VPN
Here we discuss and cover the VPN industry entirely with news, guides, and reviews. You will find a wide range of tools to help protect your privacy and have access to the content you’re interested in without restrictions.
Browse VPN by topic: Streaming | Business | Gaming | Security | Unblocking | Traveling | How-To Guides | Best Deals
💯 Discover the best VPNs for your needs:
- Best VPNs for Windows 10
- Best VPNs for Windows 8 and 8.1
- Best VPNs for Windows 7
- Best VPNs for Windows Vista
- Best VPNs for Windows XP
- Best VPNs for iPhone
- Best VPNs for laptops
- Best VPN routers
- Fastest VPNs for streaming
- Best VPNs for Tor
- Best VPNs for cryptocurrency
- Best corporate VPNs
- Best VPNs for anti-hacker protection
- Best VPNs for LAN gaming
- Best VPNs to host game servers
- Best VPNs for VoIP
🛠️ Find out how to:
- Create a VPN connection
- Use the Windows 10 built-in VPN
- Redirect all network traffic through VPN
- Connect to VPN on laptops
- Test VPN speed and leaks
- Access blocked websites
- Set up a VPN on Xbox
- Fix common VPN errors
- Speed up your VPN connection
- Fix VPN blocked by administrator
- Circumvent geoblocking
- Turn off VPN temporarily or permanently
- Use a VPN without any encryption
- Improve your ping with a VPN
- Minimize packet loss with a VPN
- Stop ISP throttling with a VPN


Virgin Media Blocking VPN? Best 4 VPNs That Don’t Get Blocked [Free Trial]

7 Best VPNs for Binance: 2024 Tested [US & Worldwide]

7 Best VPNs for Eero Routers [How to Install & VPN Passthrough]

HideIPVPN is 70% Off With a 2-year Plan For Cyber Monday

Get 49% Off & 3 Months Free on ExpressVPN For Gaming
Get NordLayer Business VPN With 22% Discount on Annual Plan

Do Eero Routers Support OpenVPN? All You Need to Know
How to Watch Australian Survivor in Canada

VPN Not Working With Crave? Here’s How to Fix It in No Time
How To Fix VPN Blocking AirPlay [3 Working Solutions]
Fix GTA Online Not Working with VPN [5 Tested Methods]

Does a VPN Protect You from Phishing? [+ Best Practices]
Betternet VPN is Connected but not Working: 3 Ways to Fix it

Firestick not Working with VPN – Tested Fixes in 2024

Roobet Not Working With VPN? Here Are 3 Easy Ways to Fix It
Yahoo Not Working With VPN? Use These Solutions [Fix]

