HTTP Security Header Not Detected? Here are 4 Great Fixes
5 min. read
Updated on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team. Read more
Key notes
- HTTP security header not detected error can make your server vulnerable, therefore it's important to fix it.
- Missing Strict Transport Security header means that the application fails to prevent users from connecting to it over unencrypted connections.
- Fixing this issue usually requires you to change your header configuration on the server.
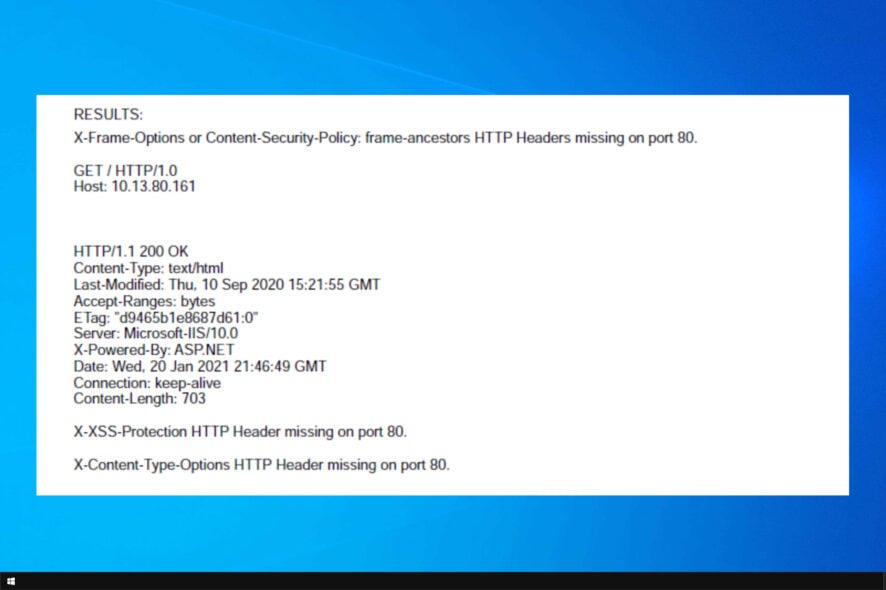
Firstly, HTTP security header not detected is an alarming issue that leaves your site vulnerable to hackers. Security headers determine whether a set of security precautions should be blocked or activated on the web browser.
Security headers direct and instruct web applications on how to handle your request and rely on responses from HTTP headers.
It depends on the responses obtained from the metadata in the HTTP request to determine if the HTTP security header is not detected.
Also, new browsers have a built-in protection system known as the XSS filter. However, it could be turned off by default, which leads to this problem.
This isn’t the only error that you can encounter, and many reported HTTP 401 unauthorized error on their PC, but that can be easily fixed.
What causes the HTTP security header not to be detected?
Cross-site scripting (XXS) occurs when malicious and dangerous code is sent by the attacker to a different end-user. Hence, if your header lacks any of these during the attack, it could cause HTTP security header not detected.
- X-frame options (Strict transport security): X-frame options help with improving the security of web applications against the threats and attacks from clickjacking. Clickjacking happens when an attacker uses different tricks to lure users into clicking on an unintended link.
- X-content type options: This reads or rather, allows the web application to sniff the MIMEtype to stop the browser from loading the styles and scripts from an incorrect MIMEtype.
- HTTP Strict Transport Security: This header deals with the browser’s built-in Cross-Site Scripting (XSS) filter, and prevents communication with illegitimate web servers. It instructs your browser direct traffic to secure and legitimate HTTPS sites.
- X-XSS-Protection HTTP: This allows you to whitelist content sources. It can prevent all the XSS attacks and reduces the damage from those that get through.
Many reported HTTP security header not detected on port 80, and we’re going to show you how to fix that issue on several different platforms.
How can I fix the HTTP security header not detected?
