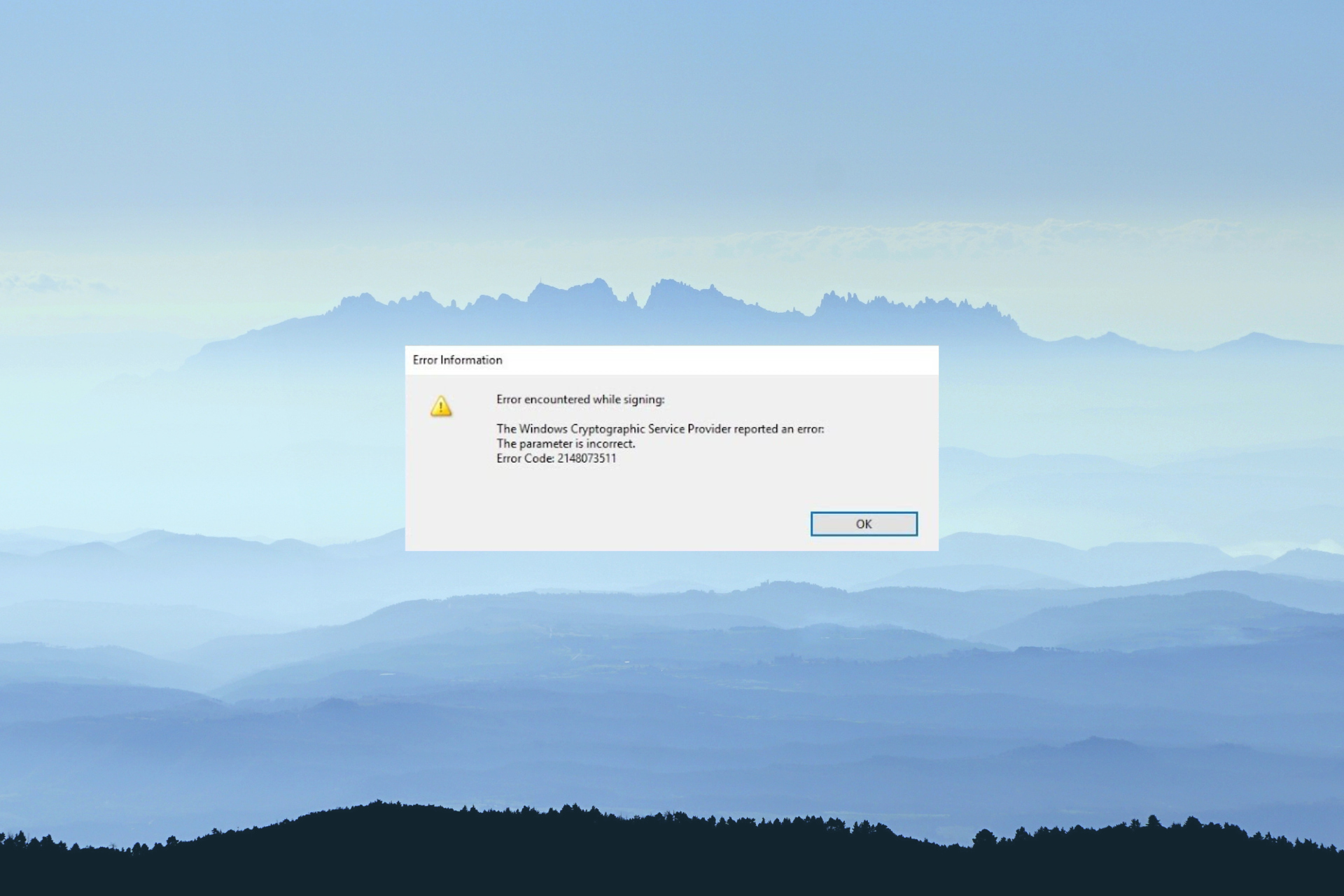
The Windows Cryptographic Service Provider Reported An Error
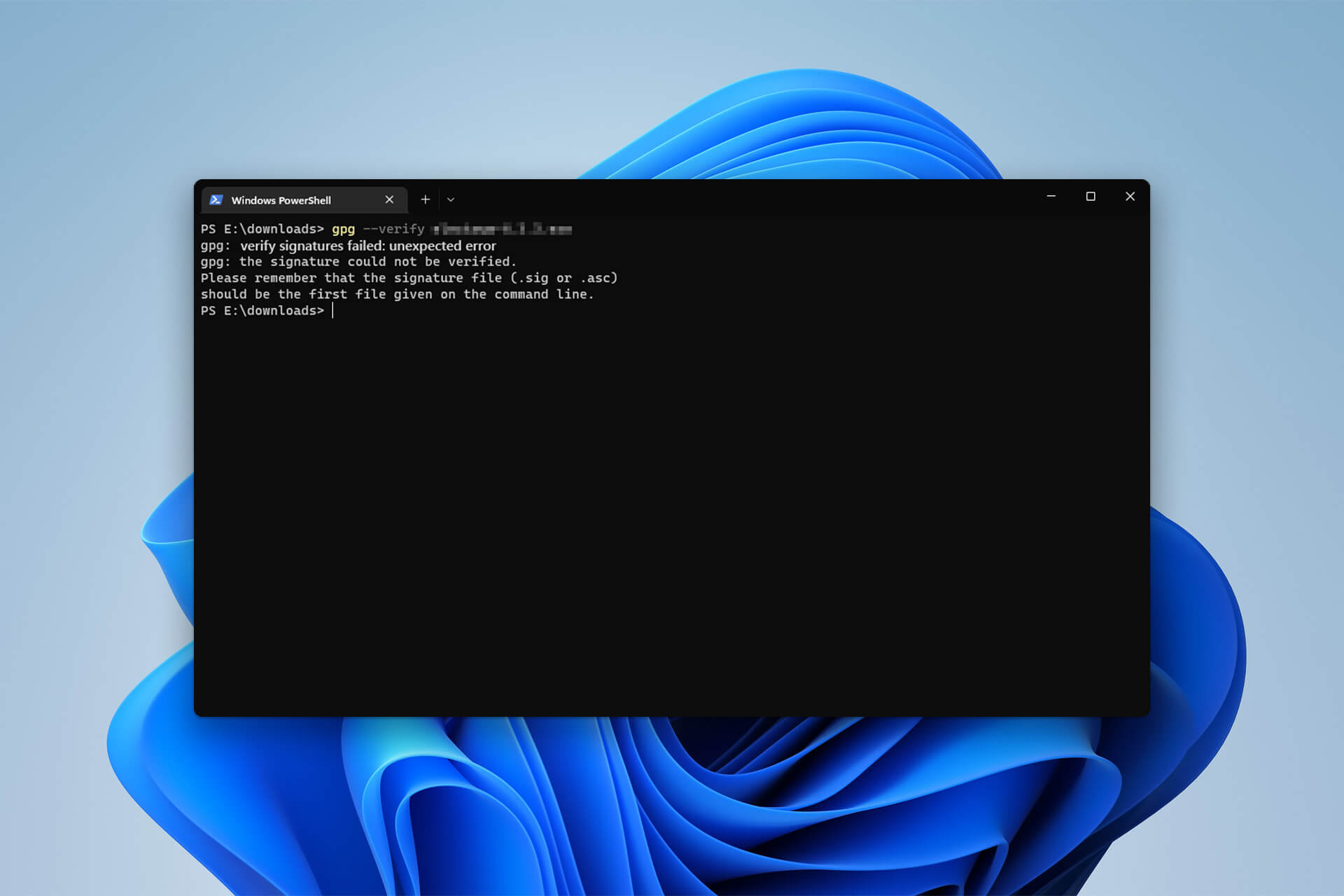
GPG Verify Signatures Failed Unexpected Error: 3 Easy Fixes

Twitter source code reveals end-to-end encryption feature
6 Most Secure Video Conferencing Software [2024 List]
Simple Fix: VPN Error 789 L2TP Connection Attempt Failed
Browser Not Supporting Password Encryption: 5 Ways to Fix It
6 Best Email Encryption Software Ranked by Features

10+ best USB drive encryption software for Windows 10/11
TPM 1.2 vs 2.0: Differences & How to Upgrade

What to Do if BitLocker Fails to Encrypt the Drive

Keystroke Encryption Software: 5 Best to Use in 2024

VyprVPN vs NordVPN, ExpressVPN, PIA, PureVPN

Are there any advantages of a VPN without encryption?

8 best encryption software tools for using free Wi-Fi