FXNOW Not Working With VPN? Try These 3 Tested Solutions
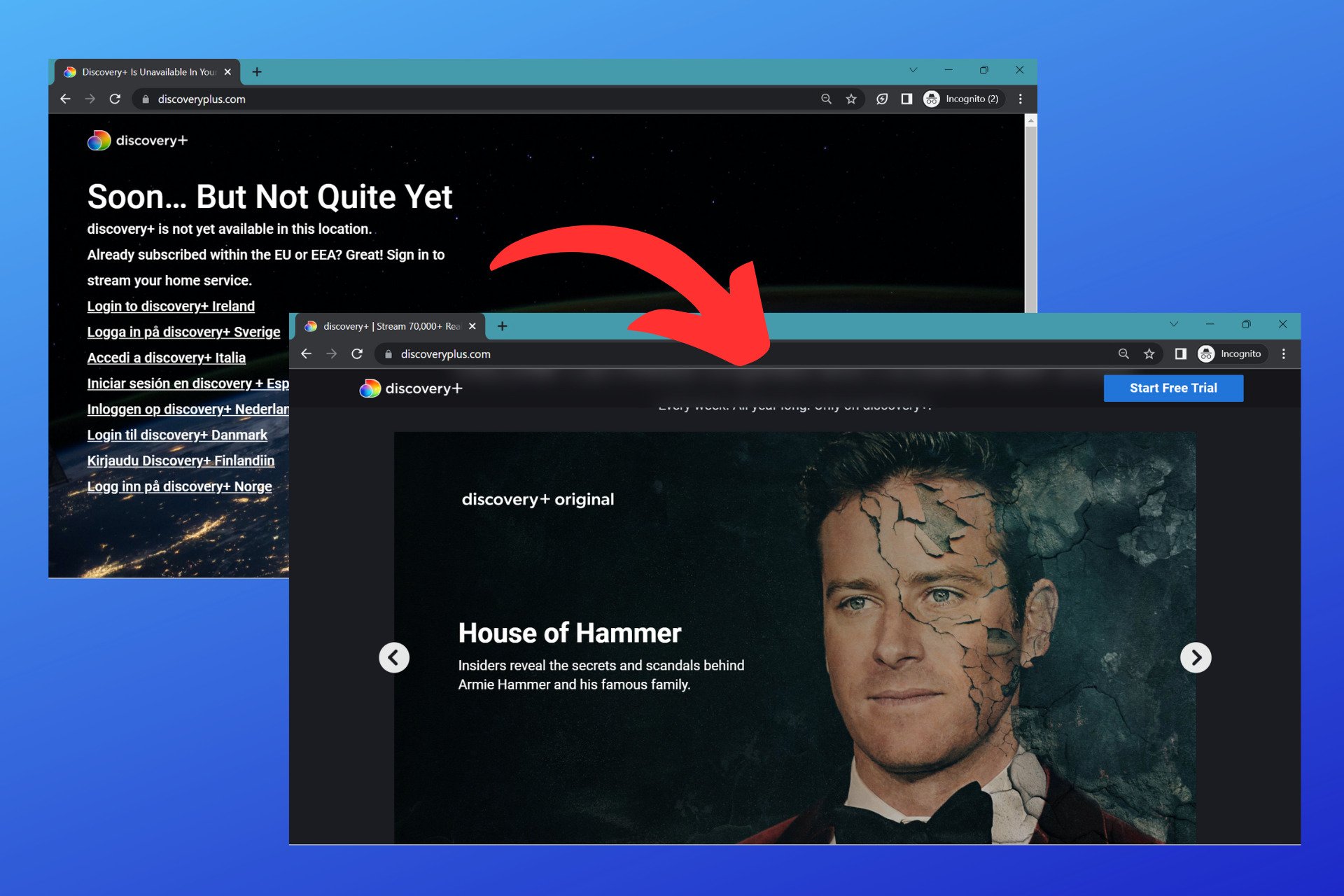
Fix Discovery Plus not Working With VPN + Best VPNs for It
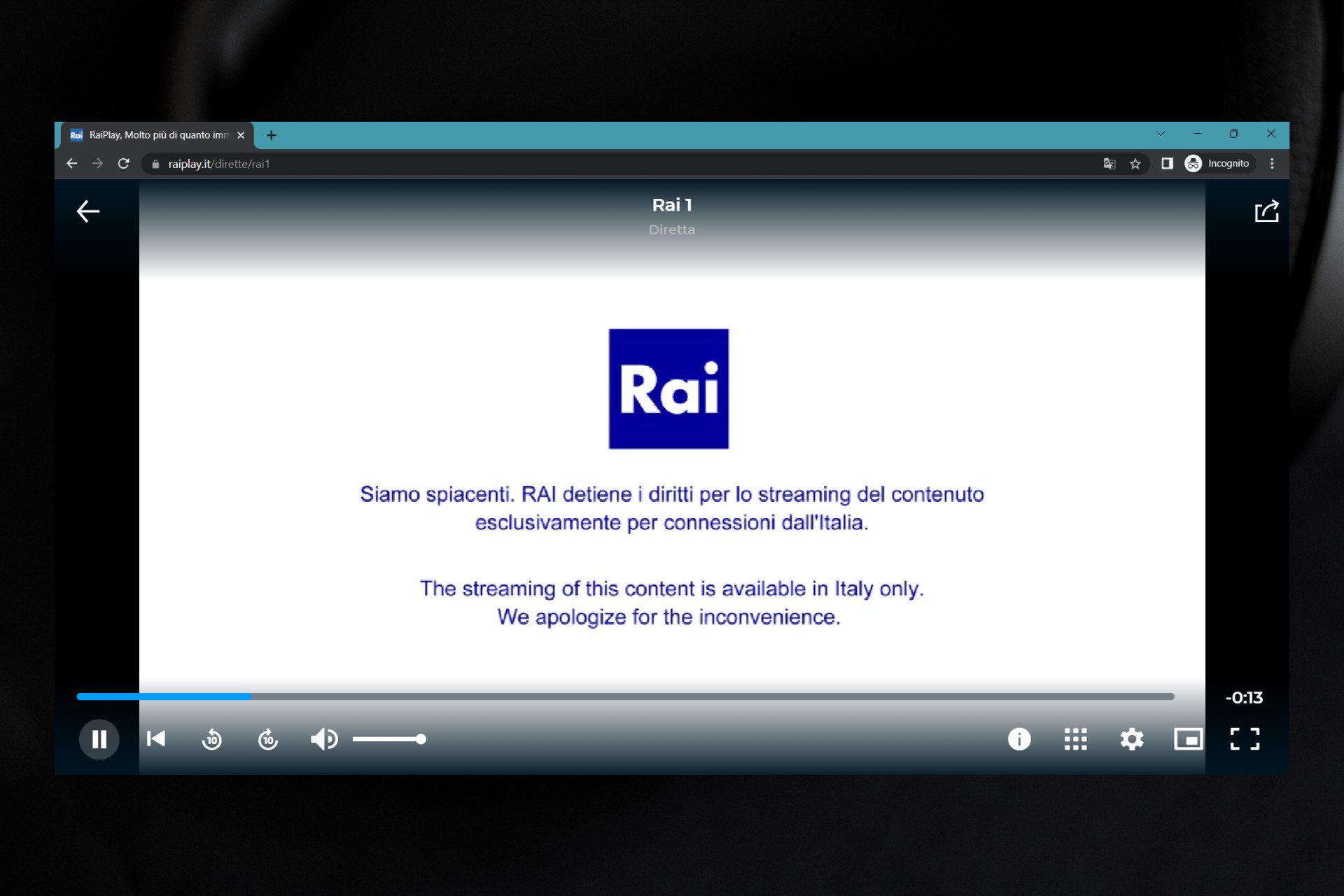
RaiPlay Not Working with VPN? Do This! [Working]