1. Implement X-Frame-Options in the server
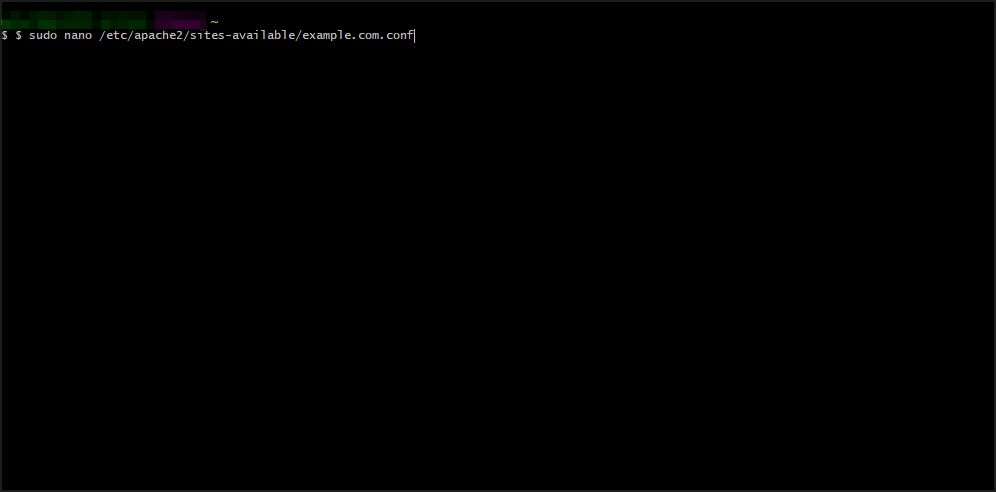
1.1 Apache
- Open your virtual host configuration file. Next, input the following:
$ sudo nano /etc/apache2/sites-available/example.com.conf - Add the following to the configuration file. Afterwards, restart the server:
Header always append X-Frame-Options DENY
1.2 Nginx
- Open your Nginx virtual host configuration file and place this in the directory:
/usr/local/nginx/conf - Add this to the configuration file:
add_header X-Frame-Options DENY
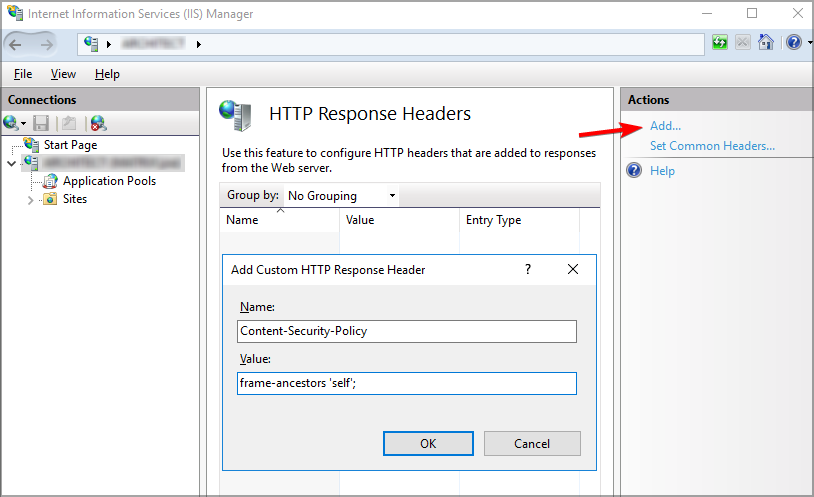
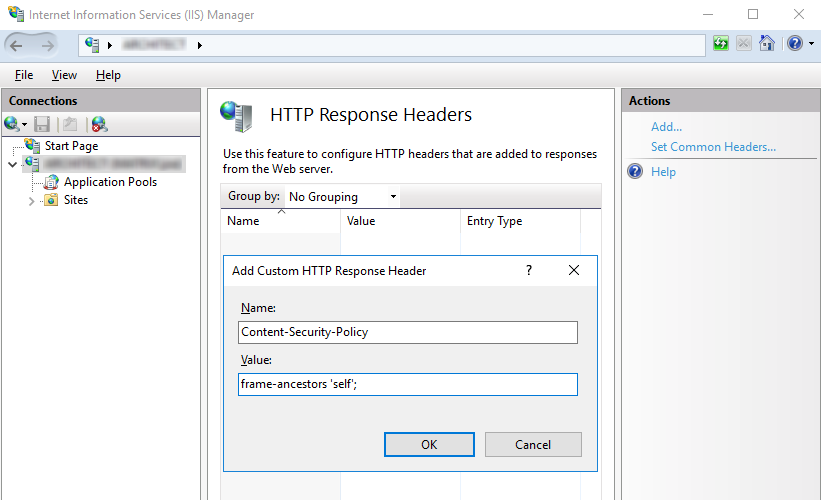
1.3 IIS
