How to set up Multi-Factor Authentication on RDP
Configure MFA for RDP easily with specialized services
4 min. read
Updated on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team. Read more
Key notes
- To use multi-factor authentication on RDP you can always rely on third-party services.
- If you prefer Microsoft products, you can also use Azure to set up MFA.
Many are using Remote Desktop Protocol to access remote PCs, and if you want to take your security to a new level, we suggest using multi-factor authentication for RDP.
MFA is extremely useful, and if you’re using VPNs, be sure to check our guide on how to set up MFA for VPN. Setting multi-factor authentication doesn’t have to be difficult; in today’s guide, we will show you the best ways to do it.
How can I set up multi-factor authentication in RDP?
1. Use ADSelfService Plus
- Log in to the ADSelfService Plus admin portal.
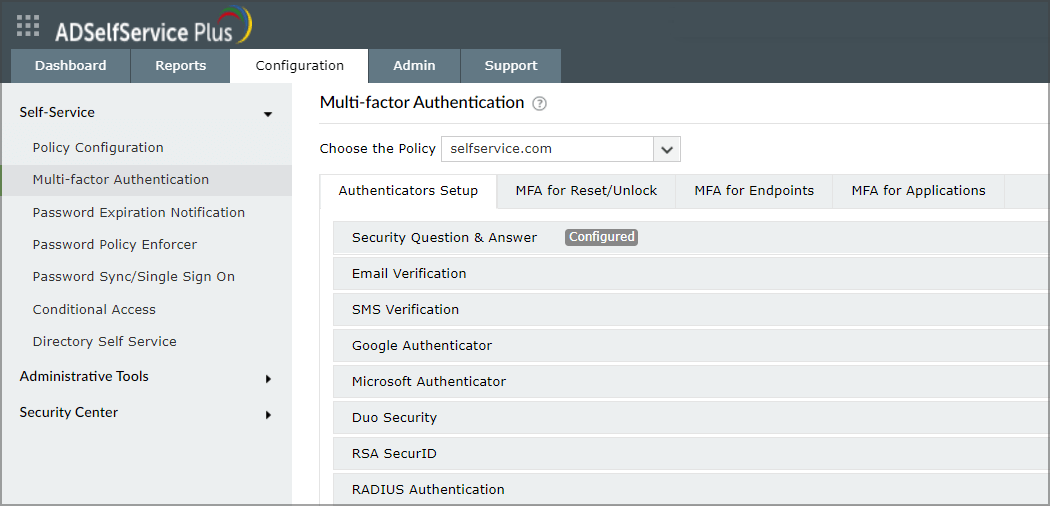
- Next, navigate to Configuration and then choose Multi-factor Authentication. Lastly, pick Authenticators Setup.
- Click on Choose the Policy and select the desired one.
- Configure the authenticators according to your organization’s needs.
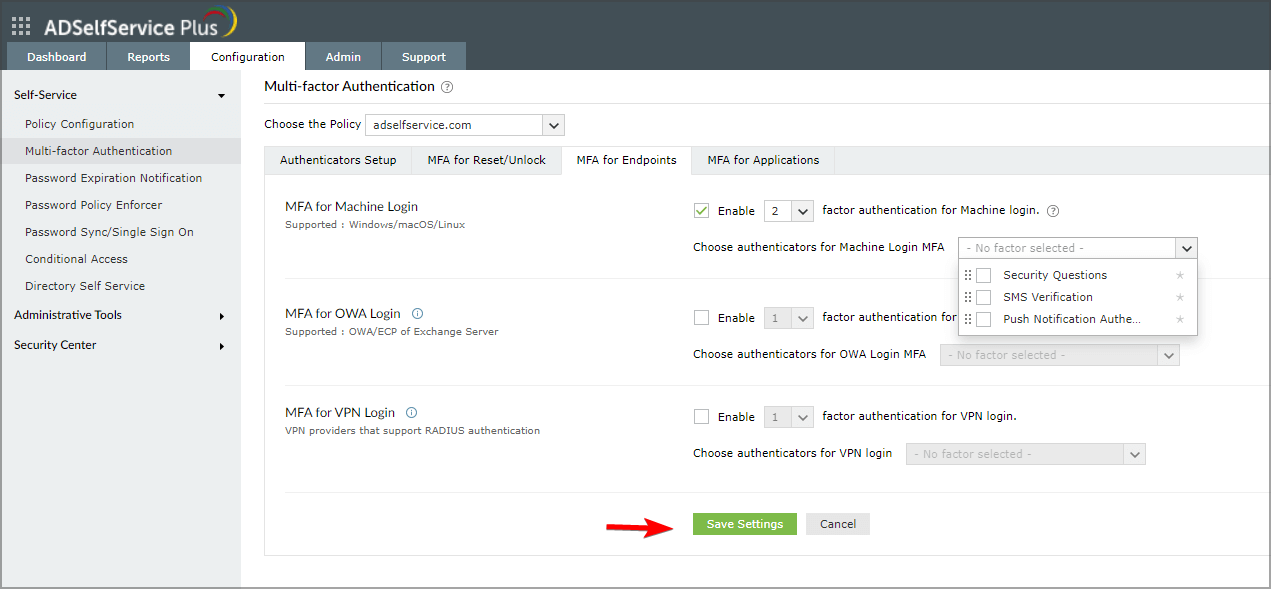
- Next, head over to Configuration. Choose Multi-factor Authentication and then select MFA for Endpoints.