My5 Not Working With Your VPN? Here Are 3 Tested Solutions
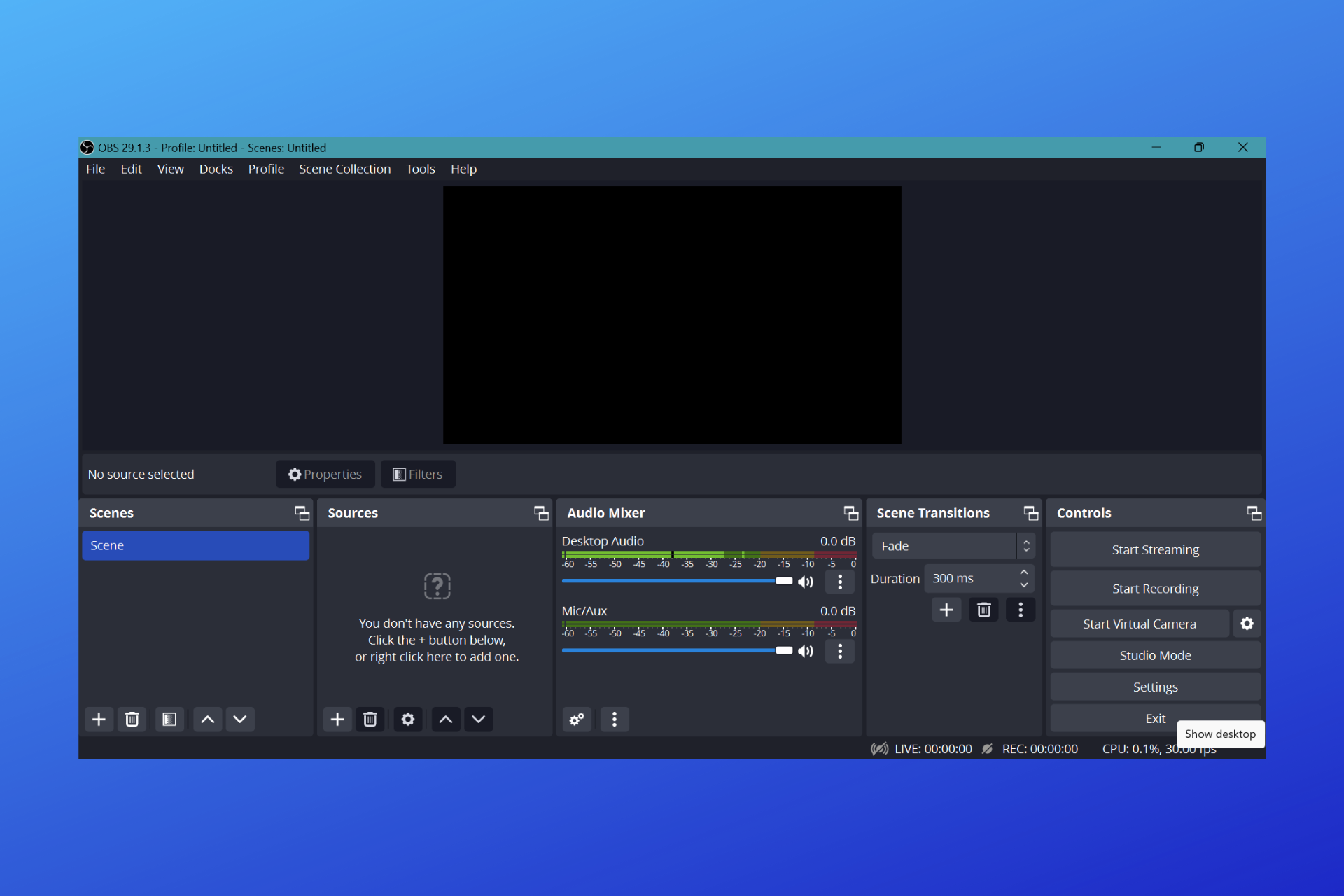
What to Do When OBS Not