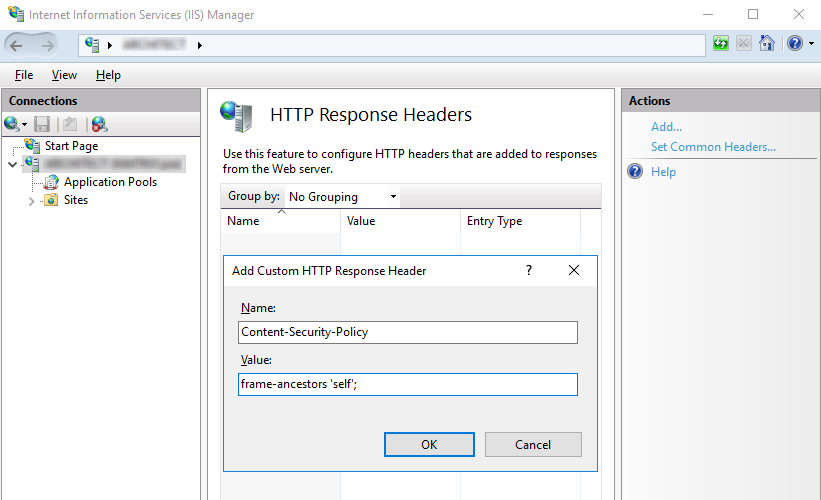
- Open IIS server host Manager.
- Go to HTTP Response Headers.
- Click Add and enter X-Frame-Options in the name entry, and DENY in the value.
- Select OK to effect change.
2. Implement X-XSS-Protection
2.1 Apache
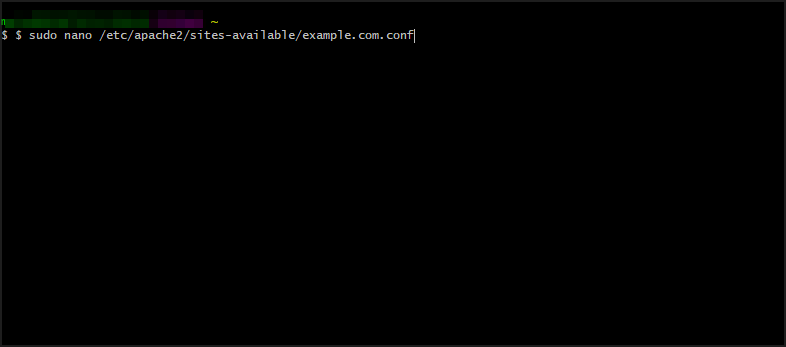
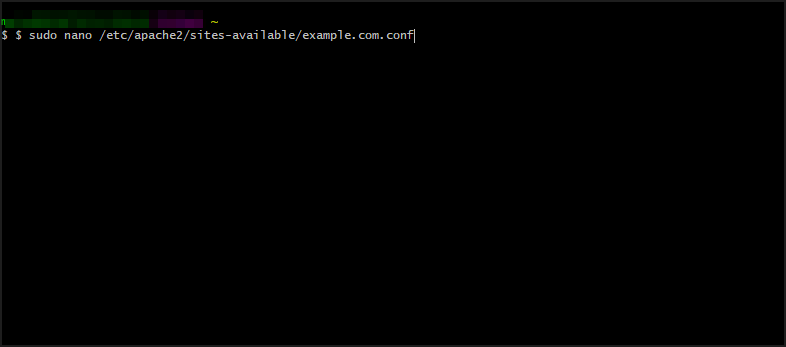
- Open virtual host configuration file and input
$ sudo nano /etc/apache2/sites-available/example.com.conf - Add this to the configuration file:
Header set X-XSS-Protection "1; mode=block
As you can see, it’s pretty simple to fix HTTP Security header not Detected vulnerability in Apache.