- In the MFA for Machine Login section, check Enable _ factor authentication for machine login. After that, choose the authentication factors that you want to use.
- Lastly, select the desired authentication methods and click on Save Settings.
Do not hesitate to give it a try as well!

ManageEngine AdSelfService Plus
Enhance the security of your organization and secure remote sessions with AdSelfService Plus.2. Use Azure Multi-Factor Authentication
Configure the Remote Desktop Gateway
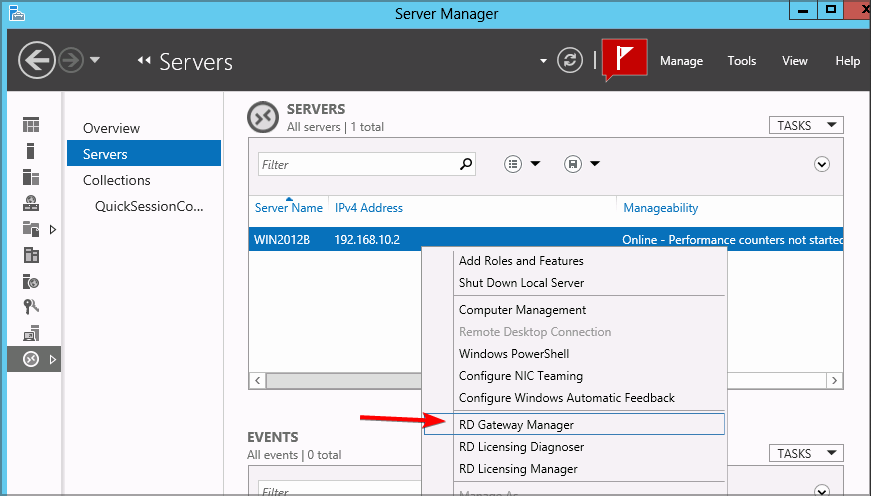
- Open RD Gateway Manager, right-click the desired server, and choose Properties.
- Head to the RD CAP Store tab and choose Central server running NPS.
- Add one or more Azure Multi-Factor Authentication Servers as RADIUS servers. You can do that by entering the server’s IP address.
- Lastly, create a shared secret for each server.
Change the timeout policy
- Open NPS and head to the RADIUS Clients and Server. Next, select Remote RADIUS Server Groups.
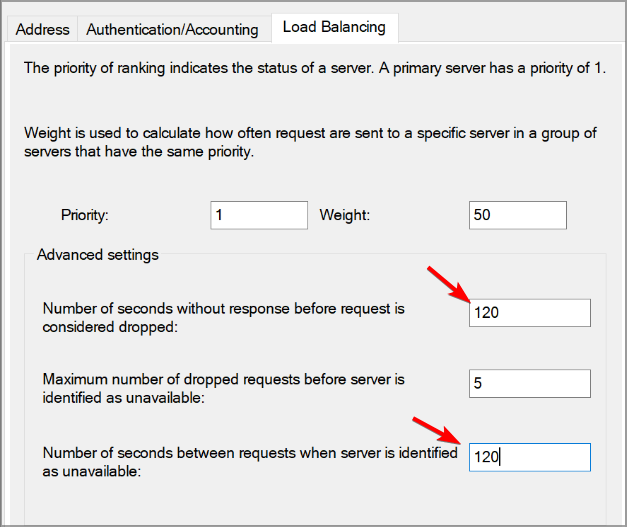
- Choose TS GATEWAY SERVER GROUP and go to the Load Balancing tab.