Working with VPN + Best VPNs for It!
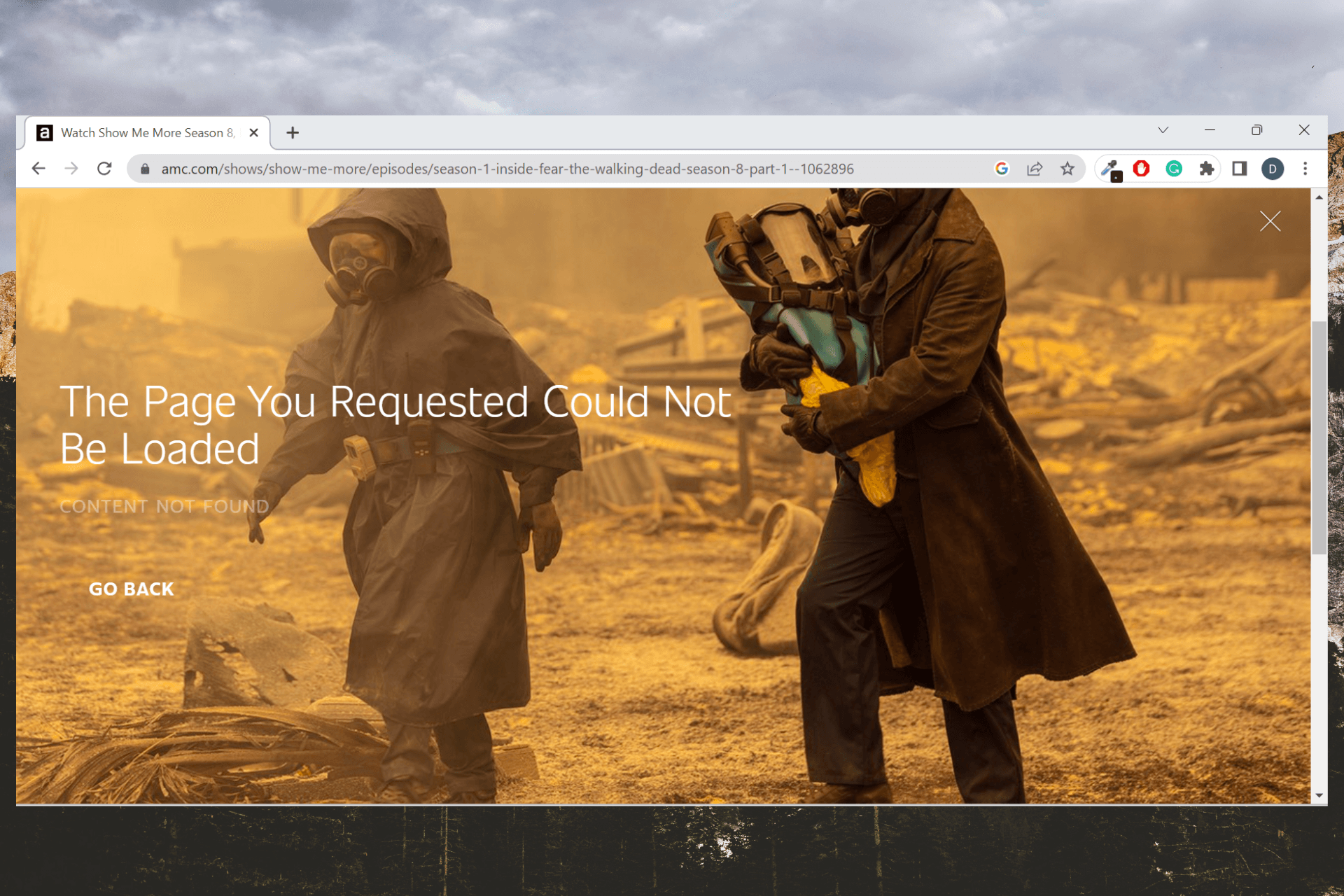
AMC Not Working with VPN? Try These 7 Fixes!