2.2. Nginx
- Open your Nginx virtual host configuration file and place this in the directory:
/usr/local/nginx/conf - Input the following in the conf file and restart the server:
add_header X-XSS-Protection1; mode=block
2.3 IIS
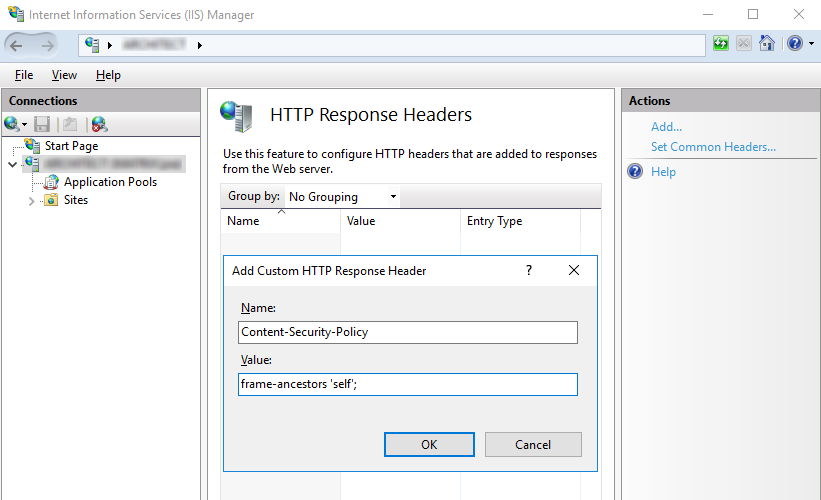
- Open IIS server host Manager.
- Go to HTTP Response Headers.
- Click Add and enter X-XSS-Protection in the name entry, and nosniff in the value.
- Select OK to effect change.
3. Implement X-Content-Type-Options
3.1 Apache
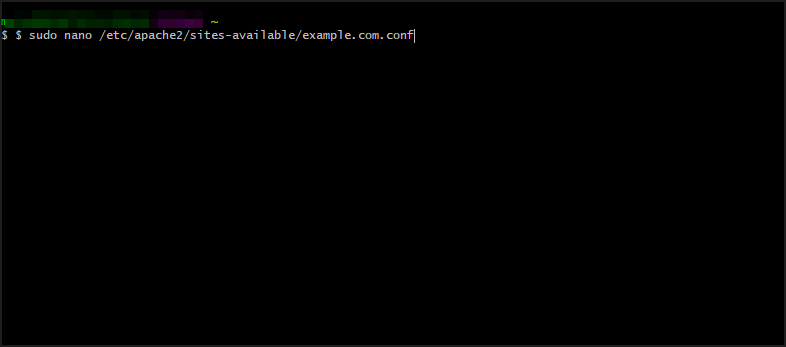
- Open your virtual host configuration file using this directory:
$ sudo nano /etc/apache2/sites-available/example.com.conf - Add the following to the configuration file, then restart the server:
Header set X-Content-Type-Options nosniff
3.2 Nginx
- Open your Nginx virtual host configuration file and place this in the directory:
/usr/local/etc/nginx - Add the following in the nginx.conf file, then restart the server:
add_header X-Content-Type-Options nosniff;
As you can see, it’s pretty simple to fix HTTP Security header not Detected vulnerability in Nginx with this method.
3.3 IIS
- Open IIS server host Manager.
- Go to HTTP Response Headers.
- Click Add and enter X-Content-Type-Options in the name entry, and nosniff in the value.
- Select OK to effect change.
4. HTTP Strict Transport Security
4.1 Apach
- Open your virtual host configuration file using this directory:
$ sudo nano /etc/apache2/sites-available/example.com.conf - Add the following to the configuration file, and restart the server:
Header set Strict-Transport-Security "max-age=31536000; includeSubDomains; preload
4.2 Nginx
- Open your Nginx virtual host configuration file and place this in the directory:
/usr/local/etc/nginx - Add the following in the nginx.conf file, and restart the server:
add_headerStrict-Transport-Security 'max-age=31536000; includeSubDomains; preload';
4.3 IIS
- Open IIS server host Manager
- Go to HTTP Response Headers.
- Click Add and enter HTTP Strict Transport Security in the name entry, and max-age=31536000; includeSubDomains; preload in the value.
- Select OK to effect change.
This is one way to fix HTTP Security header not detected vulnerability in IIS, so be sure to try it out.
HTTP strict transport security header (HSTS) is supported across all browsers. As such, the issue should be fixed after this.
These are the best solutions for the HTTP security header not detected issue. Also, it is advisable that you follow these fixes carefully to input the right information into the configuration file.
HTTP Security header not detected issue has been reported on SonicWall, Windows 2012 R2 and, Fortigate, but the solutions for these platforms are similar to the ones from this guide.
In addition, using these HTTP security headers will improve your server security and enable them on your sites.
Check out our guide to solve HTTP error 400 that users have complained about aside from security.








User forum
0 messages