Microsoft fixes 63 vulnerabilities in the February 2025 Patch Tuesday with 2 CVEs actively exploited
You should install the latest Microsoft security updates for your OS
3 min. read
Published on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team. Read more

Microsoft released the latest Patch Tuesday security updates and the list of covered vulnerabilities is much shorter than the one from January. Out of the 63 patched flaws, 4 are of critical severity, and 2 of them were actively exploited.
To avoid exposing your system, install the latest Windows security updates, including KB5051987 and KB5051989 for Windows 11 and KB5051974 for Windows 10.
The most dangerous threats involve the elevation of privileges
The most dangerous threats covered by the February Patch Tuesday update are CVE-2025-21391 and CVE-2025-21418 which are zero-day vulnerabilities.
CVE-2025-21391 involves a Windows Storage elevation of privilege vulnerability and attackers actively used it to delete targeted files on a system.
Here’s how Microsoft explains this issue in the document:
According to the CVSS metrics, successful exploitation of this vulnerability could lead to no loss of confidentiality (C:N) but have major impact on integrity (I:H) and on availability (A:H). What does that mean for this vulnerability?
This vulnerability does not allow disclosure of any confidential information, but could allow an attacker to delete data that could include data that results in the service being unavailable.
There are no details about how this vulnerability was exploited and in what circumstances.
The other zero-day threat, CVE-2025-21418, concerns the Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability. This one seems a lot more dangerous because the attackers exploiting it were able to gain system privileges in Windows.
Again, there is no detailed information about this vulnerability, but it was discovered by an anonymous entity.
Another vulnerability Microsoft patched is CVE-2025-21194 which involves a Microsoft Surface Security Feature Bypass Vulnerability. It is a hypervisor vulnerability that enables an attacker to bypass UEFI and compromise the secure kernel.
This Hypervisor vulnerability relates to Virtual Machines within a Unified Extensible Firmware Interface (UEFI) host machine. On some specific hardware it might be possible to bypass the UEFI, which could lead to the compromise of the hypervisor and the secure kernel.
However, in the description of this vulnerability, Microsoft explains that the attacker needs to first access a restricted network to successfully exploit it and run an attack.
Another critical thread that was likely to be exploited is the NTLM Hash Disclosure Spoofing Vulnerability coded as CVE-2025-21377. Here are Microsoft’s notes about this threat:
This vulnerability discloses a user’s NTLMv2 hash to the attacker who could use this to authenticate as the user.
While Microsoft has announced retirement of the Internet Explorer 11 application on certain platforms and the Microsoft Edge Legacy application is deprecated, the underlying MSHTML, EdgeHTML, and scripting platforms are still supported. The MSHTML platform is used by Internet Explorer mode in Microsoft Edge as well as other applications through WebBrowser control. The EdgeHTML platform is used by WebView and some UWP applications. The scripting platforms are used by MSHTML and EdgeHTML but can also be used by other legacy applications. Updates to address vulnerabilities in the MSHTML platform and scripting engine are included in the IE Cumulative Updates; EdgeHTML and Chakra changes are not applicable to those platforms.
To stay fully protected, we recommend that customers who install Security Only updates install the IE Cumulative updates for this vulnerability.
If you want to explore all the 63 CVE vulnerabilities patched in the February 2025 Patch Tuesday, click on the highlighted link.
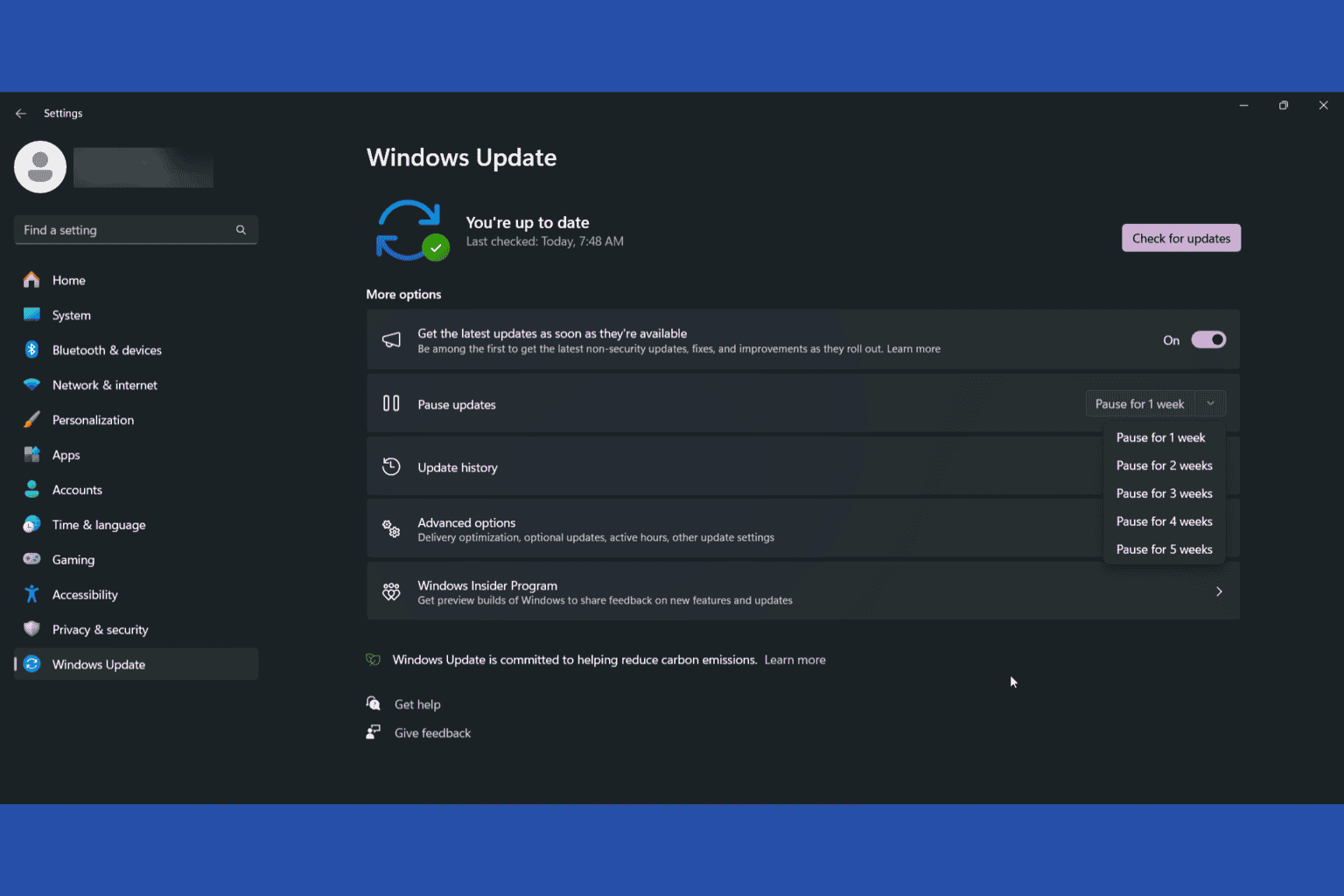
In case you haven’t done that already, install the latest Windows updates by accessing Settings > Windows Update or install them manually from the Microsoft Update Catalog.




User forum
0 messages