Voicemail Not Working with VPN? Do This! [Working]

Siri not Working with VPN: Here’s How to Fix it for Good!
TVNZ Not Working with VPN? Do This to Get it Fixed!
Freeview Play Not Working With VPN? Here’s The Fix!
7plus Not Working With VPN? Here’s What to Do to Fix it!
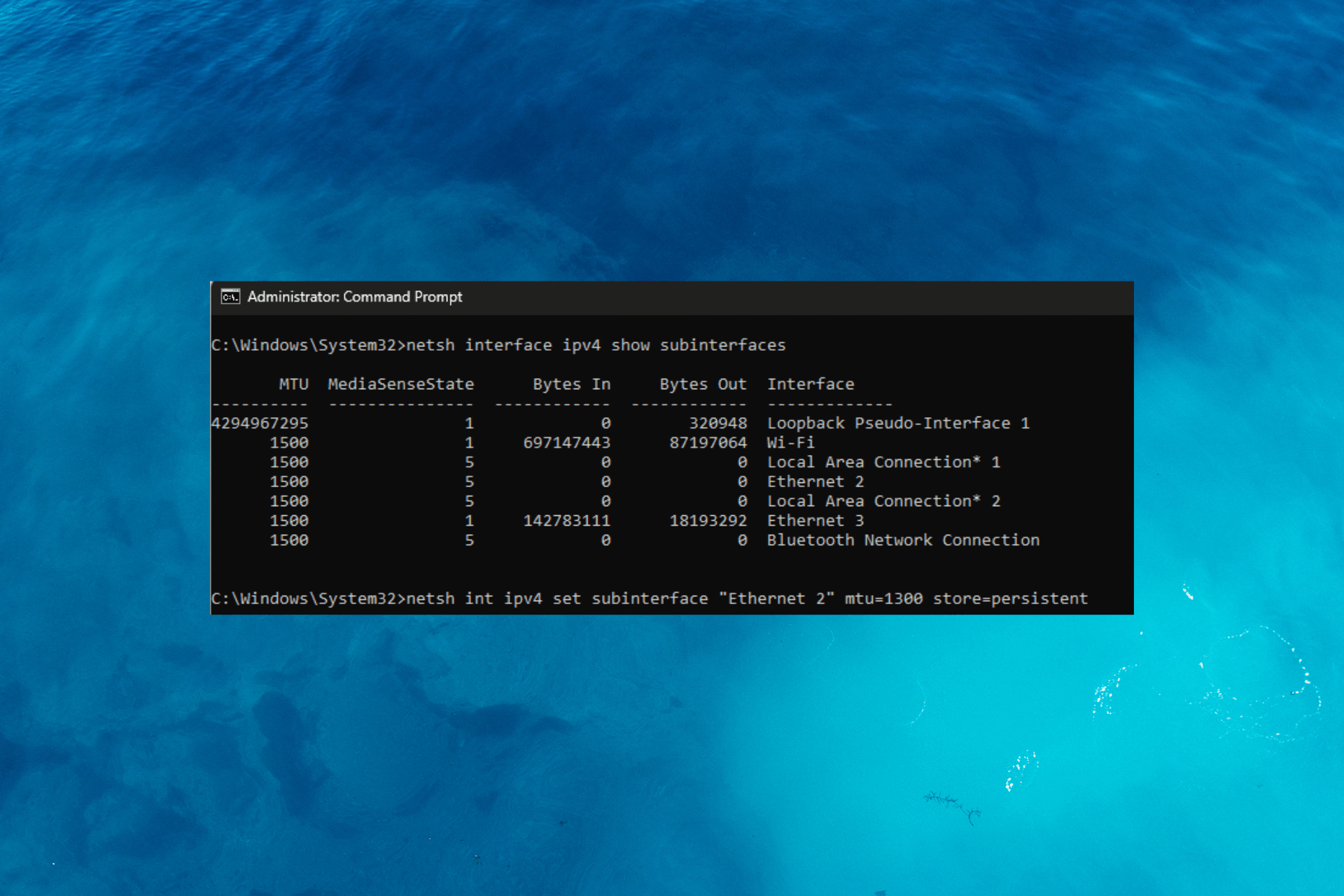
GlobalProtect isn’t Working on Hotspot? How to Fix It
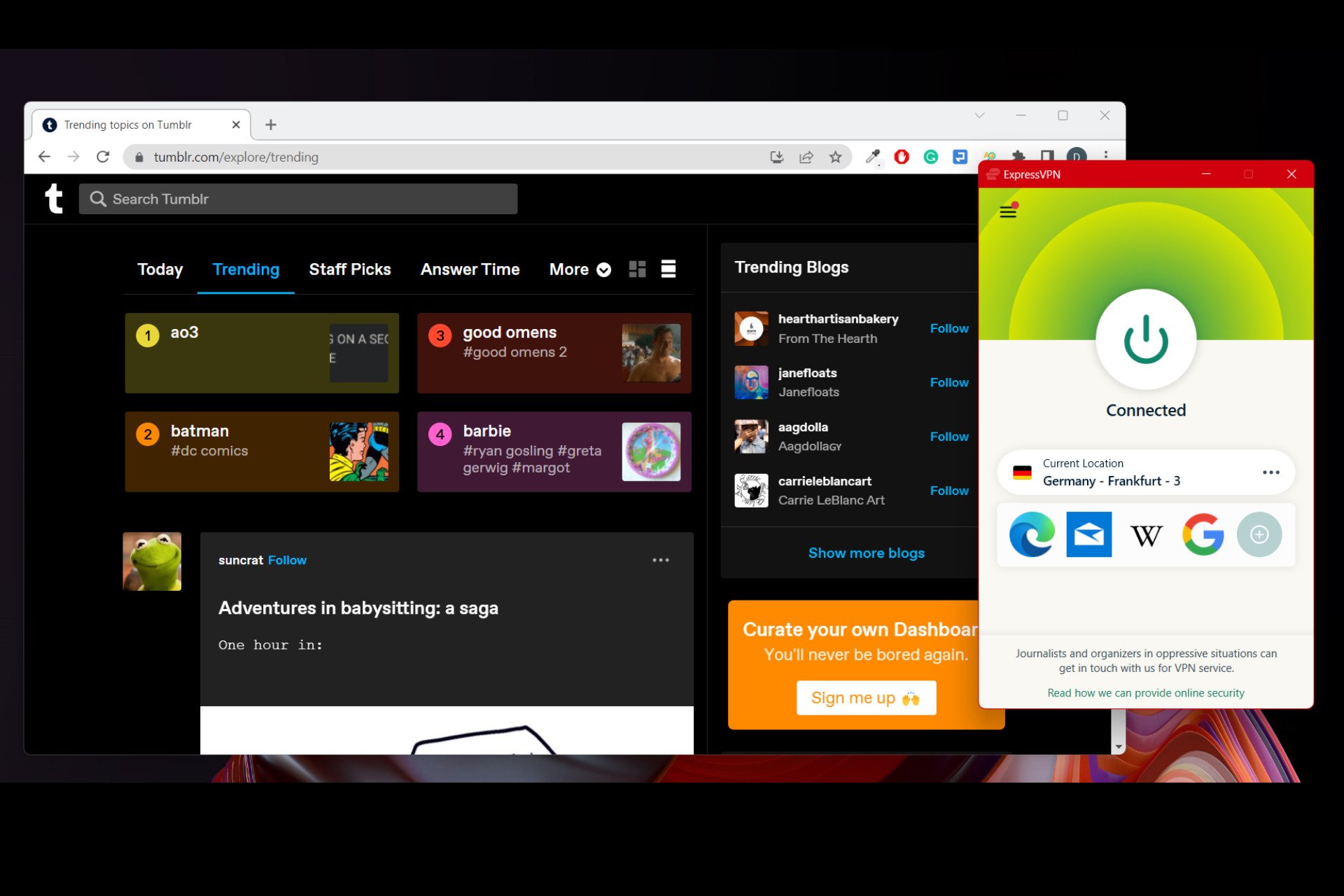
Tumblr not Working with VPN? Here’s How to Fix it!