- Locate the following settings: Number of seconds without response before request is considered dropped and Number of seconds between requests when server is identified as unavailable. Set them to 30-60 seconds.
- Lastly, go to the Authentication/Account tab and check if RADIUS ports match the MFA Server ports.
If you want to exclude a user from MFA on Azure, this guide will come in handy.
Prepare NPS for MFA authentication
- Right-click RADIUS Clients and select New.
- Now add Azure Multi-Factor Authentication Server as RADIUS client. Choose a Friendly name and specify a shared secret.
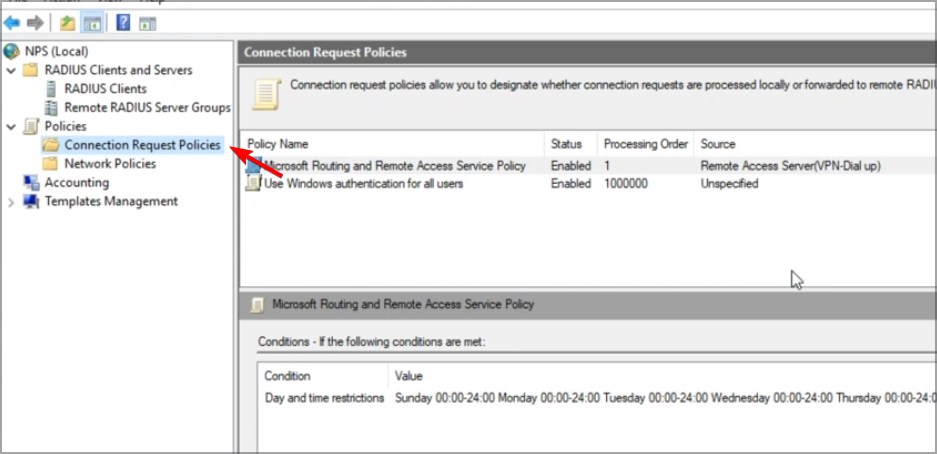
- Now head to the Policies menu and select Connection Request Policies.
- Right-click the TS GATEWAY AUTHORIZATION POLICY and choose Duplicate Policy.
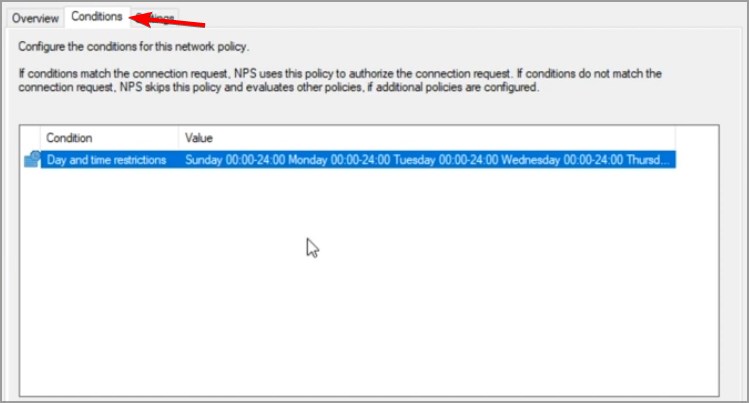
- Open the new policy and head to the Conditions tabs.
- Add a condition that matches the Client Friendly Name with the Friendly name.
- Now head to the Settings tab and choose Authentication.
- After that change the Authentication Provider to Authenticate requests on this server.
- Lastly, ensure the new policy is set above the original policy in Connection Request Policies. This will prevent loop conditions from occurring.
Configure Azure Multi-Factor Authentication
- Open Azure Multi-Factor Authentication Server and select RADIUS.
- Now check the Enable RADIUS authentication.
- Navigate to the Clients tab and make sure that ports match the ones configured in NPS. After that, click Add.
- Add the RD Gateway server IP address, application name, and a shared secret. Keep in mind that the secret needs to be the same on both Azure Multi-Factor Authentication Server and RD Gateway.
- Go to the Target tab and select the RADIUS server(s).
- Click on Add and enter the IP address, shared secret, and ports of the NPS server.
Setting up multi-factor authentication for RDP can be complicated, depending on your service.
However, some services are more straightforward to configure than others, so use the ones that match your needs. To find suitable software for these needs, we suggest using one of these multi-factor authentication software tools.
What methods do you use for MFA for RDP? Let us know in the comments section below.

User forum
0 messages