How Does a Corporate VPN Work? [All You Need to Know]
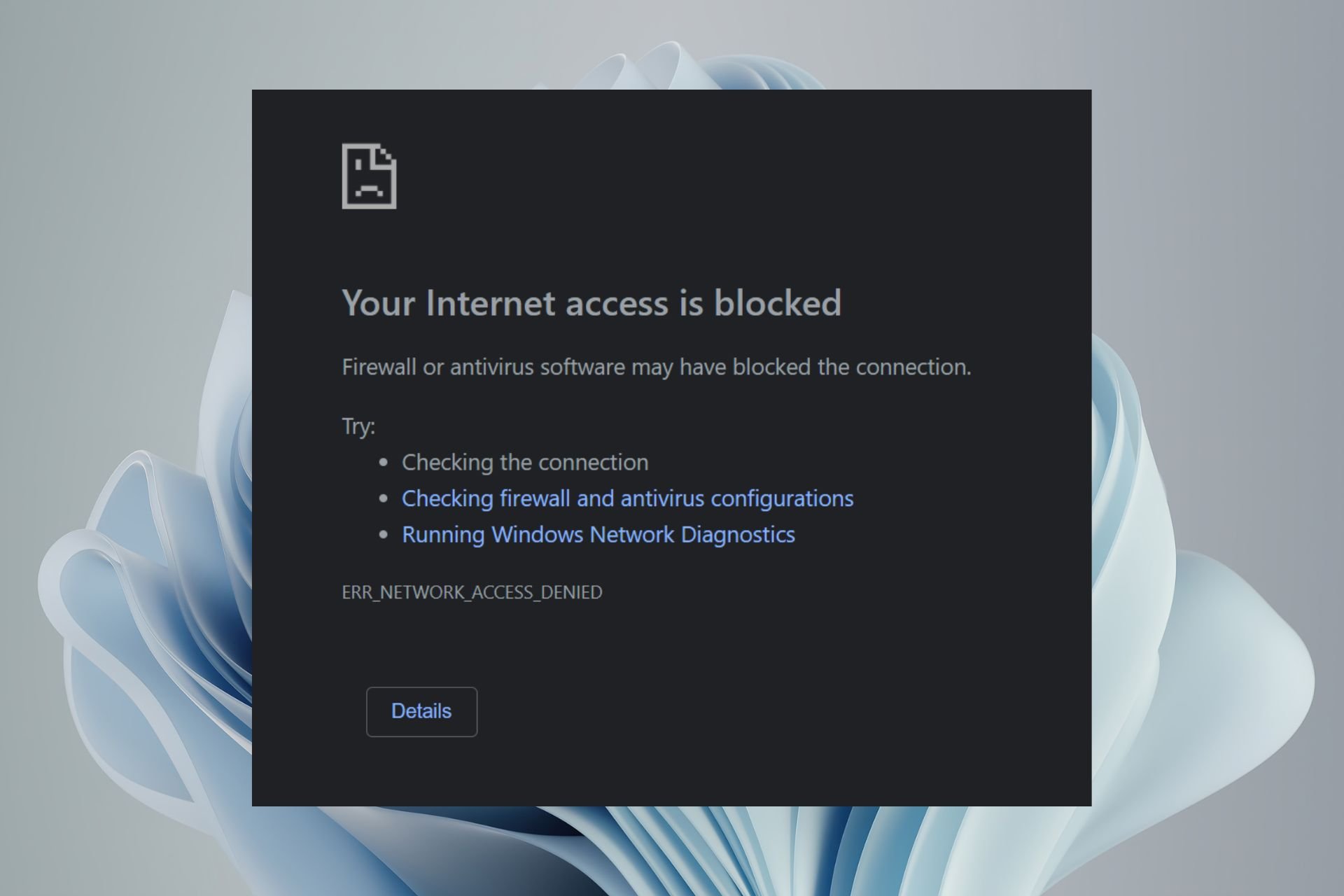
Can You Use a VPN if It’s Blocked?

Your VPN is Blocked by The ISP? How to Unblock it

How to Lower Ping in Rocket League for Seamless Gaming
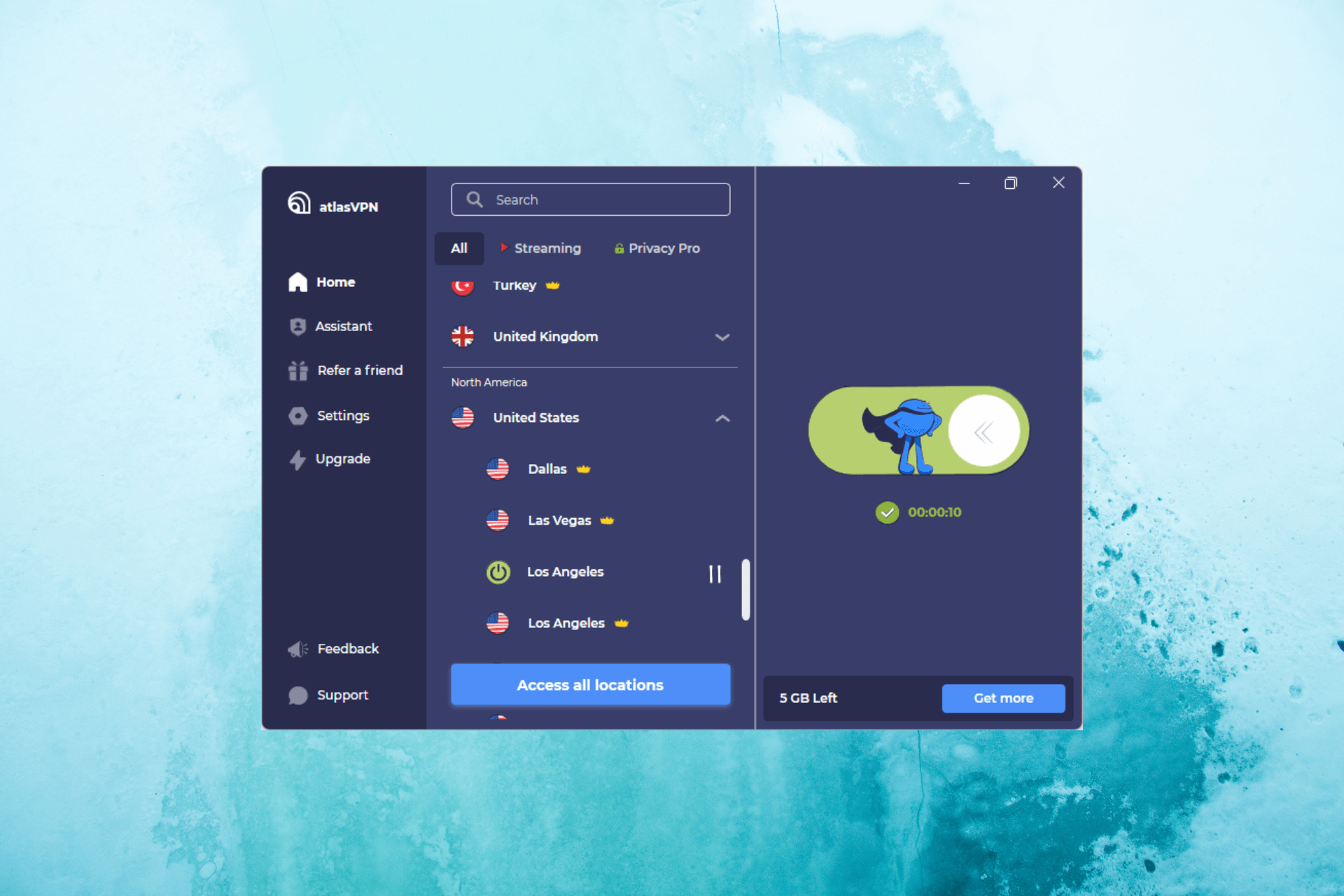
Atlas VPN Keeps your Windows PC Safe From Any Online Threats